Technologies
Discover more on Technologies
The Top 10 Salesforce Spring ’26 Updates That Nonprofits Should Know
The Salesforce Spring ‘26 release is here! To help understand the new features and updates, we’ve combed through the Salesforce Release Notes and listed some of the exciting ones that nonprofits should be...

Linking Your Association Management System With Sage Intacct
Get data from your association management system into Sage Intacct without a headache Member-based organizations must maintain close alignment between...

How Nonprofits Can Prepare Their Data for AI
Nonprofit organizations are increasingly excited about leveraging AI, but many are coming to the realization that AI is only as...

Dynamics GP end‑of‑life: What’s coming — and why now is the time to move
Microsoft’s announcement of Dynamics GP’s end‑of‑life is no longer a distant milestone — it’s a clock that is already ticking....

MuleSoft Agent Fabric: The Foundation for the Agentic Enterprise
MuleSoft Agent Fabric is a centralized platform designed to discover, orchestrate, govern, and observe AI agents across ecosystems, enabling enterprises to manage agent complexity and optimize performance. It offers tools like Agent Registry and real-time workflow tracing to ensure secure, scalable, and intelligent agent operations.
Sage Intacct AI: Close Workspace with Copilot
Our ongoing series exploring how Sage Intacct is integrating AI into its financial management platform now covers one of the...

Enhancing Financial Management for Construction Leaders with Sage Intacct
In the construction industry, challenges like labor shortages, rising costs, regulatory complexities, and pressure on margins are common. Success stories...

AI-Powered AP Automation Now Standard in Sage Intacct for Family Offices
Today’s family offices must contend with rising expectations, increasing competition, and significant economic uncertainty. In response, they’re embracing AI, with...

Enhancing Product Pricing and Order Fulfillment with Salesforce Agentforce Revenue Management
The Importance of Revenue Management Efficient and accurate revenue management is essential for maintaining a competitive edge in today’s fast-paced...

Intelligent Document Processing (IDP): Turning Documents Into Data
Learn how MuleSoft IDP automates extraction of structured data from PDFs, images, and scanned documents, reducing errors and accelerating workflows across your enterprise.

How Behavioral Health Organizations Can Streamline Finances and Operations with Sage Intacct
Behavioral health organizations encounter substantial financial and operational hurdles, including disparate systems, manual processes, and compliance difficulties. These challenges can...

How to Use Salesforce Marketing Cloud Engagement as the Launchpad for AI
AI is rapidly transforming the marketing landscape. Marketers are under intensifying pressure to drive growth and demonstrate tangible impact. Even...

Streamlining Healthcare Finance with NetSuite and AI
In today’s fast-changing healthcare environment, financial operations continue to grow more complex. To keep up, healthcare organizations need to streamline...

How NetSuite Optimization Drives Sales Growth and ROI for Wholesale Distributors
In wholesale distribution, NetSuite CRM optimization often takes a back seat to cost-cutting initiatives such as streamlining operations, reducing overhead,...

Transform the Financial Close with Sage Intacct AI
The close process, whether monthly, quarterly, or annually, remains a major pain point for just about everyone. Even for a...

Sage Intacct AI: Recent Updates and Improvements
We’ve spent the last few months highlighting the AI-driven features being integrated into Sage Intacct. From Sage Copilot, an automated...

Exploring Cloud Firewall Solutions: Azure, AWS and Cisco
Choosing the Right Firewall for Your Environment Firewalls have come a long way from basic packet filtering. In today’s cloud-first...

Sage Intacct: Making AI Accessible for Healthcare Finance
In a dynamic, detail-oriented, and process-driven field like healthcare finance, the potential of artificial intelligence (AI) cannot be overstated. And...

Financial Applications for AI Tools: 3 Compelling Use Cases
Accounting and finance teams have been more enthusiastic about AI than any previous technology. To put that into perspective, in...

Building the Agentic Enterprise with MuleSoft: Dreamforce 2025 Recap
Learn how MuleSoft’s AI-powered tools help organizations streamline integration, reduce manual effort, and improve collaboration across IT and business teams.

Agentforce and AI: Key Dreamforce 2025 Updates for Nonprofits
Salesforce Dreamforce 2025 marked a pivotal moment for the nonprofit sector. With the unveiling of Agentforce 360 and Agentforce Nonprofit, Salesforce...

Inside SuiteWorld 2025: RSM’s Insights on NetSuite’s AI-Driven Future
NetSuite’s annual SuiteWorld conference returned to Las Vegas this October with the bold theme “No Limits” and it certainly delivered....

The Evolution of NetSuite MRP Supply Planning: It’s Time for a Second Look
NetSuite’s Material Requirements Planning (MRP) module has come a long way. What was once viewed as limited has evolved into...

Enhance Family Office Efficiency With the Affiliate Entity Dimension in Sage Intacct
The best solutions make a small change to achieve a big impact. Here’s a prime example: the new affiliate entity...

Breaking down silos: How MuleSoft powers the future of connected enterprises
Powered by MuleSoft, RSM designs and implements a scalable integration solution that unifies Salesforce, NetSuite, third-party logistics providers and proprietary platforms into a single, streamlined ecosystem.

Why Life Sciences Firms Choose RSM Velocity for ERP
Why ERP Matters in Life Sciences The life sciences industry is always moving quickly, and companies need ERP systems that...

How Nonprofits Can Stay Secure on Salesforce
Earlier this year, there were reported cases of malicious attempts to access Salesforce instances through compromised connected apps. As digital...

How to Show Estimated Assembly Costs on NetSuite Work Orders
In manufacturing, knowing the cost of an assembly before production begins is critical. Early visibility into costs supports smarter decision-making,...

Enhancing Business Insights with Sage Intacct’s Interactive Custom Report Writer
In today’s competitive business landscape, leveraging advanced business reporting tools is essential for streamlining operations and making data-driven decisions. Sage...

Why Salesforce Revenue Cloud Is the Future of CPQ and Billing
Salesforce Revenue Cloud Advanced (RCA) transforms the configure, price, quote (CPQ) and billing solutions by offering a unified platform that...

How to Use AI to Enhance Fundraising with Salesforce Nonprofit Cloud
Due to evolving economic conditions and changes in government funding, fundraising has become a significant challenge for nonprofit organizations. As...

Dreamforce 2025: Our Top Session Picks for TMT and Telecom Leaders
Dreamforce 2025 is right around the corner, and with hundreds of sessions on the agenda, it can be tough to...

Harnessing AI to Overcome Nonprofit Challenges Ethically
Nonprofits are increasingly leveraging artificial intelligence (AI) to overcome challenges and enhance their operations and improve service delivery to their...

How to Build a NetSuite Saved Search for Serial and Lot Numbers
Tracking inventory accuracy is critical, especially when working with serialized or lot-numbered items. Businesses often need a quick way to...

Empowering Nonprofits at Dreamforce 2025: Must-Attend Sessions
Dreamforce 2025 is only a few short weeks away. With dozens of sessions for nonprofits, there is a lot to...

The Top Dreamforce Sessions for Industrials – 2025
With so many industrials Dreamforce sessions to choose from this 2025 season, and with Dreamforce just around the corner, how...

Why Senior Living Organizations Are Moving to Sage Intacct: Unlocking Efficiency and Resident-Centered Care
Senior living communities face unique financial and operational challenges. From managing rising staffing costs to consolidating financials across multiple facilities,...

Top 5 Salesforce Winter ’26 Updates Nonprofits Should Know
The Salesforce Winter ‘26 release is around the corner! Salesforce releases new features three times a year, with the Winter...

Optimizing Grant Management and Compliance with Sage Intacct
Effective grant management is crucial for organizations, particularly nonprofits, that depend on external funding. Sage Intacct offers a powerful solution...

Implementing GCC High for Government Contractors
At RSM US LLP, we guide government contractors through the complexities of regulatory environments with a focus on secure cloud...

Unlocking Profitability: NetSuite’s Costed Bill of Materials SuiteApp
When it comes to manufacturing and inventory management in NetSuite, there’s a hidden gem many users overlook: the Costed Bill...

Navigating Federal Policy Shifts: How States Can Prepare for Health & Human Services Transformation
The Changing Landscape of Service Delivery Federal reorganization and evolving administration policies are reshaping how Health & Human Services (HHS)...

Why It’s Time to Move from Dynamics AX to Dynamics 365 Finance & Supply Chain Management
For years, Microsoft Dynamics AX served as a reliable ERP platform for managing finance, operations, and supply chain activities. But...

Modernizing Manufacturing: A Digital Transformation Journey with Microsoft Dynamics 365
In today’s fast-paced industrial landscape, manufacturers face mounting pressure to modernize legacy systems, streamline operations, and empower their workforce with...

From QuickBooks to Sage — Why Contractors Are Making the Switch
QuickBooks is often a contractor’s first step into digital accounting—but as your projects, people, and processes grow, the system that...

3 Challenges of Nonprofit Case Management and How Technology Can Solve Them
Nonprofit case management is a collaborative process to assess, plan, implement, and monitor services. This complex process is not without...

From Goldfish to Gut Health: The Evolution of Functional Snacking
The snacking industry is undergoing a transformation, driven by a growing demand for health-conscious and functional foods. Consumers are no...

Why Purchasing Managers Have the Toughest Job in the Building
In the complex world of supply chain management, purchasing managers challenges’ often place them at the eye of the storm....

Salesforce Grants Management: What Nonprofits Should Know
Salesforce recently announced end-of-sale for Grants Management, meaning the product is no longer available for new purchase. However, existing customers...

Smarter SQL starts here: Expert management with AI-powered insights
Unlock the Full Potential of Your SQL Services No DBA? No problem. You don’t need to hire a full-time database...

Transforming project-based industries: RSM + Microsoft Dynamics 365 for business and professional services and government contracting
Professional services, business services and government contracting firms—spanning architecture, engineering, construction (AEC), legal, accounting, consulting, janitorial, HVAC and federal contracting—face...

Selecting Specific Fields to Include in Mobile Offline Sync in Dynamics 365 Field Service
Feature Specifications Mobile offline synchronization has long been a key feature of Field Service. This new release expands upon that...

Modernizing for a Sustainable Future: How a State Environmental Agency Transformed Its Legacy Systems with Microsoft Solutions
At RSM, we’re proud to help government agencies modernize and better serve their communities through innovative technology solutions. One recent...

Salesforce Agentforce Toronto 2025 Recap
A few weeks ago, I attended Salesforce’s Agentforce World Tour in Toronto and let me just say: AI is no...

Enhancing efficiency and security in family offices through Sage Intacct integration
Family offices are increasingly adopting technology to enhance their operations and service delivery. Managing wealth, assets, and family dynamics has...

AI Is Here—What Nonprofits Can Learn from the Online Giving Era as AI Takes Hold
In the late 1990s and early 2000s, nonprofits faced a digital crossroads. Some embraced online donations early and reaped the...

Customizing NetSuite Dunning with Behavioral Customer Metrics
NetSuite’s Dunning module offers powerful automation for collections, but its native configuration does not support filtering based on behavioral metrics....

Sage Intacct 2025 Release 2 – Enhancements to the Contracts Module
If you currently use the Contracts Module in Sage Intacct or you need a solution to make contract management more...

The ROI of ERP Innovation in Food & Beverage: From Field to Factory
For produce companies, ERP systems like Microsoft Dynamics 365 offer a powerful solution to optimize operations, reduce waste, and increase...

The Future of Food and Beverage Starts with AI
In the food and beverage industry, where seconds matter, margins are tight, and traceability is essential, AI in food and...

Sage Intacct Dashboards for Enhanced Healthcare Decision-Making
Healthcare organizations currently encounter numerous challenges that can hinder their operational efficiency and financial performance. For instance, factors such as...

AI as a Teammate: Can Nonprofits finally be fully staffed?
Artificial Intelligence (AI) is transforming how organizations operate—but the nonprofit sector has a unique opportunity to lead with purpose. While...

Federal HHS priorities offer a roadmap for state and local modernization
At a recent national conference sponsored by RSM, I had the opportunity to hear directly from Federal Health and Human...

What’s Next for Microsoft Dynamics GP?
Key takeaways from RSM’s latest survey With Microsoft ending mainstream support for Dynamics GP by December 31, 2029, and only...

RSM Honorees Earn Microsoft MVP Recognition for Technical Leadership
RSM is proud to celebrate several of our team members who have been recognized with the distinguished Microsoft Most Valuable...

Automatically Add Document to Adobe Sign Agreement in Dynamics CE
I recently implemented the Adobe Sign integration with Dynamics CE and encountered a new use case. I needed to add...

Make the move from foundationConnect to Salesforce Nonprofit Cloud for Grantmaking with RSM
Salesforce is retiring foundationConnect, and now is the time for grantmakers to migrate to Salesforce Nonprofit Cloud for Grantmaking—a more...

From Mission to Maturity: Navigating the Nonprofit Lifecycle with Technology
In the nonprofit world, passion and purpose are the beating heart of every organization. But as these mission-driven entities grow,...

Transforming Manufacturing Customer Service with Dynamics 365 Contact Center
In the industrial manufacturing sector, handling customer service requests like spare parts inquiries, warranty claims, and product specifications requires speed,...

Sage Intacct 2025 R2 Updates: AI, Automation, and Smarter Workflows Take Center Stage
The Sage Intacct 2025 R2 updates introduce a powerful lineup of enhancements that improve automation, streamline reconciliation, and provide deeper...

What’s New in Sage Intacct Construction: 2025 R2 Update
Sage continues to evolve its cloud financial management platform to meet the complex demands of the construction industry. The 2025...

Boost Efficiency and Make Life Easier in Sage Intacct: Tips From the Trenches
Let’s face it—Sage Intacct is a powerful financial management platform, but even the most seasoned users can benefit from a...

Ensuring Compliance: Best Practices for Releasing Restricted Funds in Sage Intacct
Whether you’re a nonprofit executive stewarding donor trust, or a financial systems user managing day-to-day accounting in Sage Intacct, restricted...

Sage Future 2025: Transforming Finance with Trustworthy AI and High-Performance Innovation
Sage Future 2025 brought together finance leaders, technologists, and industry innovators to explore what’s next in intelligent financial management. The...
Merging Mountains: Successful Org Merges in Salesforce
Org merges. Just the phrase can send shivers down the spine of even the most seasoned Salesforce admin. It’s a...

Why Businesses Are Moving from Microsoft Dynamics NAV to Dynamics 365 Business Central
As businesses continue to grow and adapt to new digital demands, many are reevaluating their legacy ERP systems. One of...

Maximize Field Service Efficiency with Resource Scheduling Optimization
As organizations scale their Field Service operations and manage high volumes of complex work orders, scheduling can become a significant...

Reimagining Business & Professional Services: How RSM and One Microsoft Are Powering the Next Wave of Industry Transformation
The Business & Professional Services (BPS) industry is at a critical inflection point. The BPS industry encompasses a wide range...

Don’t Stop at Go-Live: Power Your BlackLine Invoice-to-Cash (I2C) Success Every Step of the Way
For many companies, going live with BlackLine I2C is only the beginning. The real challenge starts after the implementation—when internal teams are expected to maintain, support, and optimize a sophisticated invoice-to-cash platform without the benefit of specialized expertise. RSM US LLP provides ongoing support to support efficiency, business continuity, optimization and strategic growth.

5 Clear Signs Your Construction Company Has Outgrown QuickBooks
QuickBooks is a reliable entry-level accounting tool, especially for smaller construction businesses. But as your company scales—with more jobs, entities,...

Sage Intacct’s AI Solutions: Employee Expense Automation
Welcome back to our ongoing series about the AI-driven solutions being added to Sage Intacct. We’ve previously covered general ledger...

Using Internal IDs and External IDs in NetSuite
In NetSuite, each record is uniquely identified by the record type with either an external ID or internal ID. The...

Conversational AI in Retail: Microsoft Copilot as the New Sales Assistant
Meeting the Modern Retail Customer Where They Are Today’s retail shoppers want more than just products—they expect instant answers, personalized...

Now Available: RSM Velocity, Our Rapid NetSuite Implementation Package
Go live in just six weeks—with a streamlined approach built for speed, efficiency, and confidence. NetSuite is a powerful platform...

Build 2025: Three Ways AI Just Got Real for Business
Microsoft Build 2025 felt less like a conference and more like opening the door to tomorrow’s workplace, one where AI...

Sage Intacct: Ideal for Nonprofit Healthcare Organizations
Why Sage Intacct is the Perfect Fit for Nonprofit Healthcare Organizations? Nonprofit healthcare organizations operate at the intersection of two...

NetSuite Shipping Capabilities and the Gap in Multi-Order Consolidation
NetSuite provides shipping integration with major carriers like FedEx, UPS, and DHL, allowing businesses to generate shipping labels and tracking...

Using AI to Tackle Quality Risks and Streamline Recalls
Introduction: Why AI is the Future of Quality Control Reducing quality risks with AI is now a strategic priority for...

Invoice-to-Cash: Enhancing Customer Satisfaction Through Automation
We delve into how automating the Invoice-to-Cash (I2C) process can significantly boost customer satisfaction.

Is It Time for NetSuite MultiBook Accounting? A Practical Guide to Use Cases and Implementation
For companies using NetSuite, the idea of enabling MultiBook Accounting can sound like an elegant solution to complex reporting requirements....

All Roads Lead to San Francisco: Why Dreamforce 2025 Should Be on Your Radar
This blog updated was on Friday, August 21, 2025 to update pricing status. Dust off your trail badges and start...

Navigating the Future with RSM’s AI Framework
AI Strategy: Laying the Groundwork for Success Artificial intelligence (AI) has become a cornerstone for businesses aiming to enhance productivity,...

The Manufacturer’s Guide to IoT Cybersecurity
Why Secure IoT Matters in Manufacturing As manufacturers continue to adopt digital technologies, the need to secure IoT in manufacturing...

WhatsApp and Dynamics 365 Contact Center: What to Know
Microsoft has recently announced the availability of WhatsApp channel support in its Dynamics 365 Contact Center, powered by Azure Communication Services...

