Security in Microsoft Dynamics AX 2012 is based on roles where the access is granted to roles and those roles are then assigned to users. Each role consists of a set of duties, each duty comprises of as set of privileges and privilege includes permission.
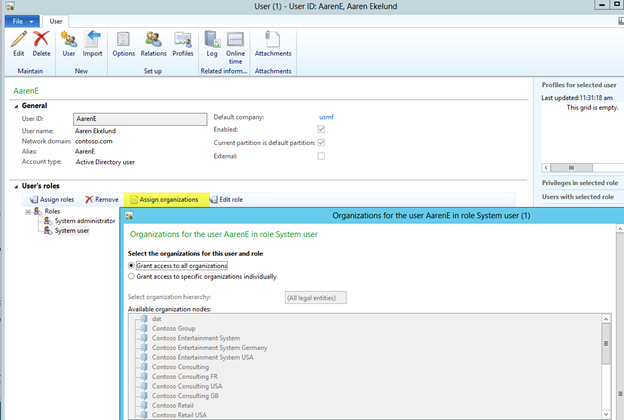
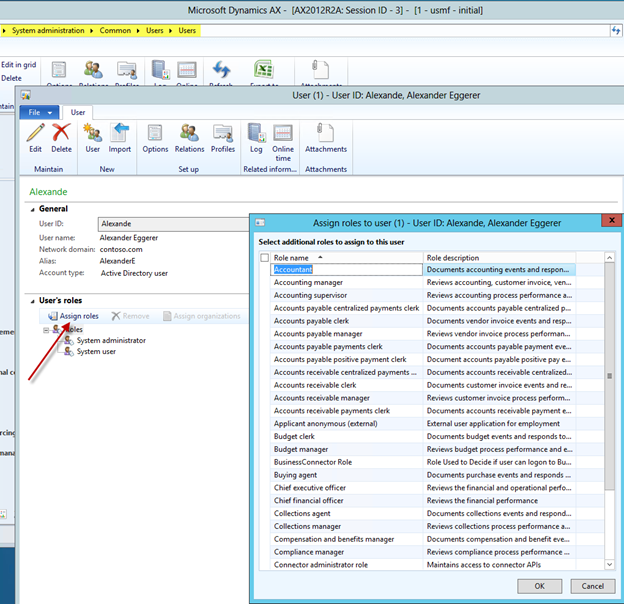
In Dynamics AX 2012, the roles are defined based on the various business processes a typical company might require. These roles vary from Accounts Payable clerk to Chief Executive Manager to Warehouse Manager – each role defining their access points within the system. Roles can be added to a user account within the user setup form: System Administration > Common > Users > Assign Roles
Some things to understand about roles before we get started:
- User roles can be defined for each legal entity or the same roles can be applied to all of the legal entities without manually adding them for all entities.

- Selecting Grant access to all organizations enables this role for all legal entities for that user. If a user only requires a role for a certain entity only, then the Grant access to specific organization individually should be chosen.
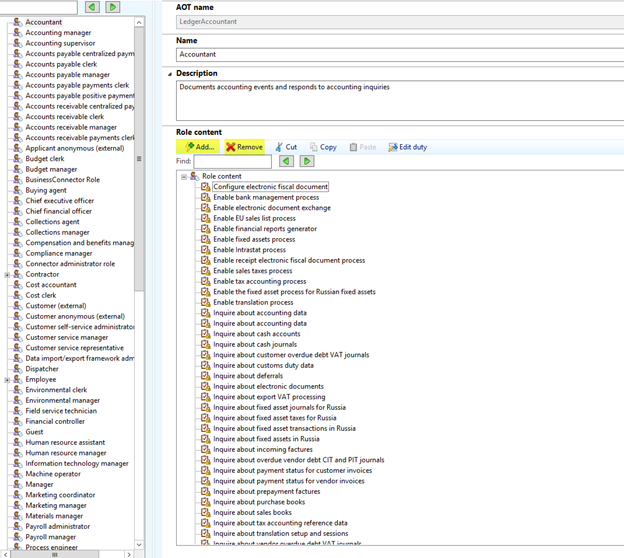
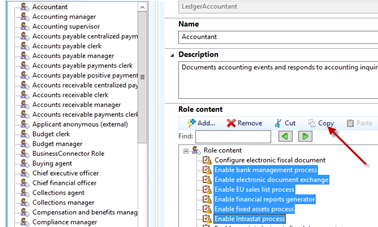
- Each role comprises of a list of duties which signify parts of a certain business process. Dynamics AX 2012 provides a set of duties for each role, however duties can be added or deleted for a particular role.

