OData is a great new feature in GP 2016 which allows you to expose your GP data to any OData compliant application, such as Excel or Power BI, and make it available securely over the internet. Now, let’s take a deeper dive into how you set up security for this data.
Map your GP account
Your first step is going to be to map a GP account to an active directory account. This can be done on the User screen within GP.
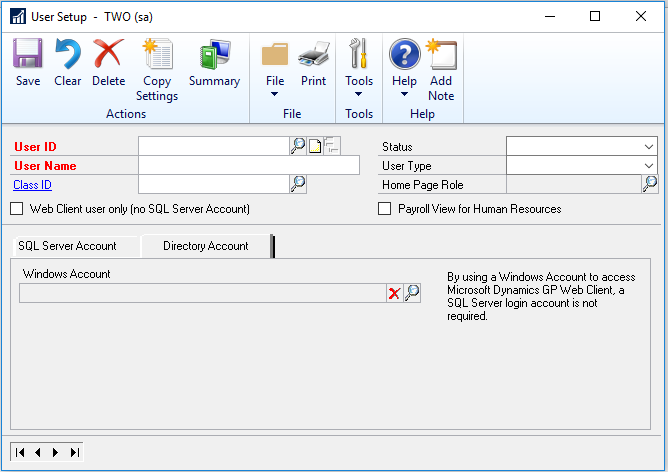
You will notice that there is the tab called Directory Account. Once on that tab, you will need to use the lookup to find the users account in Active directory. This can be done without issue on a normal functioning GP account for the user, no need to create a new and separate account for OData.
Grant Security in OData
The next thing you will need to do is grant security. One of the points behind the implementation of OData in GP 2016 is to make it easier for the front office to manage, meaning that you don’t always need your IT team or consultants to step in for security. Because of that, there are new roles in GP specifically designed for OData. These roles start with “OD_” and generally match up to the roles offered when you first login to GP. If these roles are missing for you, there is likely a script which can be run to create them for you. Once you assign one of these roles to a user which has their active directory account mapped, they should have access to all of the OData objects that are assigned to that role.
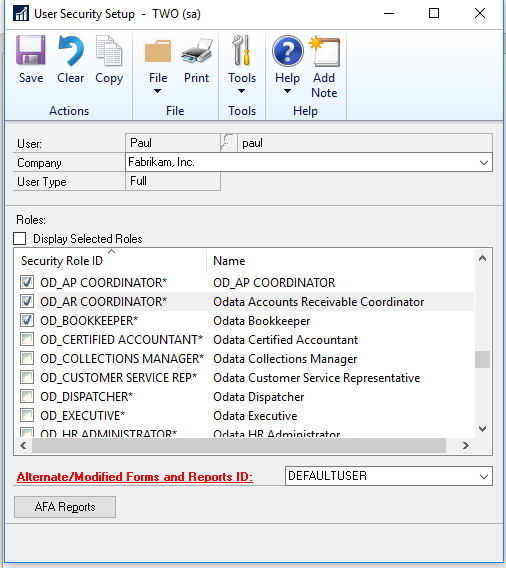
This will allow you to create new Power BI reports in power BI desktop, or pull your GP data into excel, even off of your own network!
Add custom objects to OData roles
You can also add custom SQL objects to the OData roles. If you created a new view, or have a third-party view which you want to access the data from, all you need to do is create a new role in GP for those objects, or add them to an existing OD_ role. This can be done in Security Task setup, and will look like this:
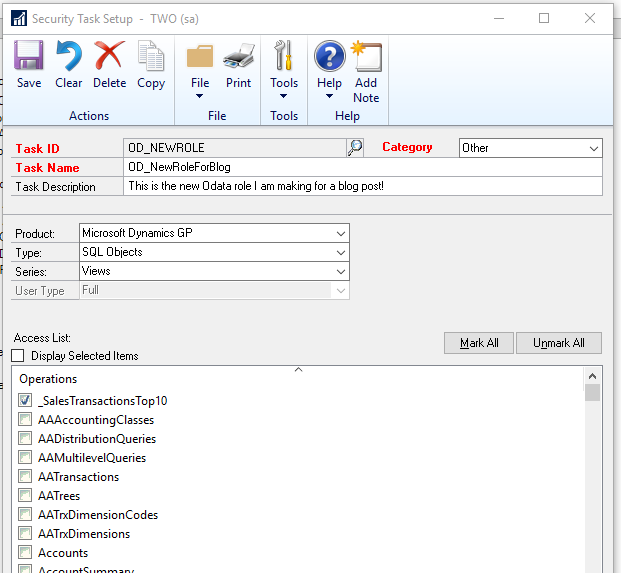
You can see that the product is Microsoft Dynamics GP, and the type is SQL Objects. Under series, there are options for either stored procedures or views, so you can get data from a few different custom objects in SQL. Now just add this task to a role, or create a new one to assign to our users who needs access. This will be fairly easy to manage, just like your regular GP security!
To learn more about how you can take advantage of this and other Dynamics GP features, visit RSM’s Microsoft Dynamics GP resource. To make sure you stay up to date with the Microsoft Dynamics Community, subscribe to our Microsoft Dynamics Community Newsletter.
For more information on Microsoft Dynamics 365, contact us.
By: Paul Newsom

 RSMUS.com
RSMUS.com