Sage Intacct’s AI Solutions: General Ledger Outlier Detection
Welcome to our ongoing series exploring the ways that Sage Intacct—a cloud-based financial management solution with a robust toolkit for...

Sage Intacct’s AI Solutions: Sage Copilot
With so many interesting, exciting, and innovative AI-driven capabilities coming to Sage Intacct, we created a series highlighting them all....

The Rise of Virtual Card Payments: Transforming Invoice-to-Cash Processes
According to a study by Juniper Research, the total volume of virtual card transactions is projected to reach 175 billion by 2028, a significant increase from 36 billion transactions in 2023. This anticipated surge will have a profound impact on the Accounts Payable and Accounts Receivable departments.

How to Store Unstored Fields in NetSuite Using Workflows
In NetSuite, custom fields based on saved search values are often “unstored,” meaning their values update dynamically. While this is...

Transform Project Success with NetSuite
In today’s fast-paced business world, successful project delivery requires seamless alignment between project management, finance, and HR systems. That’s where...

Future-Proofing Manufacturing with Azure IoT
In today’s manufacturing environment, minimizing downtime and maximizing efficiency are essential. Unplanned disruptions can be costly, which is why more...

Embrace the Future: Migrating from Process Builders and Workflows with RSM
Why Read This Blog? You may have heard about the end of support for Process Builders and Workflows and transition...

Automating Expiration Status Updates in NetSuite
Safeguarding Quality and Compliance for Perishables This is a scripted customization. To discuss implementing it in your NetSuite environment, reach...

NetSuite Nonprofit Financial Statements – Net Assets
The Social Impact edition of NetSuite comes with pre-built Nonprofit Financial Statements, including Statement of Financial Position, Statement of Activity,...

Strategies to Boost Sustainability with Azure Digital Twins
The Push Toward Greener Operations Environmental regulations, consumer demand for eco-friendly products, and a global movement toward net-zero carbon emissions...

How to Use NetSuite Price Levels for Tariff Management
Why Pricing Flexibility Matters Pricing flexibility is more critical than ever as businesses navigate tariff increases and market volatility. NetSuite’s...

Field Service USA Palm Springs 2025: A decade in review
As a decade-long attendee of Field Service USA, it has been remarkable to witness both the evolution of the event...

Achieving Government Contracting Success with RSM’s Unique F&SC Solutions
In the ever-evolving regulatory landscape of government contracting, achieving compliance and operational efficiency is paramount. RSM US LLP, a leading...

Top ServiceNow Knowledge 2025 Sessions for Tech Leaders and Developers
With ServiceNow Knowledge 2025 quickly approaching, it’s time to lock in your agenda. Whether you’re a CTO focused on enterprise...

10 Lessons From 25 Years of ERP Implementation
With over 25 years of experience in ERP implementations—primarily on the client side—I’ve gained invaluable insights. Now, after spending years...

Unlocking Value Creation with Sage Intacct: A Digital Evolution for Private Equity
In today’s fast-paced private equity landscape, technology is more than just an operational necessity—it’s a strategic enabler. Outdated systems and...

Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator (Pt. 6)
As government agencies work to meet the growing demands of Medicaid and Health and Human Services (HHS) programs, the release...

Value and Accountability: A Look Inside Azure FinOps
You don’t need to be a cloud expert to understand how much cloud costs. It’s right there on your credit...

Call in a Click! Enabling Teams Click-to-Call
Did you know that Microsoft Teams Phone Numbers can be used to make calls from any device with Teams accessibility?...

NetSuite Bill Capture Enhancements 2025.1
NetSuite has recently released in 2025.1 new features preview for NetSuite Bill Capture. These features enhance functionality around the vendors,...

The Age of Automated Accounts Receivable
Digital transformation in accounts receivable (AR) processes is becoming a critical factor for businesses in a highly competitive market

Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator (Pt. 5)
At RSM, we understand the immense pressure that government service agencies face in delivering effective, person-centered care. From complex service coordination to...

Cloud vs. Traditional Software in Construction
The construction industry has been slow to embrace technology in the past, so it’s not surprising that cloud adoption also...

Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator (Pt. 4)
RSM understands that states are often tasked with doing more with less while navigating complex challenges in delivering critical services....

Creating a Virtual Replica: The Role of Azure Digital Twins in Smart Factory Development
OverviewIn today’s rapidly evolving manufacturing landscape, smart factories have become game-changers. They help businesses optimize processes and boost productivity. One...

Transaction Line Distribution SuiteApp
SuiteApp Overview The Transaction Line Distribution SuiteApp is designed to manage and automate the allocation of both purchase and sales...

Suite Tax Benefit and Setup
After reading this article, you will have a better understanding in terms of what SuiteTax can do and how to...

Spring Into Innovation: RSM’s Food & Beverage Newsletter [Spring 2025]
As the seasons change, so does the food and beverage industry! From groundbreaking trends in natural and sustainable products to...

Integrating the Investment Book Effortless for Family Offices with Sage Intacct
In the past, financial management and general accounting at family offices involved seemingly endless amounts of data management, where professionals...

Project Management & Accounting in Microsoft Dynamics 365 F&SC
Project Management & Accounting in Microsoft Dynamics 365 F&SC is a powerful tool that can be used to manage a...

Fabric Copilot is now available for all SKUs!
Copilot in Microsoft Fabric is an AI-powered assistant designed to enhance the workflows of data professionals within the Fabric platform....

Accelerate your journey to Fabric with the new Fabric Migration Tool!
Microsoft Fabric continues to evolve, and so do the possibilities of what you can accomplish within it. With all the...

Billing Operations – Best Practices
What are Billing Operations, and Why Do They Matter? NetSuite can streamline and automate an organization’s billing process by managing...

Utilizing NetSuite Workflows to Auto-Populate Fields based on Transaction Dates
Understanding the Flexibility of NetSuite workflows NetSuite workflows offer exceptional flexibility, enabling businesses to tailor their processes according to their...

Allocation Schedules in Healthcare with NetSuite
NetSuite & Healthcare Accounting in Healthcare comes with its own complexities and extensive requirements for any company situated within the...

Maximizing Efficiency with Merchandise Hierarchy
What is Merchandise Hierarchy? A well-structured merchandise hierarchy is a crucial tool for retailers, offering a clear system for organizing...

Lot Allocation Management Accelerator (LAMA) Benefits: Creation and Reversal
Last year, I had the pleasure of assisting in the creation and testing of a RSM’s Lot Allocation Management Accelerator...

BEWARE: Windows 10 EOL is Approaching!
On October 14th, 2025, Windows 10 will reach end of life support, meaning no additional quality or security updates will...

Spring ‘26 Transition from Profiles to Permission Sets, Are You Ready?
In 2023, Salesforce announced the planned retirement of permissions on Profiles. However, in 2024, they declared they were no longer...

NetSuite System Management Best Practices
Effectively managing your NetSuite environment is important for ensuring optimal user performance, data security, and scalability for your business operations....

Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator (Pt. 3)
Government agencies face a growing list of regulatory requirements, particularly within Medicaid and Health and Human Services (HHS) programs. The...

Delivering a Seamless Network & Security Experience with SASE
As remote and hybrid models become the more popular model in the modern workforce, IT environments have needed to evolve...

Leveraging AI: The Risks of Oversharing and How to Handle Them Like a Pro
Originally posted to MaddyDahl.com. With tailored recommendations, task automation, and precise analytics, workplace productivity is truly being reimagined by AI....

EFT Processing for Sage Intacct
Society is embracing the move to electronic payments While payment by check remains common in the U.S., the momentum towards...

Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator
Government agencies face an ever-changing landscape of complex regulatory requirements, particularly within Medicaid and Health and Human Services (HHS) programs....

Configuring SAML SSO 2.0 within NetSuite
There are several reasons why an organization would want their NetSuite users to be protected through SAML SSO, or Security...

Blog Series: Navigating the CMS Access Rule with RSM’s Case Management Accelerator
Welcome to the first installment of our weekly series exploring the CMS Access Rule and its impact on Health and...

Navigating Tariff Changes with NetSuite’s Landed Cost Functionality
In today’s global trade environment, tariffs are constantly evolving, impacting businesses of all sizes. With shifting trade agreements, new tariff...

NetSuite New Release Upgrade Best Practices
In Q1 and Q3 of each year, NetSuite comes out with a new release upgrade, which consists of new features,...

NetSuite 2024.2 & 2025.1 News Release: Key Updates for Life Sciences
Stay ahead in the Life Sciences industry with the latest NetSuite updates! Discover how the new Bill Capture Enhancement, SuiteProcurement...

Automate External Revenue Management in Sage Intacct
Automate Revenue Management from External Billing Systems in Sage Intacct Sage Intacct has a substantial list of features and functions,...

Smart Manufacturing: Harnessing the Power of Azure Digital Twins and IoT for Real-time Operational Insights
In today’s rapidly evolving manufacturing landscape, staying ahead of the competition requires more than just optimizing traditional processes. Manufacturers are...

Mastering Resource Allocation for Project Success
Efficient resource allocation is critical for delivering projects on time and within budget. It involves strategically assigning people and assets...

Barely Survived Year-End Inventory? Here’s How to Make It Easier Next Time
If you’ve just wrapped up another exhausting year-end physical inventory, you’re probably thinking, “There has to be a better way.”...

Modernizing Beverage Distribution with Microsoft Dynamics F&SC [Case Study]
A leading beverage distribution company has embarked on a digital transformation journey by implementing Microsoft Dynamics F&SC. This initiative underscores...

Upcoming Nonprofit Events: Insights, Innovation, and Impact
Nonprofit organizations constantly adapt to new challenges, from leveraging technology for greater efficiency to strengthening cybersecurity and donor engagement. At...

Reducing Downtime and Increasing Customer Satisfaction with Dynamics 365 CE
In the service industry, machine downtime is an important metric that directly impacts operational efficiency and customer satisfaction. Dynamics 365...

The Importance of Designing and Building a Robust Quote-to-Cash Process
The quote-to-cash (QTC) process encompasses everything from generating the initial quote to receiving payment (similarly, lead-to-cash (LTC) represents a larger...

Scaling AI Across Manufacturing with Copilot: From Pilot Projects to Enterprise-Wide Adoption
As a Business Applications Consultant at RSM, I’ve seen firsthand how manufacturing organizations worldwide are unlocking the potential of generative...

First Impressions of Microsoft Sustainability Data Solutions in Fabric
Microsoft Fabric, a unified analytics platform, has garnered significant attention in the sustainability space for its promise to streamline data-driven...

Do You Really Need Backup for Microsoft 365?
Microsoft 365 (M365) has become indispensable for modern organizations—powering collaboration, productivity, and communication in real time. It’s easy to assume...

Unlocking Efficiency in Senior Living Operations With Sage Intacct
Senior living communities have arrived at a long-awaited inflection point. The oldest members of the Baby Boomer generation will turn...

The Top 4 Reasons to Utilize Dynamics 365’s Contact Center
In an increasingly digital-first world, delivering exceptional customer experiences demands more than responsiveness— it requires tools that foster engagement, empowerment,...

Leveraging Power Platform for a seamless vendor onboarding experience
Streamlining Vendor Onboarding with Microsoft Power Platform For professional services firms, vendor onboarding is more than just a routine administrative...

The Top 5 Things to Know in Government Contracting This Week – February 17th, 2025
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

How Dimension Relationships Elevate Family Office Accounting
The family office ecosystem has grown significantly in recent years as new offices open and more wealth flows to these...

Automate Receivables with RSM’s Dunning Letters Solution
Overview: Despite persistent reminders, are you still struggling to collect customer payments? Do you wish you had better insights into...

Reducing costs while reducing Greenhouse Gas emissions using Microsoft solutions
There are several reasons to calculate your company’s greenhouse gas emissions, including compliance with direct or indirect regulations, reducing operating...

Finding the Microsoft Solution for Your Nonprofit’s Needs
Nonprofit organizations put the needs of others above their own, working towards a mission of betterment, be it their communities,...

Reporting Options with Microsoft Business Central for Nonprofit Organizations
Nonprofit organizations have different financial reporting goals than their for-profit counterparts. While for-profits tend to focus on maximizing net income...

Dimensions and Not for Profits
The Dimension functionality in Microsoft Dynamics 365 Business Central software enables Not For Profit (NFP) companies to streamline their operations...

Automate AP With Sage Intacct’s EFT Payment Manager
A survey of finance leaders contains some eye-opening insights about the accounts payable (AP) process. Vendors ranked the speed of...

Controlling Employee Access Through Custom Forms in NetSuite
An important consideration for controls is the ability to limit user roles and access. As most NetSuite users know, each...

Accelerating ERP Deployment in Manufacturing with RSM’s ScaleFast: Reducing Time and Risk
In today’s fast-paced manufacturing landscape, businesses need modern, integrated solutions to scale efficiently, enhanced financial controls, and streamlined operations. Yet,...

How to Manually Pair Intercompany Transaction
Managing intercompany transaction is a crucial aspect of accounting for businesses with multiple subsidiaries. NetSuite intercompany development framework offer a...

Transforming Manufacturing and Distribution Operations with Dynamics 365 Copilots
The integration of AI-powered co-pilots into Dynamics 365 marks a significant advancement in industrial and business operations. These sophisticated systems...

Distinguishing Excellence: Qualities of Exceptional Implementation Consultants
Software implementation consultants play a critical role in assisting companies with integrating new software systems into their operations. Their work...

Maximizing ERP Success: How to Choose the Right Consulting Partner
When selecting a partner for your ERP software implementation, several key factors should be carefully considered to ensure the project’s...

Top GovTech Trends in 2025 & How RSM is Helping State & Local Governments Prepare
As technology evolves, state and local governments are embracing new digital solutions to improve efficiency, enhance citizen services, and strengthen...

Germany E-Invoicing- NetSuite SuiteApp Features and Functionality
Electronic invoicing (e-invoicing) refers to the exchange of invoice documents between businesses, their partners, and tax authorities in a structured...

Fundraise Fluently With Sage Intacct + DonorPerfect
Nonprofits must hold themselves to a higher standard in an increasingly competitive funding climate. Providing donors with a seamless and...

The Top 5 Things to Know in Government Contracting This Week – February 3rd, 2025
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

A Beginner’s Guide to Navigating in NetSuite
A Beginner’s Guide to Navigating in NetSuite To new users, navigating in NetSuite might seem like a daunting task. There...

1099 Reporting Process in NetSuite
What is Form 1099 and Why Does it Matter? Form 1099 is used to report any non-employment income to the...

Maximizing Efficiency and ROI in AI Initiatives: A Guide to Cost Optimization
Artificial Intelligence (AI) is transforming industries, unlocking new opportunities for innovation, automation, and enhanced customer experiences. However, the financial investment...

Accounts receivables automation with HighRadius + RSM: A game changer
HighRadius offers a suite of products designed to revolutionize the accounts receivables process. By leveraging HighRadius, clients can significantly enhance their accounts receivables process, leading to improved cash flow, reduced risk of bad debts, and more efficient operations.

Meeting CA 253/261 requirements using Microsoft Cloud for Sustainability
There are several reasons for your company to prioritize sustainability—whether it’s to enhance brand reputation, identify cost-reduction opportunities, or comply...

Advanced PDF Version Histories
This blog will provide users with the knowledge to locate advanced PDF version histories. This will allow someone to revert the...

Streamline Approval Processes with Change Requests in NetSuite
Clients can have very specific approval processes for different record types in NetSuite. Item records, transaction records, and entity records...

The Top 5 Things to Know in GovCon This Week – January 13th, 2024
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

The Top 5 Things to Know in GovCon This Week – January 6th, 2024
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...
Microsoft’s Cloud for Sustainability – new solution for Business Central
Starting in 2025, several rules will require businesses to report their activities that create greenhouse gas emissions. Initially, large companies...

Tax Tips: File 1099s with Sage Intacct + TaxBandits
The deadline for filing 1099 tax documents for independent contracts has almost arrived. You need to submit all documents...
Azure Virtual Desktop vs Windows 365: Which Is Right for You?
Aren’t these virtual desktop solutions essentially the same? Not quite! Join us as we dive into the features and key...

Dynamics 365 FSC Implementation: A Catalyst for Change [Case Study]
Background A leading manufacturer in the consumer goods industry, serving approximately 82,000 customer locations across the U.S., decided to embark...
Revolutionizing Manufacturing: From Predictive Maintenance to Proactive Optimization with Azure Digital Twins and IoT
In today’s competitive manufacturing landscape, minimizing downtime and maximizing productivity are essential for success. Azure Digital Twins and the Internet...

Nonprofit Budgeting Made Better: Martus + Sage Intacct
Nonprofit budgeting is a big responsibility…and a big risk. Every year, nonprofits spend time and energy building their budget, usually...

Maximizing value with BlackLine: RSM’s key takeaways from BeyondTheBlack 2024
As businesses evolve, finance transformation is not merely about implementing technology. Finance transformation is all about driving a mindset shift that enables sustainable growth and efficiency. This is a recap of key takeaways from the conference and actionable steps to focus on moving forward.

Alteryx 2024.2 update highlights
The latest Alteryx enhancements will save you and your clients time so they can get more done in their day. This blog post will provide highlights on the latest and greatest features in Alteryx designer and server 2024.2.

The Top 5 Things to Know in GovCon This Week – December 16th, 2024
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...
Billing Operations – Best Practices
What are Billing Operations, and Why Do They Matter? NetSuite can streamline and automate an organization’s billing process by managing...
A Guide to Inventory Statuses
The Inventory Status feature is a core function of NetSuite that allows you to associate attributes to items to drive...

Multi-Currency Delegation Approval Workflow
Overview Recently, I was a part of a Consumer products implementation, specifically focusing on the Procure to Pay side of...
Key Takeaways from Microsoft Ignite 2024
“Originally posted to https://maddydahl.com/key-takeaways-from-microsoft-ignite-2024/” Even with Copilot, I have stared far too long at the blank white word document with the...
![RSM’s Microsoft Food & Beverage Newsletter [Winter 2024]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v1_green.png)
RSM’s Microsoft Food & Beverage Newsletter [Winter 2024]
As the temperatures drop and winter sets in, the RSM food and beverage team is celebrating a season filled with...