File Path: System Administration > Setup > Security > Security Roles.
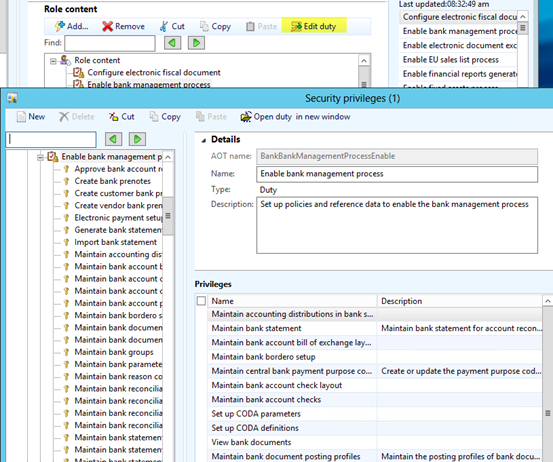
- Each duty consists of a list of Privileges, which permit access to the next layer of user security hierarchy such as posting, submitting and other task related components.
- The duties can be edited from the Security Roles form, by clicking on the Edit Duty button. This will open up the Security Privileges form, which lists outlines all the privileges associated with a specific.

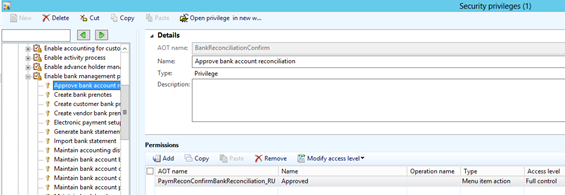
- The left pane displays the Privilege’s names whereas the right pane displays information related to the backend of the application. The permissions area of the form indicates the associated AOT table and the level of access this privilege grants for a duty. The access level can be set to: No Access, View, Edit, Create, Correction and Full Control. Just like other security components, permissions can be added or deleted as required.

As mentioned before, roles can be customized at different layers of the security hierarchy. Roles can be customized by adding/removing duties or adding/removing privileges of a duty or adding/removing permissions of a privilege. The best practice for creating a new customized role is to:
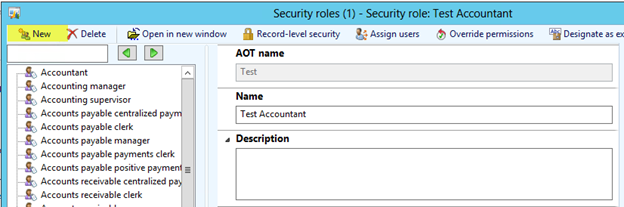
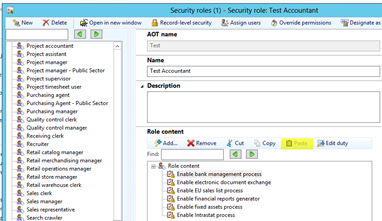
- First create a new role

- Then select a role which best matches the requirements and copy the duties over to the newly created role.

- The new role is added.

If you have questions about Role Based Security in Dynamics AX, please leave a comment below. If you have a Dynamics AX project and need support, RSM is an experienced ERP implementer and proven Microsoft partner serving the Dynamics community for more than 30 years. Contact our professional at erp@rsmus.com or 855.437.7202.
By: Karthik Chadalawada – New Jersey Microsoft Dynamics AX partner

 RSMUS.com
RSMUS.com