The United States FBI earlier this month identified the author of the original CryptoLocker malware, a Russian national named Slavik as Evgeniy Mikhailovitch Bogachev . Working with police organizations around the world, they dismantled his network powering the malware. Although his network has been dismantled, the original source code for the Cyptolocker malware was distributed amongst other cyber criminals and has been adapted and re-released.
Cryptolocker works by silently encrypting the files on your network via mapped drives. The decryption key is stored on a server on the attacker’s network. The malware gives little or no indication that encryption is in progress until it is done and then notifies the user with the ransom message. Once the files are encrypted, administrators face the choice of paying the ransom (ranges between $300 and $1000) or restoring their files from backup. According to estimates, the original CryptoLocker had 41% of infected machines pay the ransom in excess of $27 million between October and December of last year.
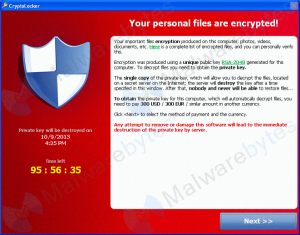
The original CryptoLocker would show a message that looked like this:
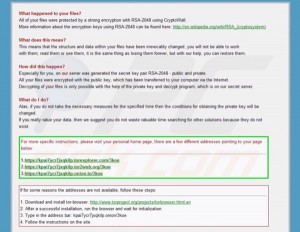
In April, two new variants of Cryptolocker called CryptoWall and CryptoDefense started spreading. They operate in a similar manner to CryptoLocker. These variants put 3 files called DECRYPT_INSTRUCTIONS in the root of each directory it encrypts and shows an HTML page that looks like this:
The malware is spread through a variety of means. Cryptolocker was usually spread through a spoofed email that appeared to come from UPS and contained an infected ZIP attachment. The CryptoWall variant appears to be spreading through an email that is spoofed from the user’s own domain with a subject of You’ve Received a New Fax. The email includes a link to the file sharing website www.cubby.com, which is owned by LogMeIn.com . The file download contains the CryptoWall malware. LogMeIn and Cubby are legitimate cloud-based services that the distributors are exploiting to distribute their malware.
There are no perfect defenses today for this type of malware. The most effective prevention is to avoid becoming infected through education, informing the user base to look out for suspicious emails, and not open attachments they don’t recognize or weren’t expecting. Users should be trained on what the company’s antivirus solutions looks like and provided examples of malware posing as legitimate antivirus.
Administrators must develop a deep, layered, and complicated defense strategy. This takes proper planning and due diligence to avoid unnecessary business interruptions. Internet connections should be protected by firewalls, IPS, and perimeter networks including DMZs for web facing services. Patch management solutions should be utilized to keep all systems up-to-date on vendor patches including workstations and servers alike. These patch management solutions must patch all systems across the board, not just Microsoft Windows updates. Most antivirus scanners do not have signatures so a layered defense is necessary, organizations cannot rely on antivirus alone. Additionally, administrators can tighten security on spam firewalls to block spoofed addresses (this can break web forms on public websites) and increase spam scores (which can result in false positives). Organizations that don’t utilize cloud-based file sharing services can block these sites with web filtering. With proper planning, organizations can utilize Group Policy and restrict applications from running in the user’s Appdata directory, but this requires careful planning as many types of legitimate applications require this feature.
All organizations should have a contingency plan for how they will react if infected. This includes a detailed risk analysis to determine backup strategies – how long can they be down for and how much data can they lose? Plans should be made for offline backups that cannot be targeted by malware. This includes folder redirection for users and reminding users to not save files locally that aren’t backed up. Logging and Event Monitoring tools can be utilized to collect and analyze logs for suspicious behavior, such as marketing user writing data to accounting files that could be a sign of malware.
For more information on defending against ransomware, contact RSM’s technology consulting professionals at 800.274.3978 or email us.

 RSMUS.com
RSMUS.com