Unlocking Efficiency: What’s New in NetSuite 2024.2 for Manufacturing, Supply Chain, and Distribution
NetSuite 2024.2 brings plenty of updates and excitement in area of supply chain, manufacturing, and distribution industry. The focus of...

Malaysia E-Invoicing- NetSuite SuiteApp Features and Functionality
For NetSuite users operating in Malaysia, the Malaysia e-Invoicing SuiteApp provides a solution to address tax-regulation changes while streamlining invoicing processes.

The Top 5 Things to Know in GovCon this Week – December 2nd, 2024
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...
Salto to NetSuite Integration for Cutover
Understanding the capability of Salto Salto is an automated configuration management tool for enterprise resource planning (ERP) software solutions. Salto...
Top 5 Reasons Healthcare Organizations Choose Sage Intacct
Top 5 Reasons Healthcare Organizations Choose Sage Intacct In healthcare, what distinguishes the adequate financial management software from the exceptional?...

Modernizing Small Business Finance With Sage Intacct
For the largest and most successful businesses, financial management is a key strength driving their competitive advantage. For many...
Ensuring Transaction Integrity with Status Validation in NetSuite: Enhancing Inventory Management for Diverse Industries
This is a scripted customization. For more information on implementing it into your NetSuite instance, contact a member of the...
Case Study: Modernizing Property Assessments with Microsoft Dynamics
In the ever-evolving landscape of public service, organizations responsible for managing property assessments face significant challenges. Manual processes, limited data...

The Top 5 Things to Know in GovCon this Week – November 18th, 2024
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

How canvas apps can be leveraged in the BPS industry
Canvas apps offer a significant level of customization, allowing them to be tailored precisely to meet the unique needs of...

Revolutionizing Customer Support with Microsoft Copilot: A New Era for Service Teams
In today’s fast-paced world, customer expectations are higher than ever. Service representatives are grappling with mounting workloads, an increasing number...

Unlocking Growth: How Sage Intacct’s Partial Ownership Consolidation Empowers Financial Services and Retail Chains
Financial services firms and retail chains, while different in many ways, have something unique in common: complex ownership structures. In...

Transform your accounting firm with NetSuite
Looking to elevate your accounting firm’s efficiency and growth? Join us on Thursday, December 12 at 2 p.m. EST for...

Quarterly Business Reviews and OKRs
Driving Business Impact in Managed IT Services I’ve been working in the managed IT services field for the last 25...

How to Set Up Inventory Adjustment Reason Codes in NetSuite
When companies manage their inventory in NetSuite, there are times when it is misstated due to miscounts, inventory spoilages, theft,...
How data analytics is transforming the manufacturing industry
In today’s fast-paced world, manufacturing companies face a myriad of challenges, from increasing competition and market shifts to supply chain...
Top 5 Data Challenges Facing Manufacturing Companies (and How to Solve Them)
The manufacturing sector is increasingly relying on data to drive efficiency, optimize processes and gain a competitive edge. However, while...

Case Study: Transforming Project Investment Lifecycle Management with GEMS 2.0
Project Overview: In May 2022, a government project management team developed and launched GEMS 2.0, a next-generation investment lifecycle case...

Modern Family Office: Automate Ownership Consolidations
Modern Family Office: Automate Ownership Consolidations Family offices must maintain a careful balance between accuracy and efficiency. At the same...

Case Study: Modernizing Municipal Operations with a Unified Microsoft Platform Solution
Client Overview A city in Eastern Ontario, Canada, sought to modernize its back-office finance, supply chain, and human capital management...
Managing Project Budgets in Dynamics 365 Project Operations
In a project, each phase, task, or work package incurs costs as labor, materials, and expenses. A project budget represents...

NetSuite Backup of Financial Records in India – Recommended Approaches to Comply with Recent Changes in Regulation
Introduction In today’s digital age, the importance of data integrity, availability and security are critical for business. For Indian companies...

Correcting a Project Invoice in Dynamics 365 Project Operations
A project invoice in Dynamics 365 Project Operations is a document that details the billing for work performed on a...

Case Study: Public Health Department Implements RSM’s D365 CE Disease Surveillance System
Client Overview: A large public health department, with an annual budget exceeding $70 million and over 900 staff members, serves...

How Sage Intacct’s Inventory Module Transforms Inventory Management
Unlocking Efficiency in Healthcare: How Sage Intacct’s Inventory Module Transforms Inventory Management For healthcare providers, inventory management isn’t just about...

Protected: Enhancing Inventory Visibility with Custom Measures in D365
There is no excerpt because this is a protected post.

Key Features and Benefits of Salesforce Field Service
Salesforce Field Service is a key application in the Salesforce platform that helps organizations modernize their field operations. For companies...
Live webcast: Accelerate your firm with NetSuite and Filevine
We’re excited to invite you to an exclusive live event on November 11, 2024, from 1-2 PM EST, where you’ll...
The End Is Near!
What Windows 10 End of Life means to your organization. The end of Windows 10 is upon us! Today marks...

Reaffirming Our Commitment to Dynamics GP Customers
At RSM, we understand the concerns surrounding Microsoft Dynamics GP as it approaches the end of mainstream support. We want...
![Implementing Business Central for a Dairy Processing Facility [Case Study]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v1_grey.png)
Implementing Business Central for a Dairy Processing Facility [Case Study]
The Challenge A dairy processing company that produces a range of high-quality milk ingredients such as powders, protein concentrates, and...
![Transforming a Craft Brewery’s Digital Operations with Business Central [Case Study]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v1_grey.png)
Transforming a Craft Brewery’s Digital Operations with Business Central [Case Study]
The Challenge A prominent craft brewery faced operational and technical challenges as it prepared to sunset its existing Microsoft Great...

For Government Contractors, Compliance is King
Are You a Government Contractor or Wondering What It Takes to Become One? Government contracting, or GovCon for short, isn’t...

Using SuiteAnalytics to View Account Data
NetSuite offers a powerful analytical tool that is available in your environment, SuiteAnalytics. Users can leverage this tool to create...

How To Install and Configure the NetSuite File Drag and Drop Bundle
Are you tired of the tedious process of clicking through multiple buttons to upload a file into the correct folder...

Utilize NetSuite Saved Searches for Automated Email Notifications
A key component to increasing a user’s productivity and efficiency is leveraging NetSuite’s Saved Search functionality. While many users are...
Transforming Dairy Operations with RSM’s Dairy Data Accelerator
The dairy industry operates in a unique space where precision, efficiency, and agility are critical to success. As the market...
![Modernizing Snack Food Manufacturing with Dynamics 365 F&SC [Case Study]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v1_grey.png)
Modernizing Snack Food Manufacturing with Dynamics 365 F&SC [Case Study]
A leading snack food manufacturer transforms its operational infrastructure for enhanced efficiency and business growth. Background A prominent private-label and...

Top 5 Things to Know in GovCon This Week (October 1st – October 7th, 2024)
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

Top 5 Things to Know in GovCon this Week (September 21st – 30th, 2024)
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...

Elevating Financial Management in Hospitality with Sage Intacct
Hospitality businesses have unique challenges to contend with, from seasonal demand to talent shortages, and from thin margins to increasing...

How Sage Intacct Forms and Operational Flows Fix Data Collection
Sage Intacct does remarkable things with data, organizing, analyzing, and distributing it to keep everyone focused on financial excellence. First,...
Maximize Your Business Insights with NetSuite’s Benchmark 360 SuiteApp
In today’s competitive business landscape, understanding key performance indicators (KPIs) is essential for maintaining a strong financial position. When clients...

Dynamics GP End of Support
In a recent announcement, Microsoft confirmed the end of mainstream support for Dynamics GP. This marks a critical juncture for...
Patient Refunds
Patient refunds are a common problem for Healthcare companies to navigate. Healthcare providers are in the business to deliver exceptional...

Measuring Important KPI’s in the Service Industry through D365 Field Service
In D365 Field Service, service providers can set up Service Level Agreements (SLAs) at an account level to define customer...

Embracing the Future: Adopting the New D365 Field Service Mobile UI in the Business and Professional Services Industry
In the field service industry, staying efficient and adaptable is crucial to being able to meet customer needs and handle...

Making the Most of your Work Breakdown Structure with Project Operations
Creating a Work Breakdown Structure For demonstration purposes, we will be using a construction project as an example. To begin,...

Revolutionizing the Business and Professional Services Industry with IoT and Field Service
With the fast-paced business environment, the integration of the Internet of Things (IoT) with D365 Field Service (Connected Field Service)...

Messaging for In App and Web
In the ever-evolving landscape of customer service, staying ahead of the curve is crucial. Salesforce has continually developed innovative solutions...

Flex Your Fitness Franchise With Sage Intacct
There are more than 113,000 gyms, health clubs, and fitness centers in America. In a crowded and competitive market like...

Financial Services: Gain Strength From Sage Intacct
Growing revenues, happy clients, talented employees, ambitious plans: all these advantages become irrelevant for financial services firms if the accounting...

Modern SaaS Accounting – ASC 606 with Sage Intacct
It has been several years since the ASC 606 revenue recognition standards introduced by the Financial Accounting Standards Board (FASB)...
![Milking Efficiency: Transforming Dairy Operation with Microsoft Solutions [Webinar]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v2_blue.png)
Milking Efficiency: Transforming Dairy Operation with Microsoft Solutions [Webinar]
Don’t miss the RSM Microsoft Food and Beverage team webinar “Milking Efficiency: Transforming Dairy Operation with Microsoft Solutions,” where we...

Work Smarter Not Harder: Integrate Sage Intacct & Procore
Streamlining Financial and Project Management in Construction: Sage Intacct + Procore In the same way that modern building projects depend...

Celebrating RSM’s FastTrack Solution Architects: Driving Excellence in Microsoft Solutions
RSM is proud to announce that three of our top professionals—Ryan Masschelin, Curtis McDonald, and David Merdian—have earned the prestigious...

Live webcast: Integrated financials and field service management: A single source of truth
We’re thrilled to invite you to “Integrated financials and field service management: A single source of truth,” on Wednesday, Sept....

From Insights to Action: How NetSuite’s AI Empowers Service Companies to Thrive
At SuiteWorld, NetSuite unveiled a slew of upcoming AI functionalities set to redefine the landscape for Business Service companies. These...
![Transforming Sustainability Reporting for a Vertically Integrated Agriculture Producer [Case Study]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v1_blue.png)
Transforming Sustainability Reporting for a Vertically Integrated Agriculture Producer [Case Study]
Sustainability is more than a buzzword in modern agriculture—it’s necessary. For a vertically integrated agriculture producer, accurately reporting sustainability data,...

Top 5 Things to Know in Government Contracting (August 27 – September 5th)
Stay ahead in the dynamic world of government contracting with our roundup of the top five must-know updates from this...
Simplify Lot Tracing with RSM
In today’s competitive marketplace, effective lot management is essential for businesses to maintain product quality, ensure traceability, and meet regulatory...

Mastering Incoterms: The Key to Successful Intercompany Transfer Orders in NetSuite
Intercompany Transfer Orders are used to move items from one subsidiary location into another subsidiary location. With an Intercompany Transfer...

Salesforce Data Cloud
Revolutionizing Customer 360 and AI-Driven Decision-Making for Businesses of All Sizes In the era of digital transformation, customer data is...
![RSM’s Microsoft Food & Beverage Newsletter [Summer 2024]](https://technologyblog.rsmus.com/wp-content/uploads/featured-images/all/industry-blog_fb_v2_blue.png)
RSM’s Microsoft Food & Beverage Newsletter [Summer 2024]
As summer comes to a close, the RSM food and beverage team is reflecting on an exciting season of growth,...

Top 5 Things to Know in Government Contracting This Week (August 15 – 21st)
Welcome to this week’s government contracting update, brought to you by RSM US LLP. Here are the top five stories...

Understanding FSMA 204: Enhancing Food Traceability for Safer Consumption
The Food Safety Modernization Act (FSMA) was created to make our food supply safer by focusing on prevention rather than...

NetSuite 2024.2 Release: Hot Topics for Nonprofits
The latest NetSuite 2024.2 release has arrived, bringing a host of new features and enhancements tailored to meet the unique...

The Main Event – Teams Premium Webinars
Teams Premium Mini-Series, Pt. 3: There are many ways to host a live, virtual event in 2024. Microsoft has invested...
Displaying Amount Due on Vendor Bills
Have you ever applied a partial payment to a vendor bill? Have you ever created a vendor prepayment for less...
Unleashing Desktop Magic: The Power User’s Guide to Microsoft PowerToys
Originally posted to https://maddydahl.com/microsoft-powertoys/ Power Automate, PowerApps, PowerToys, Power BI, oh my! Ever since the release of Power BI in...
RSM is an Azure Expert MSP
Celebrating RSM’s achievement RSM is now one of only 120 companies around the globe that call themselves an Azure Expert...

Updating Subsidiary External IDs
Have you ever tried to upload/update subsidiaries using NetSuite’s CSV Import? If not, you’ll be surprised to learn that you...

Importing Sales Data Through a CSV File, Mapped to Specific Locations
Do you run into errors when attempting to import location specific sales data through a CSV file? Follow these...

Top 5 Things to Know in Government Contracting This Week (July 21 – 29th)
Welcome to this week’s government contracting update, brought to you by RSM US LLP. Here are the top five stories...
Embracing the Future with Microsoft’s Global Secure Access
In today’s digital age, securing access to resources and data is more important than ever. Microsoft’s Global Secure Access offers...
Breaking down the Benefits of Salesforce Field Service Management
Salesforce offers customers a platform to improve their field service operations and automate and optimize processes for their field services...

System Audit Functionality in NetSuite
Introduction One of the many selling points of NetSuite is its ability to keep track of changes to almost all...

Automating Child Record Creation with Custom Records and Workflows in NetSuite
Introduction NetSuite’s custom record and workflow actions are powerful tools that allow for detailed customizations in any given environment. Using...

Top 5 Things to Know in Government Contracting this Week (July 7 – July 12, 2024)
Hello readers! Here are the top five things you need to know in government contracting for the week of...

RSM Celebrates Outstanding Team Members with Microsoft Most Valuable Professional Awards
RSM proudly announces the recognition of its exceptional team members through...
Case Study: Transforming Restaurant Operations with Azure Virtual Desktop
The organization, a pioneer in the restaurant industry, is renowned for its award-winning destination restaurants. The company has a rich...

Case Study: Modernizing a Multi-State Clinic with Azure
The clinic, known for its excellence in healthcare, employed over 100 Infectious Disease (ID) physicians across multiple states. Each office...

Navigating NetSuite China Localization: Enhancing Operational Efficiency
Introduction Expanding your presence in China on the unified NetSuite cloud ERP platform across finance, manufacturing, sourcing, sales, and operations...

Copilot Chat in Microsoft Dynamics 365 Business Central
With upgrades rolling out, you don’t want to wait on upgrading your Business Central environment to version 24. If you...
Automating Hospital Accounting Using EMRConnect
Automating Hospital Accounting Using EMRConnect For many hospitals and healthcare providers, a troubling disconnect persists between the clinical and financial...
Understanding Azure Nonprofit Credits
Did you know that nonprofits can benefit from annual Azure credits? Qualifying organizations can receive up to $2,000 for production...

Top 5 Things To Know In Government Contracting This Week (June 1 – June 9th, 2024)
Hello readers! As we step into the summer of 2024, the US government contracting sector has seen significant developments. Here’s...

Field Service Management Software Can Transform Your Field Operations
Field operations involve hard physical costs – trucks, fuel, parts, tools, labor. Coupled with constraints such as customer access and...

Key Takeaways from BlackLine’s Best Practices Summit – Los Angeles
BlackLine’s recent Best Practice Summit in Los Angeles featured engaging content and inspiring client success stories. As the event sponsor,...

SaaS Migration Strategy
Evolving from on-premises, single-tenant applications to multi-tenant, cloud-native applications hosted by cloud providers. With the advent of SaaS, businesses have...

HIPAA Compliance for NetSuite: Compliance 360
NetSuite’s new ‘Compliance 360’ SuiteApp is aimed at increasing visibility into NetSuite user activities, internal activity audits, as well as...

Tax Engine Comparison
Introduction NetSuite SuiteTax is a powerful tool that NetSuite users can leverage to streamline and empower their tax management with...
RSM Takes Key Insights from ServiceNow Knowledge 2024
RSM US LLP was a proud sponsor of ServiceNow Knowledge 2024, held May 7-9 at The Venetian Las Vegas. The...

Salesforce vs HubSpot: Choosing the Right CRM for Your Business
In today’s competitive landscape, a strong Customer Relationship Management (CRM) system is crucial for businesses of all sizes. Two industry...
Active Directory (AD) Critical Risk Analysis: Do you know your AD risk score?
In the era of digital transformation, the pivot towards cloud computing has been nothing short of revolutionary, offering organizations scalability,...
Optimizing Retail Operations with Terminal Integration
Watch Video Below: Terminal Integration with Dynamics 365 Payment Connector for Adyen Dynamics 365 Payment Connector for Adyen Integrating physical...

Transforming Global Supply Chains: The Industrial Tech Revolution
Introduction: In an era where global supply chains face unprecedented challenges, from unpredictable market demands to labor shortages, industrial companies...

RSM Achieves Cisco Specialization, Reinforcing Commitment to Cutting-Edge Solutions
RSM is proud to announce its latest achievement, which was receiving a prestigious Cisco specialization. This recognition underscores RSM’s dedication...
Omni-Channel Payment Management with the Dynamics 365 Payment Connector for Adyen
Watch Video Below: RSM + Adyen Payment Connector – Omni Channel Dynamics 365 Payment Connector for Adyen In the retail...
Key Takeaways from Coupa Inspire
This post was written by RSM, a Coupa Alliance Partner. From initial implementation through expansion and optimization, we have the...
Streamlining Payments in the Retail Sector
Watch Video Below: Discover how the Dynamics 365 Payment Connector for Adyen enhances retail payment systems Dynamics 365 Payment Connector...

