The black plague of cloud security
Ransomware is the IT equivalent of the medieval Black Plague. It can easily and quickly destroy a company’s IT environment. Even if the perpetrators offer a “cure,” there is no guarantee it will work. Many companies have looked at the destructive potential of this “disease,” calculated the ROI, and moved their data and applications to a cloud managed services provider (MSP).
Cloud services providers are able to offer enterprise-level security, applications, processes and procedures designed to insulate companies from this type of attack. These tools are cost prohibitive for most businesses to deploy on their own. Ideally, in the event a cloud provider is infected with ransomware, their disaster recovery\business continuity plan should kick in and quickly recover the data with minimal downtime and impact to their customers. However, all clouds are not created or maintained equally. The differences can have a major impact on recovery times and the amount of data lost or stolen.
Major differences exist between cloud providers
Let’s compare two different cloud providers who appear to offer identical managed cloud services for Dynamics ERP applications. While they appear similar in delivery, their backend systems and security architecture are configured differently. The impact ransomware would have on each of these providers respective to infection rate and recovery time will vary.
Provider A deploys a single shared backend environment in which customers use communal components, including Active Directory, application servers, web servers and database servers.
Provider B deploys dedicated virtual backend environments for each customer. In this model, Active Directory, application servers, web servers and database servers are allocated independently to each customer.
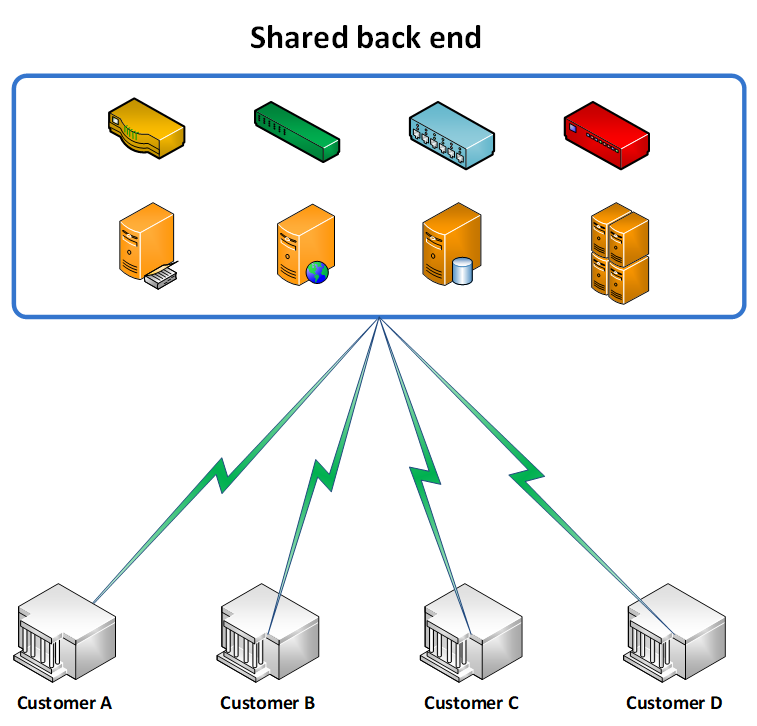
Think of Provider A as a large hospital wardroom in which each patient has their own bed, but only a screen separates one patient from the next.
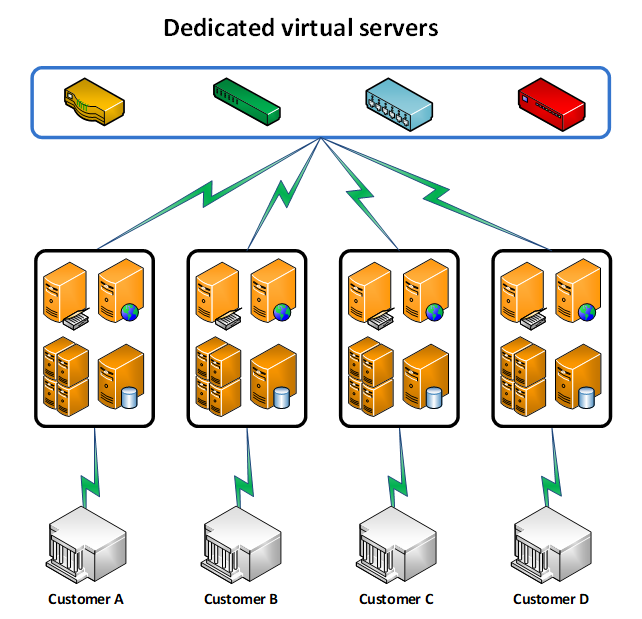
Think of Provider B as a private hospital which assigns each patient to a private room with only one bed in it. Each room in the private hospital requires the staff (administrators) to enter a unique security code in order to enter.
In comparison, a single security code to the hospital wardroom (Provider A) allows access to all patients within that space. If ransomware compromises the security code and gets into that room, all patients become infected.
If the ransomware made its way into one of Provider B’s private rooms, which has its own unique security code, only the single patient within that room will be infected.
The amount of damage ransomware can do is based on the level of access rights it procures. Based on the hospital analogy above, if it has access only to the shared network T drive but not the Z drive, it would only be able to infect (encrypt) files on the T drive. Files on the Z drive would be safe, as it does not have access rights to it.
From a recovery standpoint, both providers need to thoroughly test and verify their DR/BCP plans on a continuous basis. The minimum recommendation is at least once a year.
The time to recover from an infection will vary greatly due to the amount of data affected. Returning to our hospital analogy, it would take a lot longer to clean and disinfect the wardroom with multiple beds and patients than it would to clean and disinfect a single private room with one bed and one patient.
Cost versus security must be factored into the decision
The other factor to consider when comparing MSPs is price. Running applications and storing data in shared environments will cost less than dedicated virtual environments. The balance between security and cost is a never-ending battle. Each customer will need to evaluate potential downtime versus costs when reviewing the type of environment setup they prefer from their cloud services provider.
With heavy customer disclosure requirements around personal, identifiable information (PII), HIPPA, GDPR and PCI, the risks of shared environments often outweigh the potential cost savings. A breach at a cloud provider can have a significant impact on a business’s reputation and sales due to data not being properly secured by the cloud provider.
If you would like to talk with one of RSM’s cloud consultants, please send an email or call 800.274.3978.
By: Andrew Ferraro and Bobbi Kuhlman

 RSMUS.com
RSMUS.com