How CTA balance gets calculated in NetSuite?
Cumulative Translation Adjustment (CTA) account balance represents the translation gain or loss due to the translation of financial statements of...

Mastering Efficiency: NetSuite’s Intercompany Inventory Transfers
Introduction: Managing intercompany inventory transfers seamlessly becomes crucial for companies operating across multiple subsidiaries or entities. NetSuite offers a robust...
Minimum Order Quantity (MOQ)– for Lot Sizing for Supply Planning
Introduction With the NetSuite 2023.2 Release, a new and significant Lot sizing option has been introduced in Supply Planning –...

New for Nonprofits – Automating Net Asset Release
As a financial management platform suited to the unique needs of nonprofits, Sage Intacct has evolved from good to better....

Sage Copilot – Your New Favorite Feature
With Sage Copilot, artificial intelligence and accounting combine forces to change the future of financial management. This brand-new tool from...

Highlights from the Sage Transform Conference
The annual Sage Transform conference brings together users across the Sage ecosystem to commune, collaborate, and celebrate. It’s always an...

Sage Intacct – More Automation & Integration Than Ever
Sage Intacct – More Automation & Integration Than Ever Sage Intacct and RSM have a common goal: saving time for...

Sage Intacct 2024 R1 Update Highlights
So many additions, enhancements, and upgrades come included free with each quarterly Sage Intacct update that it would be impossible...

Transitioning From QuickBooks to Sage Intacct Construction
Transitioning From QuickBooks to Sage Intacct Construction: Unleashing Efficiency and Growth As strong financial management increasingly defines the most competitive...

Moving to Cloud Voice – Importance of Discovery
Moving to a modern voice solution can be scary because of the various unknowns, dependencies on legacy hardware, and user...
Outlook for Web; Outlook for Everything!
Teams Chats Are Now Available in Outlook Over the course of the past few months, Microsoft has continuously updated and...

NetSuite Budget Versus Actual Reporting with NFP Segmentation
The native NetSuite report for Budget Versus Actuals does not include Not For Profit segmentation including restriction, grant, and program....

Netlease Accounting
Introduction NetLease was built to address the new lease accounting standards ASC 842, IFRS 16, and GASB 87. It supports...
Cloud Migration: Common Pitfalls and How to Avoid Them
A guide for enterprises and organizations that want to leverage the benefits of cloud computing without compromising on aspects such...

Historical Trial Balance Methodologies Comparison
When handling Historical Trial Balances (HTB) with a Client’s NetSuite environment there are two methodologies we can follow. 1. Net...

How to use the ‘Copy to Account’ feature in NetSuite.
Copy to Account is an administrator tool designed to transfer custom objects between your accounts. Copy to Account allows you...
Top 5 Things to Know in Government Contracting This Week (April 13th – 19th, 2024)
Hello readers! Here are the top five things you need to know in government contracting for the week of April...
Wow customers with a React based user experience to boost revenue
Enhancing user experience is not just about aesthetics; it directly correlates with improved business outcomes. A React-based Single Page Application...
Upcoming NetSuite AI Enhancements
Oracle is prioritizing investment in Artificial Intelligence to improve functionality in upcoming NetSuite updates. The company plans to roll out...
Grow revenue with strategic cross-selling despite margin pressure
In today’s competitive ecommerce world, retailers are hard pressed to handle ever increasing margin pressure. However, retailers can grow revenue...

Top 5 Things to Know in Government Contracting This Week (April 6th – April 12th, 2024)
Here are the top 5 things you need to know in the government contracting space this week: Lockheed Secures $4.1B...

Future-Proof Your Access: Switch to User-Based Authentication Before the Deadline
Before diving into the details of the upcoming authentication changes for the Warehouse Management Mobile App, we highly recommend watching...

NetSuite Japan Localization
Co-Author: Pawan Singh and Satyam Shah NetSuite SuiteTax is a global tax management solution seamlessly integrated into the NetSuite platform,...

Elevating Customer Connections in the Consumer World with NetSuite CRM
In the world of consumer products, crafting unforgettable customer experiences isn’t just a luxury—it’s the key to differentiation. In the...

Setting up NetSuite Bank Feeds SuiteApp
Clients are often looking to automate their bank data import into NetSuite to avoid the tedious import of bank files....
Setting up NetSuite with Ramp
At RSM, we frequently get asked to integrate AP automation solutions with our clients’ NetSuite instances, and sometimes even get...
Setting Up Settle with NetSuite
RSM recently worked on a NetSuite implementation where the client used a platform called Settle, an AP automation tool and...

Sage Intacct Advanced Ownership Consolidations: A Game-Changer
Sage Intacct Advanced Ownership Consolidations: A Game-Changer Here’s a dilemma familiar to any owner (or ownership group) with less...

New Release 2024.1 – Revenue Recognition Field Mapping Enhancements
Co-Author: Eric Frei The release of NetSuite 2024.1 has brought enhancements to the Revenue Recognition Field Mapping functionality. Before diving...

Customer Refund via Electronic Bank Payments
NetSuite offers a SuiteApp, Electronic Bank Payments, that enables users to process bill payments, employee expenses, partner and employee commissions,...

Expensify and NetSuite Integration Overview
One powerful way to streamline your processes is by integrating Expensify and NetSuite, two industry-leading solutions designed to simplify expense...

Subscription Billing – Focusing in on Minimums and Maximums
Minimums and Maximums Minimums and Maximums are an attribute of the usage-based pricing model that helps control the variability of...

How well are companies navigating workforce balance?
HCM solution provider Dayforce surveyed 8,700+ global workers to find out It is up to employers to discern whether the...

Dynamics GP: Will you stay or will you go? Take our survey
Microsoft is sunsetting Dynamics GP yet plans to support it through 2028. Some organizations will stay with the platform to...
Transform Your Warehouse with NetSuite WMS: Benefits, Features, and Insights
In the dynamic landscape of industrial operations, Warehouse Management Systems (WMS) are pivotal for efficient logistics and streamlined processes. For...

Simplifying NetSuite Inventory Adjustments: A Guide to Single-File Imports
The inventory adjustment record changes the quantity and value of an item without entering a purchase order. Inventory adjustments are...

How to set up NetSuite Pay
NetSuite Pay is a new SuiteApp developed by NetSuite that is a fully integrated payment processing solution for clients using...

From Inventory to Assets: Harnessing NetSuite for Strategic Asset Management
NetSuite’s Fixed Asset Management SuiteApp has an Asset Proposal feature that allows you to propose new assets from transaction(s) recording new assets....

Using Stored and Non-Stored Custom Fields in Saved Searches
Overview: Saved Searches in NetSuite are a powerful tool that allows users to search through thousands of records and return...

User Interface Enhancements To SuiteAnalytics Workbook
With the release of NetSuite 2023.2, enhancements and quality-of-life improvements have been made to SuiteAnalytics Workbook. Let’s look at what...

Introducing The New Teams Discover Feed
Microsoft has begun rolling out their New Microsoft Teams application globally. This new iteration of Teams introduces a plethora of...

Selecting NetSuite Multibook Accounting: An Essential Guide
In the ever-evolving landscape of business, staying ahead of the curve requires the right tools and strategies. NetSuite offers a...

NetSuite’s GL – Matching Features and Capabilities
GL Matching is a feature in NetSuite that adds the ability to match transactions, a common practice in many countries,...

Ben Vollmer Joins RSM’s Microsoft Practice as Power Factory Growth and Product Leader
Welcome back to the Microsoft community Ben Vollmer! RSM is pleased to announce Ben will be joining the RSM Power...

Upcoming Nonprofit’s Events
Upcoming Event: Explore the future of your board: Digital transformation and risk Join Directors & Boards’ executive publisher David Shaw...

Copilot for Microsoft 365 Community Series – Session #2
RSM is excited to present the second session in our community series on Copilot for Microsoft 365, the AI-powered assistant...

Microsoft Fabric Community Conference
RSM is excited to be a Gold sponsor of the inaugural Microsoft Fabric Community Conference March 26-28, 2024 in Las...

Standard Costing in NetSuite
Introduction: In the complex business management and financial tracking world, implementing effective costing methods is crucial for organizations to maintain...

5 Things to Know in Government Contracting This Week — February 26 – March 4, 2024
Here are the top 5 things to know in Government Contracting this week: New Government Contracting Opportunities and Emerging...

NetSuite Creating Custom Sublists and Common Sublists for Non Profit Clients
Introduction One of the benefits of NetSuite’s unified data structure is the interconnectivity of data. NetSuite sublists can be utilized...

NetSuite 2024.1 New Release – NetSuite Pay SuiteApp (version 1.0.0)
The latest NetSuite 2024.1 Release introduces upgrades aimed at empowering organizations to optimize their data management, bolster software security, and...
AP Automation: Bill Capture
What is bill capture? Using Bill Capture, you can upload or Email vendor bill files to create NetSuite vendor bills....

Smart Count SuiteApp Enhancements
In the fast-paced world of business, efficient inventory is a crucial part of warehouse management’s best practices. With customers wanting...
Quartzy and NetSuite Integration Overview
Quartzy simplifies lab management by streamlining procurement and inventory tasks. Quartzy now provides Netsuite integration, enhancing the efficiency of the...

Distributing Expenses Across Subsidiaries in NetSuite via the Transaction Line Distribution SuiteApp
Nowadays, many businesses use NetSuite’s OneWorld which enables them to manage records and transactions for their multiple subsidiaries. Often time,...

Advanced Inventory: Automated Reorder Points
Overview Advanced inventory enhances NetSuite and provides more visibility between locations and an even furthered automated environment. The automated reorder...

Top 5 Things to Know in GovCon this Week: February 17th-23rd, 2024
Here are the top 5 things to know in Government Contracting this week: Compliance and Regulation Updates: This week,...

Revolutionizing Real Estate: Sage Intact Real Estate Software
Revolutionizing Real Estate: Sage Intact Real Estate Software For real estate professionals, it’s the best of times and the...

Teams Premium Miniseries, Pt. 2: All About Your Brand – Explaining Teams Premium’s Custom Meeting Themes and How to Make Them
Microsoft has officially begun to roll out its suite of new features for Teams Premium. This new toolset brings a...

Getting Started with the Payment Automation SuiteApp
Getting Started with the Payment Automation SuiteApp Automation is a fast-growing facet of successful modern businesses. Cash flow management becomes...

Customize a Subscription Pricing Sublist
Customize a Subscription Pricing Sublist Within a subscription record, clicking Customize will allow editing of the display order and field...
Welcome to the NEWest chapter of Microsoft Teams!
As we embrace this exciting era, let’s explore what makes the new version of Teams a standout upgrade from its...

Automated Cash Application
Month-end close is a stressful time for many of our clients, and simplifying that process is one of the many...

NetSuite Cash Application: Simplify Finances with Automation
NetSuite Cash Application: Simplify Finances with Automation This article comprehensively examines NetSuite’s Automated Cash Application feature, covering its key benefits,...

NetSuite 2023.2 Quality Management SuiteApp Enhancements
This blog is co-authored by Nikita Kumari and Brittany Quinlan. Effective quality management helps organizations meet regulatory and internal quality...
Empowering Daily Tasks with Copilot Studio: Integrating AI Solutions
Copilot Studio, formerly Power Virtual Agents, is a part of the Power Platforms suite that offers a solution to integrating...

Copilot for Microsoft 365 Community Series
RSM would like to thank everyone who was able to join the first session of our new community series on...
AI Copilots: From R2-D2 to Jarvis, How AI Technology is Transforming Our Digital Assistants
Welcome to the cutting-edge world of AI copilots, the latest innovation reshaping our interaction with technology in the workplace. These...

Vendor Prepayment with Bill.com Solution
REQUIREMENT: Clients often have a requirement where they need to pay vendors a pre-payment on a shipment per the established...
Salesforce Commerce Cloud 2024 Roadmap: Composable Innovation Leads
The Salesforce Commerce Cloud 2024 roadmap announcement brings a plethora of exciting features, with particular attention to the enhancements...

2025 RSM Microsoft Events
RSM: Driving meaningful connections in the Microsoft Community At RSM, we are deeply engaged in the Microsoft Community, actively supporting...

Utilizing Microsoft Mesh in Teams Meetings
Microsoft Mesh is a new platform that enables immersive and collaborative experiences across multiple devices and locations. With Mesh, you...

Saudi Arabia E-Invoicing- NetSuite Integration for ZATCA Requirements
As businesses continue to expand and grow internationally, it is more important than ever to have a system to manage...

Change on the Horizon: WORK Transactions Deprecated in D365 Finance & Supply Chain
We want to ensure you know of an upcoming change to how inventory transactions associated with WORK/inventory movements within an...

NetSuite CPQ: The Next Thing for You
Within the fast-moving business environment of global enterprises, managing customizable and complex products while dealing with length sales cycles, inconsistencies...

SuiteTax and India localization Overview
Co-author: Sansdeep Gill NetSuite SuiteTax is a global tax management solution seamlessly integrated into the NetSuite ERP platform, catering to...
RSM Cloud Readiness and Assessment Services Overview
RSM provides modular, framework-based Azure cloud readiness assessment services to confirm our clients’ business and IT ecosystem are ready and...

Unleashing Operational Excellence: The Impact of MES-ERP Integration in Manufacturing
In the dynamic realm of manufacturing, the adoption of Industry 4.0 strategies and factory automation has become increasingly prevalent among...

Matrix, Kit, and Group Items – How Do They Differ?
NetSuite’s inventory capabilities feature various individual inventory item types, such as serialized inventory and non-inventory for resale. Often, multiple items...

NetSuite Custom Records for Multiple Field Defaulting
Custom Records Custom records in NetSuite can assist organizations in organizing and utilizing information that cannot be done through native...

NetSuite Account Reconciliation Software – Simplify Your Account Reconciliation Process and Accelerate Financial Close
What is NetSuite Account Reconciliation Software? NetSuite Account Reconciliation provides an all-in-one, centralized workspace for Account Reconciliation and Transaction matching....

Streamlining Operations: RSM’s NetSuite Impact on Distribution Success
NetSuite is a cloud-based business management software that is an excellent fit for distribution. Because NetSuite’s functionality is a great...

NetSuite Tips & Tricks
NetSuite delivers business value, a value that grows with increased customization of dashboards, personalization of preferences, and fine-tuning of saved...

RSM Achieves the Cisco Hybrid Cloud Computing Specialization
RSM announced today that it has achieved the Cisco Hybrid Cloud Computing Specialization through the Cisco Partner Program. The distinction...

Zone Advanced Billing: A NetSuite Suite App
What is Zone Advanced Billing (ZAB)? Zone Advanced Billing is a Subscription and Billing Management native NetSuite SuiteApp built for...

Creating a Transaction Line Distribution Schedule
Overview The Transaction Line Distribution SuiteApp provides organizations the ability to distribute expenses across different subsidiaries, classifications, custom segments, departments,...

Electronic Bank Payments Enhancements
NetSuite has introduced the 2023.2 new release notes, which includes enhancements to the Electronic Bank Payments SuiteApp. The Electronic Bank...

How NetSuite’s SuiteBilling Renewal Uplift Percentage Functionality Can Boost Your Revenue
Are you a business that offers subscription-based products or services? If so, you likely understand how challenging the renewal...
NetSuite – Financial Institution Setup
Let’s talk about High-level Process Bank Reconciliation Process Now the question arises Why we need to setup a Financial Institution...

Unlocking Opportunities: RSM at the Nonprofit Innovation Hub
Embark on a journey into innovation with RSM! We’re thrilled to sponsor the National Mentoring Summit, an exclusive gathering where...

NetSuite Costing
Optimizing your business’s potential involves seamlessly blending accounting and inventory functionalities. Imagine effortlessly tracking asset values and calculating profits. Welcome...

Strengthen Your Cybersecurity with Microsoft’s New Conditional Access Policies – Act Now!
As your first-choice advisor in the middle market, we at RSM are committed to keeping you informed about the latest...
NetSuite Outsourced Manufacturing: Starting from the PO or Work Order
NetSuite’s Outsourced Manufacturing function allows companies to track production of finished goods performed by outside companies. Outsourced Manufacturing (also referred...

Fixed Assets Management SuiteApp : Initial Set Up
Oracle NetSuite Fixed Asset Management (FAM) empowers companies to optimize their asset-related processes comprehensively. Through the capabilities of NetSuite, businesses...

Optimize the performance of your network with Cisco SD-WAN
Cisco SD-WAN is a cloud-based network solution that simplifies and secures the connectivity between branches, data centers, cloud applications, and...

NetSuite Fixed Asset Management: Overview
Co-authored with Pawan Singh The NetSuite Fixed Assets Management SuiteApp plays an impactful role in automating the company’s management of...

Embracing Sustainability: The Imperative of ESG in Industrial Companies
There has been a paradigm shift in the business world in recent years towards a more sustainable and responsible approach....

SharePoint Look Book – Learning Pathways
Have you ever heard of the SharePoint Look Book? If not, there’s no need to worry; you aren’t alone. The...

Microsoft Nonprofit Global Summit
Welcome to the heart of innovation! RSM is excited to participate in the Global Nonprofit Leaders Summit, an exclusive event...

Must-Try Features in the Sage Intacct 2023 R4 Update
The 2023 R4 update to Sage Intacct is one of the most important and exciting in recent memory, making additions,...

Common Customer Portal Functionality with Salesforce
Customers for B2B companies expect to be able to do self-service transactions at any time. Whether it is finding more...

Teams Premium Miniseries, Pt. 1: All About Your Meetings – Intelligent Recap
Microsoft recently introduced Teams Premium, an add-in for the popular communication tool, Teams. This new offering comes with a range...

Unlocking the Potential ROI of AI: A Physics Perspective
Technology has always been a catalyst for transformative growth, and today, Artificial Intelligence (AI) holds tremendous potential to reshape businesses. Like potential...

Rebate Enhancements Patch notes 2023.2 NetSuite
In the Dynamic landscape of modern business, maximizing profitability and streamlining operations are perpetual goals. NetSuite continues to evolve in...

Webinar Recap – Navigating Mergers & Acquisitions in the Industrial Sector with NetSuite
Mergers and acquisitions (M&A) are common in the many industries including industrials, but they also pose significant challenges for business...
SharePoint Online Migration Myth Busters: Navigating the Maze
Co-written with William Jones. SharePoint Online, the robust cloud-based collaboration platform from Microsoft, has become the go-to destination for organizations...

RSM & Microsoft – Providing Solutions Through the Art of the Possible
RSM and Microsoft are strategically collaborating to tap into the $10 trillion digital market. RSM, renowned for its end-to-end Industry...

Enhancing Vendor-Item Approval in NetSuite’s Purchase Order Process: Implications in the Life Sciences Industry and Beyond
*This is a scripted customization. For more information on implementing into your NetSuite instance contact a member of the RSM...

ZoneBilling vs. SuiteBilling as a NetSuite Billing Solution
In the fast-moving business environment of global enterprises, managing complex billing processes is central to continued success. For NetSuite, the...

Is it time to migrate from your legacy ERP?
Is it time to Migrate from your Legacy ERP? Signs to Migrate from an Old System include: Unsupported Technology The...

Common Portal Functionality for Driving Partner Success
Very few companies stand completely alone in their quest to grow. That is why most companies build partner networks and...

NetSuite – Enhancements to SuiteAnalytics
NetSuite has new 2023.2 Release Notes that provides enhancements to SuiteAnalytics capabilities. With these new enhancements, users can expect to...

Leveraging Oracle NetSuite to Enhance Business Value through CRM Insights
As businesses navigate the complexities of client and sales data management, gaining meaningful insights becomes crucial for assessing and improving...

Microsoft Dynamics GP Year-End Close Webcast Series
Event overview Your year-end close doesn’t have to be painful! RSM will help you navigate through all the latest changes...

Costed Bill of Materials SuiteApp
The NetSuite 2023.2 release introduces a highly anticipated feature for manufacturing clients: the Costed Bill of Materials, without any additional...

NetSuite – HMRC Integration for submitting digital UK VAT100 Report
Why implement HMRC Integration functionality within NetSuite? As of April 1, 2019, the United Kingdom requires VAT-registered businesses with a...
Digital Transformation in Real Estate – Time to Get Onboard
This chart comes from a recent PwC survey of over 1,000 real estate professionals. Respondents were asked whether different technologies...

Microsoft Copilot Dashboard: A Copilot and Viva Collaboration
Microsoft has finally released Copilot to the general audience, and the AI train has been moving full speed ahead ever...
Turning an ask into a task with Microsoft Teams and To Do
When working on multiple projects, committees, organizations, and workgroups we often fall behind on the little things. These simple asks...

Recent IRS change related to filing Year End documents, including 1099s, W2s and 1095-Cs
As we approach 2023 calendar year end, the RSM team would like to make sure you are aware of a...

RSM’s Approach to Content Migration to Microsoft 365
One of the most common challenges that RSM’s clients face is document management. Typically, outdated and disorganized files cause inefficiencies,...

Copilot for Microsoft 365 (M365): M365 Chat First Looks
“Captain’s log, Stardate 77302.3; Chat is now mainstream…” Chatting with a computer used to be science fiction… “Computer, engage.” But...

The New Wave of Teams Premium: Three Invaluable Features Available Now
Microsoft Teams has been heavily utilized across businesses everywhere for a few years, and now that we are in the...

Microsoft Secure Score: What is it and what does it mean for you?
What is Microsoft Secure Score? Microsoft Secure Score is a security analytics tool that helps organizations assess and improve their...

Using the Updates App in Microsoft Teams
Microsoft Teams has changed the way we work and remain productive in the evolving business landscape. Microsoft Teams provides the...

Microsoft 365: Is Your Organization RaMPing UP?
In a rapidly evolving digital landscape, businesses are constantly seeking ways to optimize their operations, enhance productivity, and stay competitive....

Copilot for Microsoft 365 – Outlook Email First Looks
Copilot for Microsoft 365 (M365) was released for enterprise customers on November 1, 2023. The scale of the Copilot for...

Are you ready for Microsoft Copilot?
Written in collaboration with Kaleb Dombeck Your everyday AI Companion Microsoft Copilot is designed to revolutionize how we work, offering...

Now is the time to modernize with Microsoft D365 Business Central
Upgrades and transitioning to the latest versions of ERP software requires meticulous planning and skilled execution by a team of...

The Best of Breed Approach when selecting Construction Solution Software
The best-of-breed approach is when selecting ERP Construction, which is choosing specialized software products that meet your company’s requirements. This...

New Service Overview: Implementing Microsoft Syntex
Biotech uses automation to simplify data extraction process RSM recently implemented Microsoft Syntex for a biotechnology company specializing in therapeutics....

Grouping Invoices with Sub-Customer Reference on Child Invoices
Overview If NetSuite Invoice Grouping is being used, and each Invoice being grouped has different customers, all of which are...

A Successful Training Partnership: RSM and Sage Intacct
In the world of accounting and financial services, the adoption of new software can be a daunting experience. This is...
Field Service to Cash: Simplifying Processes for Improved Cash Flow
In today’s fast-paced business world, effectively managing cash flow is crucial for companies to remain competitive and financially stable. Fortunately,...

Power Automate: Streamline and Accelerate Contract Processing
In the fast-paced world of modern business, efficiency and automation have become essential components for success. One area where this...

SharePoint: An Intranet Solution
When our clients consider SharePoint, they often envision a web-based repository for distributing and storing digital content. While technically accurate,...

The Crucial Role of Landed Cost in Your Business: A Comprehensive Guide
In the world of supply chain management and business profitability, there’s a term that often goes unnoticed but holds immense...

RSM US LLP Expands Microsoft service offering for Government Contractors with D365 Finance and Supply Chain now supported in GCC High
Washington, DC – RSM US LLP, a leading provider of audit, tax, and consulting services focused on the middle market,...

RSM’s Nonprofit Relationship Management Practices – Activity Update
Giving back. RSM’s Support of our nonprofit and association industry clients. 2023 has been a hectic year for RSM. Here’s...

RSM Presents: New Veeam BaaS Solutions
Are you looking for an easy to use and reliable method for protecting your Microsoft 365 and Azure data? If...

Bring EMRs into Sage Intacct the Easy Way
Sage Intacct gives users more than just a powerful toolkit for accounting and finance. In practice, Sage Intacct serves as...

Tracking Nonprofit Committed vs. Encumbered Costs in Sage Intacct
For nonprofits to make the biggest impact, comply with all funding requirements, and maintain a positive reputation, they must carefully...

Community Summit NA Conference
RSM is excited to be a sponsor at the Community Summit NA Conference this year October 15th-20th. Please view our...

Streamline Your Construction Business with NetSuite Construction ERP
In the highly competitive construction industry, staying ahead of the game requires efficient project management, resource allocation, and financial control....

NetSuite – New Copy Function in SuiteBilling
New Copy Function in SuiteBilling With the recent publication of the 2023.2 Release preview in Netsuite, there have been exciting...

NetSuite Fixed Assets Management Enhancements 2023.2
NetSuite has recently released its 2023.2 new features preview for Fixed Assets Management. These features enhance functionality around leases,...

Using the Department Dimension to Track SaaS Operating Expenses
The SaaS landscape has never been more crowded or competitive than now. That brings up an essential question—what drives success...

Dreamforce 2023 and the AI Revolution
Dreamforce 2023, the most anticipated event of the year for those in the Salesforce ecosystem, witnessed a phenomenal three-day gathering...

Achievable eCommerce Holiday Readiness Tips
Lawrence Walters explains how Salesforce Commerce Cloud retailers still have time to get ready for the busy holiday season. Looking into customer journey friction points for small fixes, taking advantage of all the Einstein search and recommendation features, and knowing your holiday plan and daily operations are the three actions you can take in the next 4 weeks.
NetSuite New 2023.2 Release Features: Ship Central
NetSuite New 2023.2 Release Features: Ship Central NetSuite has released its new 2023.2 features enhancement sneak peeks scheduled to roll...

Generative AI coming to SFCC Page Designer
Salesforce announced generative AI is finally coming to Salesforce Commerce Cloud (SFCC) B2C this week at Dreamforce 2023. We have...

NetSuite Revenue Recognition with Grant Billing
Overview Many Nonprofit organizations leverage NetSuite’s Advanced Revenue Management (ARM) and Projects modules to automate monthly revenue recognition for Grant...
Community Summit – RSM Speaking Sessions
RSM is thrilled to be a premier sponsor of North America Community Summit in Charlotte, NC (Oct. 15-20, 2023). We...

Family Office Asset Tracking with Sage Intacct Dimensions
The average family office manages over $1 billion in assets across a diverse portfolio of public and private equities, income...
NetSuite and Salesforce: Quick wins for CRM and ERP integration
Customer Relationship Management (CRM) software encompasses a wide range of business capabilities from marketing automation to sales management to quoting...

NetSuite Expense Allocation Journal Entries and Working Through Common Errors
Overview Utilizing NetSuite’s Expense Allocation feature can help your business save time and resources by automating the process of allocating...

NetSuite SCM & WMS: 2023.2 New Release Features
NetSuite has just released its 2023.2 new features preview for NetSuite WMS. These features enhance the user experience on the...
The Present and Future State of Salesforce AI Cloud
Empowering Enterprises with Generative AI Salesforce introduced Salesforce AI Cloud on June 12, 2023, a groundbreaking suite of capabilities that...

Why NetSuite for Construction? Part 1
Part 1: Automation Some of the key benefits of an ERP (Enterprise Resource Planning) in Construction Why are so many...
Subscription businesses and Salesforce Revenue Cloud
The “subscription economy” has changed our lives, both personally and professionally, and by now we are all familiar with the...

Lease accounting got harder, now it’s getting easier
Should you rent or buy the assets your business relies on? There are pros and cons to both options. But...

Embrace the Magic of Dreamforce with these 5 tips
Use these five strategies to get the most out of Salesforce's Dreamforce conference in San Francisco September 12-14.
Improving Project Workflow: A Digital Transformation Success Story
For global organizations, managing project workflow, especially within IT, can be a daunting task. With projects of varying scopes and...

6 Things to Consider when Integrating an ERP and Construction Software
Enterprise Resource Planning (ERP) software and construction management software are two essential tools for managing construction projects. However, the integration...

NetSuite for Non-Profits: Releasing Funds from Restriction
NetSuite’s SuiteSuccess package for Non-Profits allows users to release funds from restriction once sufficient expenses have been spent towards Revenue...

NetSuite’s New Supply Planning Features: Improved Lot Sizing Methods – New Lead Time Offset
NetSuite 2023.1 Release Changes to Material Requirements Planning – 2 New Features for all NetSuite Users NetSuite’s 2023.1 Release provides...

Setting Up Supply Allocation & Allocation Strategies
Enabling Supply Allocation To start creating Allocation Strategies, you will first need to enable features for Supply Allocation. Navigate to...
2023 Microsoft Innovation Summit
Event Overview Event Date: 9/20/2023 Time: 1pm – 4pm ET As a Microsoft user, staying updated with the latest advancements...

NetSuite WMS: 2023.1 New Release Features
NetSuite recently rolled out the new 2023.1 release for WMS, which will make enhancements for how inventory is managed within...

Microsoft GCC High Portal URLs
The following list includes all portal URLs for Microsoft GCC High: Microsoft 365 Admin Portal GCC High – office365.us Intune...

On the Path to GCC High: How to Validate Your Organization with Microsoft
In a previous article, we discussed each of the currently available editions of Microsoft 365. These ranged from the base...

Harnessing ESG for NetSuite: A Pathway to Sustainable Success
In today’s rapidly changing business landscape, companies are increasingly realizing the importance of incorporating environmental, social, and governance (ESG) factors...

Dynamics User Group Northeast Regional Meetup (In Person) – Arlington, VA
Join us at the Dynamics User Group Northeast Regional Meetup, taking place in Arlington, VA! This exciting in-person event, hosted...

Streamline Healthcare Reporting with Sage Intacct
Producing accurate, detailed financial reports may be the single most important capability for today’s healthcare organizations—no matter their size or...

Streamline your Systems to Up your Impact: Microsoft Tools for Nonprofits
Thank you so much for joining our sessions! Please find the videos below! May 25th, 2023: A new approach to...
Sage Intacct SaaS Intelligence Dashboard
SaaS continues on what looks like an unstoppable ascent. Estimates suggest that annual SaaS revenues will top $716 billion by...

RSM Wins Microsoft US Defense and Intelligence Partner of the Year 2023!
We at RSM, a leading global provider of audit, tax, and consulting services, are thrilled to announce that RSM has...

Revolutionizing Non-Profit Fundraising: Harnessing AI for Hyper-Personalized Donor Outreach Introduction
In the non-profit world, fundraising campaigns are vital in driving positive impact. However, creating compelling and personalized donor outreach content...

Streamline Your Accounts Payable Process with NetSuite Invoice Management
Efficient invoice management is crucial for businesses to maintain accurate financial records, process payments promptly, and nurture strong supplier relationships....

Elevating Business Outcomes: Customer Experience and Its Impact on The ‘Total Experience’
As defined by Gartner’s Top Strategic Technology Trends, the “Total Experience combines multi-experience, customer experience, employee experience, and user experience...

Highlights from ServiceNow Knowledge 2023
RSM was proud to be a gold sponsor of ServiceNow’s Knowledge 2023 conference at The Venetian Las Vegas, May 16−18,...
Preparing for the transition off Dynamics GP
Is your organization ready to move off Dynamics GP? This short list is meant to assist you in building out...

Scheduling NetSuite WMS Wave Releases Tips and Tricks
Overview NetSuite WMS allows for the automation of wave releases for sales and transfer orders. Once the orders have been...

The future of AI and a Composable Commerce reality – Key takeaways from Salesforce Connections 2023
Salesforce made a big splash with soon to be released or piloted AI tools for more seamless management of customer...

Microsoft Viva Insights & The “Quiet-Quitting” Concept
The Great Resignation denotes the massive wave of employees who – resulting from the COVID-19 pandemic and other economic factors...

NetSuite Saved Search Formulas – Using Date in Saved Search Formulas
NetSuite Saved Searches are a data query tool that can have many advanced search filters and results display options. Searches...

What Satya Nadella’s Top 5 Copilot Features at #MSBuild Reveal about the Future of AI Development
Microsoft Build is a conference highlighting the latest innovations and trends in software development. This year, the conference focused on...

Copilot for Dynamics 365 Customer Service
This blog was originally posted by RSM’s Microsoft MVP, Dian Taylor, here. I am sure you have heard all about...

RSM – Cisco Certification Update – Secure Access Service Edge (SASE) & Hybrid Work from Office
Cisco certifications have become a benchmark of excellence in the IT and networking field. RSM is proud to be one...

Accelerating Digital Transformation with the Power of AI using Microsoft Co-Pilot
As businesses continue to embrace digital transformation, the role of AI and machine learning in driving efficiency and productivity has...

Advanced Revenue Management Period Close Checklist
NetSuite has introduced the 2023.1 new release notes, which includes enhancements to the Advanced Revenue Management Period Close Checklist. The...
Optimizing Quote-To-Cash (QTC) For Evolving Landscape of Customer Sales Channels
LastPass is one of the leaders in the security industry, particularly in password management. LastPass is in the process of being...

Microsoft 365 Commercial, GCC Moderate, & GCC High: What are they and how can RSM help?
RSM provides end-to-end, industry-specific Microsoft solutions for thousands of our clients across the world. We are an award-winning Microsoft Cloud...

Top 3 Concerns of Salesforce Customers Looking to Upgrade to Composable Commerce
Salesforce Commerce Cloud customers are concerned about upgrading from the aging SiteGenesis (SG) architecture to Headless or Composable Commerce. There...

Personalizing Customer Experiences with Salesforce and Language.io
In today’s global marketplace, providing a personalized customer experience is more important than ever before. When customers feel that a...

Allocating Indirect Costs in Healthcare: Simpler With Sage Intacct
Healthcare accounting comes with complex and time-consuming requirements for even the smallest of providers. As organizations grow larger, the scale...

NetSuite File Drag and Drop Bundle – How to Let Users with View-Only Permissions Attach Files to Records
A popular bundle used by many companies on NetSuite, the File Drag and Drop Bundle adds functionality that allows users...

A new approach to Fundraising – Microsoft Cloud for Nonprofit
As the world becomes more interconnected and technology continues evolving, nonprofits constantly search for new and innovative ways to raise...

Sage Intacct for Family Offices: Track Investments With Dimensions
We have written several times before about why Sage Intacct is not just an appropriate but an ideal financial management...

Using Data to Better Tell Your Nonprofit’s Story: A Webcast Review
DDS (Data and Digital Services) Leadership recently presented a webcast for nonprofits, Using Data to Better tell your Nonprofit’s Story....
Tactical Tips on improving your DSO (Days Sales Outstanding) for your Salesforce Org
Days sales outstanding (DSO) is a measurement of the average number of days that it takes for a company to...

Salesforce Person Accounts Overview
If you’ve been following the Salesforce Nonprofit Cloud news (Nonprofit Cloud), you know one of the significant changes between Nonprofit...

Sage Intacct + Kantata – A Powerful Pairing for Professional Services
Research suggests that professional services firms are struggling with digital transformation. Only 12% of firms have completed their transformation, and...

Crossfit goes global in digital transformation project for customer experience
Crossfit is one the most recognizable brands in fitness. With growth to over 5 million athletes and over 14,000 locations...

Empowering Nonprofits: How Microsoft’s Cloud Solutions and RSM’s Advisors are Driving Digital Transformation
The nonprofit industry has undergone a significant digital transformation in recent years, with an estimated value of over $50 billion....

Microsoft’s New AI Assistant: Microsoft 365 Copilot
Microsoft recently announced the revolutionary new Microsoft 365 Copilot service, which is poised to help businesses and individuals maximize productivity...

NetSuite WMS: Errors from 2023.1 Release & How to Resolve Them
NetSuite recently rolled out the new 2023.1 release for WMS, SCM Mobile, and MFG Mobile, which may cause errors in...
Working with NetSuite’s Dynamic & Static Groups
In NetSuite, Groups are a set of employees, contacts, customers, partners, or vendors. You can create groups of records to...

Intro to Nonprofit Cloud
If you’re a Salesforce fan or just plugged into nonprofit tech, you have likely heard rumors about Salesforce’s change to...

Supercharge Dynamics 365 with Microsoft Co-Pilot
Microsoft Co-Pilot is an AI-powered tool that assists Dynamics 365 users in writing better code and improving productivity. Co-Pilot uses...

NetSuite Grant Allocation with Restricted Donations
Non-Profit organizations can utilize NetSuite to allocate donations with purpose or time restrictions. Purpose restricted donations can be strategically associated...
Prevent Your Sensitive Data from Being Stored in ChatGPT
Artificial Intelligence and a machine’s ability to mimic human speech has always fascinated humankind. Recently, OpenAI’s artificial intelligence language model...

We won the construction job. Now what?
In today’s hyper-competitive construction market, it’s a great accomplishment to win a bid or get awarded a contract. But it’s...

How Sage Intacct Nonprofit Upgrades Decision-Making on Day One
A recent survey highlights why reporting matters more important than ever for nonprofits of all shapes and sizes. The survey...

How to Update the Existing Entity Bank Details of Employee or Vendor Records via CSV Import
The Entity Bank Details is another Custom Record from the Electronic Bank Payments bundle, but the difficulty in performing a...

How to Expose Customer Entity Bank Details in a NetSuite Saved Search
How to Expose Customer Entity Bank Details in a NetSuite Saved Search A Saved Search in NetSuite is an ad...

How to Disable Bank Integrations from NetSuite Payments Bundle
Log into your NetSuite Environment using the Administrative Role. Hover over the ‘Payments’ Center > ‘Setup’> ‘Bank Detail You will...

Linking Projects and Contracts – A Secret Weapon in SaaS
One area in which Sage Intacct excels, particularly compared to other mid-market financial management platforms, is with understanding the realities...

How Microsoft Dynamics 365 Helps You Navigate the Complexities of Working with USAID
The various sub-groups of the Government Contracting industry each have their own rules, regulations, and standard operating procedures. Contractors working...

Highlights From Sage Transform 2022
Billing itself as a true user conference, Sage Transform invites stakeholders from across the Sage ecosystem to gather once a...

3 reasons to replace Dynamics GP now
We know that Dynamics GP will be supported by Microsoft through at least 2028, but many GP customers will start...

Highlights from the Sage Intacct 2022 Q4 Update
Sage Intacct never rests on its laurels. The developers behind this cloud-based financial management platform are committed to continually expanding...

Unleashing the Power of Artificial Intelligence for Middle Market Businesses: How OpenAI can drive growth and efficiency
Artificial intelligence (AI) is revolutionizing the business landscape, and it is not only beneficial to large corporations; middle market companies...

Microsoft’s Deadline – Migrating from Microsoft D365 Modern POS to Store Commerce by October 2023!
We are roughly halfway through Q1 2023, and as such the Dynamics 365 Commerce platform continues to evolve at a rapid...
Every Problem in Healthcare Accounting Has the Same Solution
As the US healthcare industry approaches $3 trillion in revenue in 2022, effective accounting becomes extremely important. Providers deal with...

Leveraging Dynamics 365 for Oil Commodity Pricing and Costs
Many energy and manufacturing clients source and consume commodities to manufacture their end products – tracking average daily costs in...

Sage Intacct + FamilySight – Transforming Family Offices
The most important thing that family offices do is also the most difficult: reporting. Reports encompass all the work the...

Person-Centered Systems: Part 3
So what have we learned? First, in an increasingly decentralized world, where remote work has become more prevalent, it is...

A Microsoft Packed Toolbox for Grants Organizations
If you have been following my series, “A Microsoft Packed Toolbox for Fundraising Organizations,” found here, you may have anticipated...

Blast Off: Space Products Company Launches their ERP of the future with D365 and RSM
This Photo by Unknown Author is licensed under CC BY RSM, a Microsoft Cloud Solutions Partner and leader in providing...
NRF – Retail’s Big Show – RSM Digital Collateral
RSM is excited to be a sponsor at NRF’s Big Show January 14-17, 2023. Visit our NRF event page As...

Microsoft Announces Intune Premium Suite
At this year’s Microsoft Ignite 2022 conference, the tech giant announced that a new, premium version of their Microsoft Intune...

Network Detective Pro and Cloudockit – For Better Understanding and Protecting Your Cloud Environment
As companies move further and further into the world of online work environments, one of the most dynamic solutions to...

Azure Active Directory and Microsoft Endpoint Manager
This article details the Azure Active Directory (Azure AD) and Microsoft Endpoint Manager (MEM) services. RSM recommends Azure AD and...
Profitability and Contract Performance
Operating in the Life Science industry can bring a variety of challenges around the visibility and management of chargebacks, rebates,...
Contract Management: What it means, What RSM Offers
RSM solves the complex life science revenue management process by handling contract management, chargeback adjudication, rebate, and fee processing while...

Product Configurator Part 2 – BOMs and Routes
Introduction This article is part two of a blog series (you can find part one here) covering the product configurator...

Technology in Manufacturing, Augmented Reality
Introduction The performance of manufacturing is essential to a company’s supply chain. Some of the issues manufacturers face today are...
Power BI November 2022 Update
The Power BI November update was recently released, with many new features and visuals being released. Continue reading below to...

RSM named 2022 Sage Intacct Growth Partner of the Year
RSM US LLP (“RSM”), the nation’s leading provider of audit, tax and consulting services focused on the middle market –...

RSM Can Sell GCC-High
RSM provides end-to-end, industry-specific Microsoft solutions for thousands of our clients across the world. We are an award-winning Microsoft Gold...

Is Dynamics GP Going Away?
There has been a lot of confusion about the roadmap for Microsoft Dynamics GP. Several years ago Microsoft shifted Dynamics...

Microsoft Dynamics GP with Nonprofits
Microsoft Dynamics GP allows your nonprofit organization to manage more than just financial statements. With integrated financial management, project accounting,...

RSM’s Prendio-NetSuite Connector New Release
For many life sciences companies, managing lab purchasing is critical to controlling spend and ensuring you maintain an adequate cash...

Power BI October 2022 Update
The Power BI October update was recently released, and it includes many innovative features. Some of the most interesting highlights...

Nonprofit – Benefits of Human Resources Outsourcing for Nonprofits
HRO: Helping Nonprofits Focus on Mission, rather than Administration Nonprofits often have limited financial and people resources, which can exacerbate...

A Microsoft Packed Toolbox for Fundraising Organizations
A Microsoft Packed Toolbox for Fundraising Organizations “A Microsoft Packed Toolbox for Fundraising Organizations” – Part 4 Microsoft Power Apps...
Review of Revenue Contract Management Cycle as it Relates to ERP
RSM is a leading provider of Revenue Contract Management services and software in the Life Science industry. With years of...

Tillamook – RSM Microsoft Client Case Study
Tillamook County Creamery Association is a farmer-owned cooperative based in Tillamook, Ore. Founded in 1909, Tillamook is owned by almost...

Webinar Recap: Managing Transportation Costs with D365 Finance & Supply Chain and RSM’s ProShip Shipping Service Integration
How can a company manage inbound/outbound transportation costs more efficiently? Join RSM to understand what platforms they recommend using to...

TechnoMile – Elevate Conference
We proudly announce that RSM US LLP is the Platinum Sponsor of this year’s inaugural Elevate conference with our partner...

6 Benefits of an optimized quote to cash process that will improve your company’s performance
What is Quote to Cash? Quote-to-cash (also known as lead-to-cash, order-to-revenue, or lead-to-revenue-recognition ) is essentially the journey that customers...
Power Automate – Automatically Move a Note Attachment to SharePoint
Use Case: A user needs to submit a document on the portal by attaching a file to a CRM record....

Webinar Recap: How To Begin the ESG Journey Using Microsoft’s Sustainability Cloud
What is ESG and why is it important? Watch this webinar to understand what ESG is and what it will...

BOTTLE DEPOSIT FEES FUNCTIONALITY – FOOD & BEVERAGE CLIENTS
OVERVIEW With the newly created Bottle Deposit Fee bundle, Food and Beverage companies can easily meet new state regulations to...
Respiratory Diseases
Respiratory diseases are leading causes of death and disability in the world. About 65 million people suffer from chronic obstructive...
Power BI September 2022 Update
The Power BI September update was recently released, and it’s packed with powerful new features. The top highlights include hierarchal...

Actionable Fundraising & Engagement Insights
Non-profits keeping up with the increased need for analytics to address member engagement, member retention, and more… Using data effectively...

Sales Tax on Subscription Revenue: Track it With Sage Intacct
Selling subscriptions to generate recurring revenue is the biggest concept in business right now. After all, why collect payments once...

Webinar Recap: D365 Finance & Supply Chain – Landed Cost Module and RSM’s Trade Profiler
Watch as we discuss how the Landed Cost module in Dynamics 365 Finance & Supply Chain can be used to...

Important Update to The Buzz on Dynamics GP Email Functionality & TLS!
This post has been revised as of 9/23/22 to provide the most current information. In January of 2022 Microsoft announced effective...

A Seismic Shift in Construction Accounting – From Reactive to Proactive
Construction-based companies have always been behind the curve in terms of accounting. Not because they neglect accounting but simply due...

Leveraging Sage Intacct’s QuickStart 990 Financial Reports
One of the most important documents nonprofits deal with is IRS Form 990. The IRS requires all nonprofits with more...
The Buzz on Dynamics GP Email Functionality & TLS
Update: for the most recent details on this topic please view this post, “Important Update to the Buzz on Dynamics...

Pre-year end close tips and tricks for Dynamics GP
Is it too early to start thinking about year end? Absolutely not. For those of you that have survived the...

RSM understands Quality Management challenges in the Food and Beverage (F&B) Industry – Part #1
Have you ever found yourself evaluating the nutrition or ingredient information on a product’s label while grocery shopping? Whether this...

Sage Field Operations – Setting a New Standard
The future of field service is digital. For plumbers, construction companies, industrial equipment installers, and countless other businesses that send...

Landed Cost Part 1
This article is the first in a series that will seek to educate readers to make the best decisions for...

Excel Power Query and Power Pivot with Dynamics 365 Finance and Supply Chain
Businesses and users will have requirements to combine various data sets for ad-hoc reporting needs. These data sets could include...

Key Financial Metrics for SaaS Companies
The Software as a Service (SaaS) industry finds itself confronted by opposing forces. On one side is opportunity. The COVID-19...

Top Priorities When Upgrading Healthcare Accounting Software
Accounting could not be more important in an industry like healthcare where costs and revenues are both substantial and the...

Webinar Preview – Managing Transportation Costs with D365 Finance & Supply Chain and RSM’s ProShip Shipping Service Integration
On August 30th at Noon CST members from RSM will present how companies can manage inbound/outbound transportation costs more efficiently...
Field Service: Refrigerant Tracking
Organizations with employees who use refrigerant are required by Environmental Protection Agency (EPA) regulations, under Section 608 of the Clean...

Rapid Verification Model – Industrials
RSM’s rapid verification model (RVM) is a model and philosophy which allows RSM to deliver consistent industry solutions in a...

The final countdown to ASC 842 lease accounting compliance
For calendar year companies, there is less than six months left to implement the new ASC 842 lease accounting standard....

Webinar: Understanding Asset Leasing in Microsoft D365 Finance & Supply Chain and the Impact of ASC 842
This webinar discusses upcoming lease accounting standards and RSM’s approach to minimizing the compliance challenges along this new road map....

Webinar Preview – How to Begin the ESG Journey Using Microsoft Sustainability Cloud
On July 26th at Noon CST, we will be presenting: How to Begin the ESG Journey Using Microsoft Sustainability Cloud....

User Email Policies in Dynamics 365 Business Central
In the twentieth version of Business Central, the new email setup functionality that was once optional is now the required...

Webinar: Prevedere – Advanced Predictive Planning for Food & Beverage
Planning and forecasting your business future solely on historical data has shown to be a challenge and ineffective in today’s...

Security Filters in Dynamics 365 Business Central
There may be scenarios when you want certain users or groups of users to access specific data in a given...

Evolution of Maintenance – Predictive and Prescriptive Maintenance
Predictive and Prescriptive Maintenance A preventative maintenance strategy is the most commonly used strategy in the food and beverage industry....

Sage Intacct – Making Processes Perfect at Family Offices
A family office’s value is measured in consistency. They must meet ordinary obligations with the same high levels of efficiency,...

FX Intercompany AR/AP Revaluation
Companies that transact in foreign currencies may run into intercompany reconciliation issues. There can be many reasons for these differences,...

Join RSM at Community Summit North America this Fall
Dynamics Communities Summit : Oct 10-13, 2022 We would like to invite you to join RSM at this year’s Community...

Tech Tip: Verify Mekorma Product Keys at Renewal
RSM clients experiencing issues with Mekorma should verify that the updated product keys are applied after renewal anniversary and before...
Changes to Office 365 that will impact Dynamics GP email and workflow functionality
Recently Microsoft announced security changes to Office 365 and Exchange Online. Effective October 1, 2022, Basic Authentication protocols will be...

A Microsoft Packed Toolbox for Fundraising Organizations
Part 3: A Microsoft Packed Toolbox for Fundraising Organizations – Power BI Previous blogs in this series Part 1: Dynamics...

US Government Space Contractors Recognize Rapid Results and Expanded Capabilities with D365 Finance & Supply Chain
Space Contracting is an area of the market experiencing rapid investment and growth. These companies encounter unique requirements related to...

Evolution of Maintenance – Reactive & Preventative Maintenance
Introduction The Food and Beverage industry is challenged with producing safe, high-quality products at the lowest cost while following strict...

Healthcare KPIs and Dashboards – More Important Than Ever
Finance leaders in healthcare face a rough road ahead. The COVID-19 pandemic left many providers in a precarious financial position...

Foodborne Diseases
What is a foodborne disease? Foodborne diseases are the result of bacteria, viruses, prions, or chemicals entering the body through...

New Features Make Sage Intacct a Top Choice for Construction & Real Estate Accounting
Sage Intacct releases a free update once every quarter that improves, updates, and adds to the financial management platform in...

What to Expect When Moving Ground to Cloud – GP/NAV to D365 Business Central
Is it time for you to move to the cloud? In this webcast, we talk through key decision points and...

Using Budgets in NetSuite
Budgets in NetSuite will be specific to a fiscal year and permits the entry of an amount per account for...

Data Driven Production Scheduling
Data driven production scheduling In many manufacturing enterprises, effective utilization of installed capacity is of paramount importance. One of the...

Tips and Tricks for Using Sage Intacct Like a Pro
When it comes to a financial management platform as comprehensive and capable as Sage Intacct, it’s hard to appreciate just...

Microsoft Innovation Summit (June 14th)
Event overview As a Microsoft user, you need to stay current with the latest the product has to offer. RSM...

What is Engineering Change Management?
In today’s manufacturing environment, products need to be managed for improvements and issue resolution in an efficient and effective process....

Webinar: Cloud-based ERP – Take IT modernization to the next level
Thu, May 12, 2022 – 1 p.m. EDT | Noon CDT Register Here Event overview IT modernization can provide remarkable...

Tips for Keeping Budget Managers Informed With Sage Intacct
Dashboards are one of the most transformative business tools of the last several decades even if the concept behind dashboards...

NFP Industry Event Highlights and Takeaways
As a subject matter expert in the not-for-profit (NFP) industry, attending industry specific events is critical. It gives the RSM...

Sustainability and the Mid-Market Company
For years sustainability has been seen as something that is a personal choice. If an individual is worried about the...

2022.1 Release Notes and Benefits for Technology, Media, and Telecommunications Companies
NetSuite’s Release 2022.1 is in process of being deployed to all NetSuite instances. Within this blog we’ll focus on the...

American Express Integration for Expense Reporting
With the American Express (AMEX) Corporate Card Integration SuiteApp, NetSuite can automatically import expenses charged by employees to their corporate...

Volunteering with Fundraising and Engagement
A common challenge associations face is not having one common source of truth for all their incoming data. For instance,...

Webcast: Analyzing data with NetSuite SuiteAnalytics Workbook
Does your organization struggle with report visualization in NetSuite? Are you currently exporting saved searches and reports to Excel in...

Fundraising: Seize the (Awkward) Moment with Five Simple Steps
Nonprofit organizations are driven to success largely by two factors: individual passion and generous donations. Interestingly, although these two vital elements...

Sales Lead Time
Delivery date control/order promising Order promising is functionality within D365 that saves time by calculating the ship and receipt dates...

Industrials: Warehouse Comparison Webcast
Do you struggle with warehouse efficiencies? Do you struggle with pick, pack and ship processes, barcoding or inventory management? The recorded webcast...
Upgrading to Classic Workspaces in Power BI
Workspaces are areas within Power BI where you can collaborate with colleagues and clients to create a collection of dashboards,...

The Benefits of a Single Platform Solution
Epidemiologists at state and county health departments face several challenges as they embrace cloud applications to conduct disease management. Migrating...

Learn how to Embed with Power BI Embedded
Power BI embedded has been created by Microsoft for Independent Software Vendors (ISVs) who want to embed visuals into their...

The Many Sides of Sage Intacct Reporting
The rich reporting features in Sage Intacct distinguish themselves in a number of ways. For one, they are intuitive enough,...

Sage Intacct – Release for Restriction Feature Explained
Nonprofit accounting has a number of unique requirements. Sage Intacct is one of the few financial management solutions on the...
Listing Records Related Through an N:N Relationship in Power Automate
N:N relationships can be a great way to identify related records, however, they don’t provide us much value in the...

Ignoring Null Fields When Mapping Field Values in Power Automate
Automating standardized record creation can save users a great amount of time. Traditionally this is easier using legacy workflows, so...

Staffing firms thrive amid wage inflation and labor shortages
Staffing firms continue to adapt to challenges caused by the pandemic, becoming more agile and tapping into new revenue streams...

Environmental services and the $1.2 trillion infrastructure package
President Joe Biden on Nov. 15 signed a $1.2 trillion infrastructure package—The Infrastructure Investment and Jobs Act—that provides historic funding...

Respiratory Diseases
Respiratory diseases are leading causes of death and disability in the world. About 65 million people suffer from chronic obstructive...
Determine If Records Were Returned From A List Rows Step in Power Automate
Querying for the existence of records is a common requirement. If you are familiar with the ‘list rows’ step, you...
NetSuite Statistical Accounts and Schedules
Utilize the Statistical Accounts feature in NetSuite’s Advanced Financial module to enable tracking non-monetary data to include in financial reporting....

Take Advantage of Sage Intacct Efficiencies in a Work-From-Home World
The work-from-home world is upon us. Research suggests more than 36 million Americans will work remotely by 2025, double the...

A Microsoft Packed Toolbox for Fundraising Organizations
Part 2: Dynamics Marketing In part one of this blog series an overview was provided of RSM’s engagement with a...

Harvest scheduling: Unique challenges for the produce industry
Today, an effective supply chain has never been more important. Growing transportation costs, evolving weather patterns, and worker shortages can...

Tips on How to Integrate your Event Management Solution with your D365 Accounting System
Not-For-Profit organizations often face challenges retaining and engaging donors in a way that provides the capital necessary to successfully execute...

Harnessing Digital Strategies to Break Down Nonprofit Silos
Modern nonprofits understand that cross-program initiatives are key to promote fundraising efforts, rally volunteers, and reach previously untouchable donor segments....

Improving Reporting for a Family Office
Reporting ranks as one of the highest priorities for a family office. Anyone who trusts another party with their financial...

Tableau Integrates With Sage Intacct for Fresh Perspectives on Finance
Tableau ranks as one of the leading visualization solutions on the market. It takes raw data and turns it into...

NetSuite Fixed Assets Capitalization Threshold Customization
Overview Natively, the NetSuite Fixed Assets Management (FAM) module does not accommodate the use case where a subsidiary’s capitalization threshold...

Leveraging Technology and the Influencer Effect for Nonprofit Advancement
Nonprofit organizations play a pivotal role in the development of stronger, safer communities by providing crucial services that fortify socioeconomic...

Center Tabs: Customizing Center Tabs and Center Links
NetSuite provides the user with the ability to customize their center menu with specific tabs, both native to NetSuite as...

MEA Allocations Automate Routinely Shifting Costs
A cloud ERP system gives your business a fresh start with the best user interface. With Sage Intacct, clients rely...

What’s New with Sage Intacct 2021 Release 4
Sage Intacct 2021 Release 4 is packed with features that will deliver time savings, increase accuracy, and provide improved functionality...

Review of Upcoming Automation Improvements and Enhancements with Sage Intacct
Upcoming Automation Improvements and Enhancements with Sage Intacct The digital age has made a profound difference in accounting software solutions....

Intelligent GL Outlier Detection is Digital Transformation
Sage Intacct Intelligent GL already provides extensive visibility, scalability, and flexibility companies need to grow their business. Outlier Detection for...

NetSuite 2021.2 SuiteBilling Enhancements
Prior to 2021, the software industry was already on a steady pace to cloud-based applications, but the past year raised...

How Dynamics 365 Commerce is changing how we shop for our favorite items
After a year of unprecedented disruptions to store operations, a store’s role in merchant strategy is changing and being reinterpreted....

The 3 most asked questions about Dynamics 365 e-Commerce
As the digital retail landscape evolves, new challenges and opportunities are emerging. Microsoft Dynamics 365 e-Commerce is a powerful application...

IT modernization through ERP innovation
IT modernization doesn’t have to mean replacing all of your technology. Modernizing core applications such as ERP can lead to...

User Permissions in Microsoft Business Central
Microsoft Dynamics 365 Business Central has tremendous flexibility in how you can set up permissions. The application provides many pre-defined...

Microsoft releases new Dynamics GP Modern Lifecycle version for year end close
Year-end brings with it many different events… with luck these events will include holidays, family and friends, and fresh starts. ...

Use Different Document Layouts for Customers and Vendors
Did you know that in Business Central you can create custom report layouts and assign them to either your customers...

Capital One Integrated Payables
We have had several requests to assist clients with generating an ACH file out of Microsoft Dynamics GP in the...

Bank Reconciliation Page vs Bank Rec. Worksheet in Business Central
I’ve been hearing that there is some confusion around the bank reconciliation process in Microsoft Dynamics 365 Business Central. It...

Expand your Business Central Account Schedules with the use of Analysis Views
Are you only using the global dimensions in your Business Central Account Schedules? Do you want to expand the Account...

Understanding headless commerce
How Dynamics 365 Commerce can support effective headless commerce Customer buying patterns can change rapidly, and that has become even...

How to create intercompany transactions in Business Central
How do intercompany transactions work in Business Central? I decided to write this blog, as several people have asked how...
Make Reconciling Credit Card Statements and Sweep Accounts easy in Business Central
Make reconciling credit card statements or sweep accounts easy with Payment Reconciliation Journals in Business Central You can use the...

Transform Microsoft Dynamics 365 Finance with Kyriba Payments
Tuesday, October 19th 12pm ET / 9 am PT 1.2 CTP Credits Blossoming companies using Microsoft Dynamics 365 are running...

Exchange Rate Service
The following is a walkthrough of how currency exchange rate updates can be automated in Business Central. FloatRates is a...

Creating General Journal Reversals and Copies in Business Central
Many times, I have been asked about creating reversal general journal entries in Business Central. A lot of people think...

How do you know all journal lines have been posted?
In Microsoft Dynamics 365 Business Central, you create journals for entries such as general journals, item journals, fixed asset journals,...
CRE Change Management Advanced Features Coming Soon
Sage Intacct is working on something so beneficial to our clients’ businesses that we want to give you a sneak...

How to Find All Your Dimension Values on General Ledger Entries
Looking for All Dimension Values on General Ledger Entries Are you using more than just the two Global Dimensions in...

Are You Still Processing Computer Checks from Dynamics 365 Business Central Rather than EFT Payments?
Do you find it difficult to get payments out to your vendors? Many companies have been finding it difficult to...
D365 Reconciliation – Inventory Value (GL and SL on a same page)
While you are waiting to enable the new feature [Inventory Value Report Storage], this blog quickly covers the setup for...

Microsoft’s new intelligent omnichannel solution is here to transform your omnichannel experience
Microsoft recently announced the general availability of their latest cloud-based solution for Dynamics 365 that has the goal of making...

What to expect in Dynamics 365 Business Central’s 2021 Release Wave 2
Yes, it is that time of year again. The next release will be out soon. I am so looking forward...

Are the numbers real? D365 Financial Reporter out of balance trick.
Embarrassed by publishing D365 Financial Statements that do not match the Trial Balance? Do not fear, this simple trick will...

Yeah, say Ledger again. General Ledger > Setup Ledger > Ledger
At a high level, a new D365 company needs to tie certain information together for the company to process any...

Don’t wait to start planning for year end!
Year end will be here before we know it. It is not too early to start planning, and RSM can...

Dynamics Community Summit returns!
RSM is excited that the Dynamics Community Summit (formerly called Dynamics UG Summit) is returning this Fall. This year Dynamics...

Data Management EXPORT, Validate your D365 Chart of Accounts
Microsoft Office Export to Excel usually only shows a few of the fields, but you want to validate all of...

Best Closing Practices for Nonprofits: How to Use Intacct’s New Checklist Feature
Have you experienced the power of Sage Intacct’s Checklist and Assignment feature for your month-end or quarterly internal financials? As...

Intacct’s 2021 Release 3 Highlights
With a theme of time savings and proficiencies in automation, Sage Intacct 2021 Release 3 offers several exciting enhancements for...

Automated Accounting Part 12, Bank to Bank Transfer Journals
D365 is to post bank transfers in a single journal without using a clearing account if you attempt to post...

Intercompany Journal Entry: Migrating Offline Financials to NetSuite
What is an Advanced Intercompany Journal Entry? An advanced intercompany journal entry is a specialized record type available only in...

Automated Accounting Part 11, Yes, you can actually Post a PO Receipt for Procurement Categories
PO Receipts appears to work just fine when receiving inventory, just doesn’t appear to post anything in General Ledger for...

Sage launches new Finance Superhero Series
Join us and Sage Intacct this Fall for their recently launched Finance Superhero webcast series! In this series you’ll learn...

Automated Accounting Part 10, Foreign Currency Translation & Reval in a Consolidation Company
In a previous blog, we talked about posting foreign currency transactions. Today we are looking at a different angle. We...
Usage Billing in Sage Intacct
Usage-based billing allows companies to bill customers based on their use of a product, which means as usage varies, so...

Easy Accurate D365 Transactions via Pivot Tables instead of “T” Accounts
This blog provides an accurate and easier alternative to manually preparing “T” accounts from your D365 Vouchers. “T” accounts are...

Automated Accounting Part 9, Foreign Currency Transactions
Our goal today is to post transactions in a foreign currency and automatically record the exchange rate on a transaction....

Payment Reconciliation Journals in Business Central
Did you know you could use the Payment Reconciliation Journals to perform tasks beyond just a simple import of a...

How Sage Intacct’s Report Writer Can Make Franchise Businesses More Efficient
Due to the number of individual entities they operate, franchise companies have countless specialized reporting needs. Using an older accounting...

RSM announces the new quarterly Dynamics Innovation Summit
RSM is excited to announce our inaugural Microsoft Dynamics Innovation Summit, which will kick off at 1:00pm Eastern on Tuesday,...

Hot Off the Press, Microsoft D365 2021 release wave 1 plan
Microsoft periodically delivers automatic Dynamics 365 Updates. This keeps your ERP system up to date with the latest and greatest...

Automated Accounting Part 8, Interunit-debit & Interunit-credit (… Balance Sheets by BU)
Our business scenario today is automating balancing of a Financial Dimension: Business Unit. We have decided to proceed using a...

How Sage Intacct’s Report Writer Can Make Franchise Businesses More Efficient
Due to the number of individual entities they operate, franchise companies have countless specialized reporting needs. Using an older accounting...

How Sage Intacct Dashboards Can Benefit Family Offices
Accounting for family offices includes a wide range of needs. Sage Intacct dashboards can help manage them more effectively. Dashboards,...

Automated Accounting Part 7, Fixed Asset Proceeds on Cash Flow Statement
Today we will look at the Sale of Fixed Assets and how to separate the disposal on the trial balance....

Automated Accounting Part 6, Entangled Customers and Vendors
Now, why would we want to do that? This is an introductory setup for processing D365 Intercompany Purchase and Sales...

Webinar – Seven Reasons 7-Time NetSuite Partner of the Year Recommends Kyriba
Financial organizations of all sizes on Oracle NetSuite are supplementing, reducing financial risks, and empowering their treasury teams by bolting...
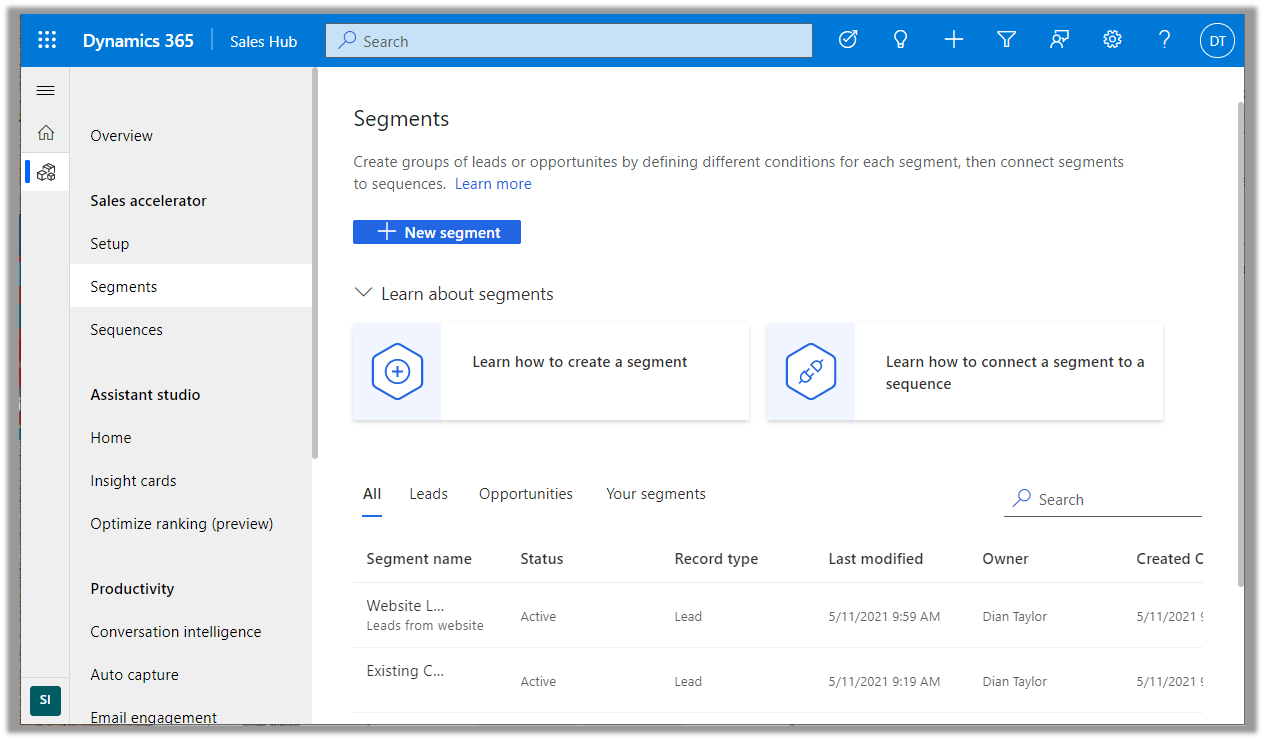
What’s new with the Sales Accelerator
The Sales Accelerator is part of Dynamics 365 Sales and to get access to it you’ll need to have a...

Automated Accounting Part 5, Intercompany Customer Payments
Today we will expand on the last post in the series by adding functionality for Recording Cash Receipts in one...

Check order status with Power Virtual Agent and Power Automate
I get a lot of requests where my prospects want Power Virtual Agent to be able to answer questions about...

What is a work order?
A work order is a request for a technician to be scheduled to complete a task or a job. The...
Don’t be afraid of Father Time. D365 Year End Close.
The short and sweet Year-End Close creates beginning balances for the new year’s Trial Balance. There is no need to...

Updated Dynamics GP Roadmap
On July 8, 2021 Microsoft released the below updated roadmap for Dynamics GP. We are excited to see Microsoft’s commitment...

Why you should consider adding multiple pickup methods for customers shopping at your retail establishment
Retail is ever-changing and evolving, becoming more manageable and more frustrating at the same time. In 2020, when the Covid-19...

Part 1: Sale of Service Agreements
Industrial sector companies often produce and sell products that need servicing over time. These services could include routine inspections and...

Automated Accounting Part 4, Intercompany Ledger Journals
Today will focus on automating Intercompany Ledger Journals. We want D365 to automatically fill in the related Intercompany Receivable and...

Automated Accounting Part 3 – Inventory Posting Profiles, Production Orders
Today we will be bridging the gap between the Purchase and Sales Orders and dive into the Inventory Posting Profiles...

New! Directly Integrate SAP Concur with Sage Intacct
One of Sage Intacct’s strengths is how well it works with the other systems your company uses. Direct integration with...

Sage Intacct 2021 Release 2 Highlights Offer Increased Efficiency and Learning Opportunities
Sage Intacct users will likely be giving the latest quarterly release two thumbs up. In fact, at least one of...

New Master Planning Optimization Add-in for D365 Supply Chain Management
We all know that Master Planning is extremely helpful in facilitating companies’ important information such as raw material availability, capacities...

Microsoft to Launch New Cloud Promotion for Legacy Customers
On September 1, 2021, Microsoft will launch the Bridge to the Cloud promotion through the Cloud Solution Provider (CSP) program....
Working Remotely with Microsoft Dynamics GP
Covid restrictions may be starting to lift around the country, however, according to a recent survey only about 1 in...
Microsoft Throttling in D365 Finance and Supply Chain
Microsoft is enabling throttling on oData and custom web services to D365 F&S, which will require investigation by all D365...

An Easy Method for Reviewing Funds and Multi-Year Grant Balances in Sage Intacct
Does your nonprofit organization struggle to easily find your ending grant balances for a certain period? Do you need to...
Automated Accounting Part 2 – Inventory Posting Profiles, Sales Orders
Today we will be reviewing automation of accounting for Sales Orders. We want D365 to automatically code the following journals:...

Automated Accounting Part 1 – Inventory Posting Profiles, Purchase Orders
So, what are posting profiles? They are the Dynamics 365 configuration of automatic transaction journal entries. These setups are the...

Offline Warehousing with Dynamics 365 Supply Chain Management
Many organizations need to run mission-critical processes around the clock without interruption. Cloud and Edge scale units enable manufacturing and...
Scribe Online Adapter convert to Azure AD – Client Credentials
Prerequisites D365 online Scribe Insight 7.9.5 or newer Scribe Adapter for Microsoft Dynamics CRM 562 HF 14 Azure AD App...
Your super user is leaving, now what?
There is a reason organizations ask for two weeks’ notice. When a key resource decides to leave an organization, a...

Optimize and Empower Your Transactions with NetSuite Advanced PDF
Your outgoing transaction documents should look exactly the way you want them to. Representing professionalism, increasing usability, and transforming how...

Top Six Metrics and KPIs for SaaS Companies to Monitor in Sage Intacct
Specific metrics define success for software as a service (SasS) companies. Whether you want to secure additional funding or are...
Dynamics GP – Payables Trial Balance Reports Missing Vendor Invoices after GP18 Update”
Several of our clients noticed some vendor invoices not yet paid had dropped off the aging reports after updating to...

Microsoft Dynamics GP – Error on Payroll Tax Filing Status
When running the Payroll Calculate Checks process in Dynamics GP, you receive an error: “The tax filing status record for...
Microsoft Dynamics GP Permission Errors Running Reports After Upgrading to GP 2018 & GP 2016
You’ve just recently upgraded Dynamics GP, and when running a report, you receive the error: “Not privileged to run this...

Memorized Transactions: Creating a Memorized Transaction for a Specific Date
A memorized transaction in NetSuite enables the user to set up a transaction to recur automatically in the system. Memorized...

How Family Offices Can Benefit From Working With Sage Intacct and RSM
The financial interests of family offices can be quite complex. Partnering with RSM can help your family office work more...

Use Different Document Layouts for Customers and Vendors in D365 Business Central
Did you know that in Business Central you can create custom report layouts and assign them to either your customers...

Management Reporter – DataMart Rebuild & Reconfiguring Change Tracking
If you’ve discovered missing or bad data on your Management Reporter reports or have some other reason that you need...

Microsoft Dynamics GP – Error “Asset ID is required.”
The user attempted to delete a Fixed Asset in GP and received an error message that the “Asset ID is...

More Information on the Banking Updates to Business Central in the 2021 Wave 1 Release
As I mentioned in my last blog about Business Central, there are some exciting updates for bank reconciliation in the...

Two-factor authentication (2FA) for NetSuite
Two-factor authentication (2FA) allows enforcement of the second level of security for logging in to the NetSuite user interface. Using...

Microsoft Dynamics GP – Error Opening Customer/Vendor Consolidations Window
You’re receiving the following error when trying to open the Customer/Vendor Consolidations window, “Your previous transaction level posting has not...

Connection Options for getting Dynamics 365 Sales Data into Power BI
Microsoft Dynamics 365 Sales is a model-driven app that enables users to build strong relationships with customers, discover insights to...
Setting Up Pending Approval Email Template
The Email Template tab in NetSuite enables users to customize messages to allow for notifications sent directly to their emails....

Setup and configuration for Engineering change management functionality – Part 1
How many times have you had users in the system who make unauthorized changes to a released product that caused...

What’s planned for Business Central in the 2021 Wave 1 Release?
I am so excited for the next wave release. I think you will agree that these are fantastic updates to...

NetSuite Outsourced Manufacturing – Configuration & Demo
Overview NetSuite 2020.1 release introduced Outsourced Manufacturing, a solution for companies that use a third-party contract manufacturing organization (CMO) within...

Sage Intelligent Time Named One of The 2021 Top New Products By Accounting Today
For service-based companies, tracking employee time is not as simple as asking them to clock in and clock out. Poor...
Effective Date Pricing SuiteApp
The Effective Date Pricing SuiteApp enables you to set a schedule for specific price changes in advance. NetSuite SuiteApps are...
Dynamics GP Payroll – New Federal Filing Status Options
In 2020 Microsoft rolled out some new Federal Filing Statuses for Dynamics GP Payroll. The 5 new filing statuses that...

How NetSuite Multi-Book Translates Functional Currency to Foreign Currency for Reporting Purposes
Many companies have foreign subsidiaries where GAAP requires the functional currency to be the US Dollar, but where there continue...

New Release Perspective: NetSuite Updates Targeting Tech, Media & Telecom
Recent NetSuite enhancements increase efficiency and automation for companies within the Technology, Media and Telecom (TMT) sectors. This article reviews...
How Do I Set a Lookup in the CDS/Dataverse Connector? You Don’t!
Last year, Microsoft released a new Common Data Service Connector aptly suffixed with ‘(Current Environment)’. Though the connector gave us...

Master Planning Item Coverage – Part III
Previously, we discussed the coverage groups in Master Planning and went through the other tab of the form. In this...

Sage Intacct Construction Continues to Build New Features to Meet User Needs
As the construction industry continues to adapt to the new world emerging from the fallout of the pandemic, more companies...

Previewing Azure Purview
What is Purview? We are going to be talking about Azure Purview in this post. No, that is not a...

Working Smarter with Sage Intacct 2021 Release 1
Among the many benefits of Sage Intacct are the quarterly updates which offer new features and functionality, helping your company...

Installing Bank Feeds and Setting up Financial Institution
The Bank Feeds SuiteApp enables the User in NetSuite to automate the upload of their bank and credit card data...

Dynamics NAV/Dynamics 365 Business Central Remove Access to General Ledger Entries with standard Permission Sets
“…But they shouldn’t be able to see General Ledger details.” If you’ve implemented Dynamics NAV/D365 Business Central you’ve heard that...

Dynamics 365 CE Bulk Delete Duplicate Records with Power Automate
Duplicate Detection rules in Dynamics 365 Customer Engagement (CE) are great for preventing duplicates, but aren’t helpful once you already...

Security and Controls for Dynamics GP
Fastpath and RSM Do you question if your GP environment is actually secure? Do you wonder if users have unauthorized...

RSM & Emburse Partnership Announcement
We are excited to announce that we are now partnered with Emburse, the market leader for expense management and accounts...

NetSuite Update: 2021.1 release notes are here
As you may have noticed during your last login, NetSuite has announced their 2021.1 release dates. You can find the...

NetSuite New Release Facts 2021.1
The New Release Portlet Will Provide Important Resources: Release Preview Date When your Release Preview/Demo environment will be ready. This...

Getting to know our MVPs – Dian Taylor
Becoming a Microsoft MVP takes a lot of time and discipline with a dedication towards supporting the business applications community...

Getting to know our MVPs – Seth Bacon
Seth Bacon had a busy year in 2020 with one of his many accomplishments being named a Microsoft MVP for...

Native Sage Intacct and Salesforce Integration for SaaS Companies
The software as a service (SaaS) market continues to grow as more and more businesses are shifting away from their...

How Sage Intacct Dimensions Can Support Faith-Based Organizations
Whether your faith-based organization is managing day-to-day operations or preparing for growth, its specialized accounting needs can be a lot...

Master Planning Item Coverage in Dynamics 365 Supply Chain Management – Part II
Last month we discussed the coverage groups in Master planning and went through its General tab. In this article, we...

Track Encumbrances and Commitments With Sage Intacct’s User-Defined Books
January is an ideal time to take a look at how your company handles its budget. User-defined books in Sage...

How Associations Can Use Sage Intacct for Greater Efficiency and Increased Visibility
Many associations depend on outdated accounting systems, which makes operations less effective and even limits potential membership growth. With Sage...

Intercompany Netting in NetSuite Release 2020.2
The 2020.2 release delivers a host of long-awaited enhancements to intercompany functionality. While some improvements target the complexities of multi-currency...

Master Planning Item Coverage in Dynamics 365 Supply Chain Management – Part I
Master planning in Dynamics 365 Supply Chain Management can be confusing for those who are learning to use it for...

Sage Intacct 2020 R4 highlights: outlier detection, updated AR interface, and more
In a time filled with uncertainty, you can still count on Sage Intacct’s quarterly releases to add features and functions...

Improve Your Foundation’s Reporting with Sage Intacct
Is your foundation managing grant reporting, restricted schedules and cost-reimbursable tracking manually? For increased accuracy and efficiency, these processes can...

Top 5 Features of Microsoft D365 Commerce – e-commerce and One Functionality Gap
Since before Microsoft’s e-commerce platform became generally available RSM’s team has been leading the way in developing with Ste Michelle...

Sage Intacct Construction and Real Estate: Building More Efficient Financial Management
Your company needs the right tools to get the job done. Sage Intacct Construction and Real Estate was developed to...

Azure Express Route Considerations
Middle market organizations are deploying Azure Express Route to provide reliable, low latency connections between their primary office(s) – where...

The Best Thing about Sage Intacct Budgeting and Planning? Saying “Goodbye” to Spreadsheet Headaches and Busy Work!
Saying “Goodbye!” to spreadsheet headaches and busy work is indeed a benefit that Sage Intacct Budgeting and Planning provides, but...

Time to Prepare for Regulatory Reporting to the IRS
It is that time of year again where we start thinking about preparing for our year end closes and generating...

Take your fundraising beyond Giving Tuesday
While we have just finished up with Giving Tuesday, it is just a reminder of how much fundraising impacts your...

Are You Ready to Close Your Fiscal Year?
Many companies will have a fiscal year that closes on December 31st and will need to process their year-end close activities. ...

Dynamics 365 for Operations: The numerous uses for project contracts is staggering
Blog Series Part 5 – Contract Progress Billing Rule As you may recall, in Part 3 of this series I...

What’s New in Dynamics GP? October 2020 Release Features
With the most current release of Microsoft Dynamics GP that came out last month, many new and exciting features and...

Sage Intacct 2020 R3 highlights: credit card feeds, inactivity reminders, and more
With each quarterly Sage Intacct release, there is a lot to get excited about. This is especially true for 2020...

Five things we learned at Sage Intacct Advantage 2020
Sage Intacct Advantage 2020, held virtually this year, was packed with information, updates, tips and tricks. With travel costs taken...

Grow Customer Relationships at Scale with ERP data and Customer Insights
Use your ERP for customer discussions Omni-channel retailers capture customer data across transactions and online ad and web engagement. Using...

Identifying NetSuite SuiteCommerce Advanced (SCA) Version
When working on a NetSuite e-commerce website, identifying the platform and version is a critical first step. There have been...
Power Automate CDS Option Sets: Where are my labels?
Microsoft has positioned the CDS current environment connector as the one to use and that connector has given us a...

Planning Optimization in Dynamics 365 Supply Chain Management
For those of you involved in running Master planning in Dynamics 365 Supply Chain Management, you know the drill: schedule...

Power Automate Date Filtering on Today’s Date
Using Power Automate I often need to filter records based on date to find only those matching a certain date....

Salesforce and Sage Intacct: the Sales and Accounting Dream Team
Sage Intacct and Salesforce are like peanut butter and jelly — great by themselves but even better together. A pre-built...

Dunning Email Templates: Adding Custom Transaction Fields to the Email Template
The Dunning Letters SuiteApp enables NetSuite users to set up automated dunning processes in NetSuite to help manage the collections...

NetSuite SuiteSolutions Are Now Free
In Early 2019, NetSuite announced that they would be providing all SuiteSolutions to customers at no additional cost. SuiteSolutions are...

Microsoft Dynamics Fundraising and Engagement – Part 2
This is the second blog in a series devoted to Microsoft Dynamics Fundraising and Engagement. The first blog introducing this...
New IRS form 1099-NEC: What it Means for Dynamics GP
The IRS has released a new form 1099-NEC (non-employee compensation) which replaces using Box 7 of the 1099-MISC form from...

Microsoft Dynamics Fundraising and Engagement is released!
Microsoft recently included Fundraising and Engagement as part of its Dynamics 365 offering for the Not For Profit community. This...

The Miami Heat are using Microsoft technology to change the customer experience
As the Miami Heat march through the playoffs, their fans hang on every shot, dunk, and block. Microsoft technology has...

Power Automate Flows: Adding Properties to Arrays
Recently, a client requested something in their Business Central integration: Show us the company for each record you are integrating....

OpenAir: Custom Utilization Reporting
One common request our clients have is to create a custom calculation for utilization reporting. In this example, we will...

4 Critical Challenges that all Life Sciences Firms Can Solve with Technology
Whether they are developing new drug therapies, designing innovative medical devices, or creating more accurate medical diagnostic tools, organizations that...

How to embed PowerApps into Dynamics 365 Dashboards
Dynamics 365 is already a robust suite, but what if you could get access to your data faster and in...

Using Assignment Groups in OpenAir
An Assignment group is a list of employees selected from all the active employees in the system. Assignment groups allow...
Dynamics GP Technical Support Alert, Word Template and eOne SmartConnect Errors
Many of our clients have recently reported receiving errors in Dynamics GP & eOne’s SmartConnect related to a recent Microsoft...

Realize the Power of your Data with Intuitive Reporting
The wide range of reporting possibilities in cloud-based accounting solution Sage Intacct gives users easy access to a significant amount...

OpenAir Custom Calculations and Reporting
A custom calculation allows you to create a more specific calculation in the system than what comes out of the...

Using Descriptive Analytics to Improve Decision-Making
For optimized insights into both your current operations and future growth, your company needs both descriptive and predictive analytics. Sage...

RSM’s National Dynamics GP Support Moves to World-Class Service Now Platform
Are you experiencing delays getting support from your Dynamics GP solution partner? If so, wait no longer. RSM’s National Dynamics...

Customizing Transaction Email Templates to “Include Transaction”
When sending emails out of NetSuite via workflow, one great feature is the ability to include an Email Template as...

Webinar – Connect your supply chain and deliver amazing customer experiences
Optimize operations and engage customers with Microsoft Dynamics 365 October 7, 2020 2:00 PM Eastern Time (11:00 AM Pacific Time)...

Automating Use Tax Calculation with a Workflow in NetSuite
Use tax is a sales tax on purchases made outside one’s state of residence for taxable items that will be used, stored or...

Modifying Your Subsidiary Hierarchy
Purpose Modify the existing subsidiary structure to add additional roll-up/parent subsidiaries, a new subsidiary becomes the parent entity or you...

Creating Custom Email Templates for Electronic Payment Notification
This article outlines some tips and tricks to use when setting up email notifications to Customers, Vendors, and employees when...

Common Data Service (Current Environment): Now Outside of Solutions!
Have you been working hard on your Power Automate Flows for CDS/Dynamics 365 Sales outside a solution only to find...

NetSuite Update: 2020.2 release notes are here
As you may have noticed during your last login, NetSuite has announced their 2020.2 release dates. You can find the...
Add Dynamic Hyperlinks in Emails Sent by Microsoft Power Automate
Microsoft Power Automate is a powerful tool with many capabilities to help automate your business processes. By using Microsoft Power...

NetSuite New Release Facts 2020.2
The New Release Portlet Will Provide Important Resources: Release Preview Date When your Release Preview/Demo environment will be ready. This...

Customizing Sage Intacct to Expand your Productivity and Efficiency
When you use Sage Intacct, you will find that the cloud-based accounting system can be tailored to meet your company’s...

Dynamics Users: Migrate to the Cloud for Free
Has the sudden switch to full-time remote work had an impact on you and your organization? Well, Microsoft has now...
Extend the Life of your Dynamics GP Solution
Two key reasons a company usually decides to change their accounting system are 1) for better financial reporting and 2)...

Using the new Views functionality in Dynamics 365 Finance and Supply Chain Management
Recently, Microsoft introduced additional personalization functionality in Dynamics 365 Finance and Supply Chain Management that is a total game-changer for...

More Efficient Operations for Professional Service Firms with Sage Intacct
Whatever your professional service firm specializes in, from digital marketing and IT services to consulting and engineering, Sage Intacct is...

Dynamics 365 for Operations: The numerous uses for project contracts is staggering
Blog Series Part 4- Milestone Contract Billing As you may recall, my previous blog, Part 3: Project Contracts, showed you...

Empowering Web Authors: Dynamics 365 Commerce
With the launch of Microsoft’s digital commerce solution earlier this year, the options for hosting e-commerce stores have expanded. An...

Sage Intacct for Success: Five Features that Support Company Growth
As you manage your software or technology company, Sage Intacct can meet your business’s needs today and in the future....
Sage Intacct 2020 R2 Highlights
The second release of Sage Intacct in 2020 includes a wide range of updates, from a game-changing way to manage...

Why does my Cumulative Retained Earnings Exchange Rate look so weird?
I get asked this question a lot from clients when they look at their retained earnings and their Cumulative Translation...

Making the Case for Better B2B E-Payment Processing
New fintech trends are constantly emerging. This can make it difficult to determine which ones are necessary and which are...
Sales and Purchase Agreements in Dynamics 365
First of all, let’s not confuse this topic with trade agreements – which is a very common form that many...

Buy Now, Pay Later with NetSuite
Creating conversions and driving revenue is the ultimate goal of your eCommerce store. Getting customers through the browsing process, into...

Dynamics GP – Stay or Leave?
With the recent increase of attention on the Microsoft Dynamics 365 lineup of cloud applications, my clients often ask me...

Customer Rebates in Microsoft Dynamics 365
Any company that sells products or services to another company usually will offer some kind of incentives at one point...

NetSuite’s Automatic SSL Certificates Will Save You Time and Money
Five years ago, this would be a different blog post than it is today. However, NetSuite has debuted its new...

Dynamics 365 for Operations: The numerous uses for project contracts is staggering
Billing Rules When using project contracts, you have the capability to set up billing rules on the contract. Billing rules...

How to use Parse JSON on SQL Stored Procedure results in Microsoft Power Automate
Microsoft Power Automate can parse the results of a SQL Stored Procedure from an On-Premise SQL Gateway connection, but it...

Project Service Mobile Time Entry Blocked
A client using Dynamics Project Service Automation (PSA) recently highlighted a Time Entry issue. Users on the mobile version of...
Before You Build: Business Central & Power Automate Flows
Microsoft Flow (now under the Microsoft Power Automate umbrella) is a powerful workflow tool that gives you the ability to...

Extending Your SuiteCommerce Site with Google Tag Manager
You are sitting at your desk, making sure products are in stock and your website is prepared for increased volume...

Route Management in NetSuite
The Static Route Management feature in NetSuite allows companies whose trucks operate on predefined routes more visibility into their operations....

How Sage Intacct Helps Family Office Organizations
If you deal with the distinctive issues of family offices, then you know the only constant is change. One day,...

Utilizing SuiteCloud Development Framework (SDF) in NetSuite
Although not a new feature, NetSuite’s SuiteCloud Development Framework (SDF) has not been widely adopted. Below is some information on...

Why Salesforce Plus Sage Intacct Is the Best Solution for Your Software or Technology Company
As you make plans to grow your software or technology business, it’s easy to focus on your big-picture goals. But...

Six Signs Your Company Is Outgrowing QuickBooks
As your business expands, you’ve probably focused on your success. You may not have even realized that your accounting system...

Installing and Setting up Solution7
Installing Solution7 Installing Solution7 requires downloading multiple application files and entering some information, but it is relatively simple as a...

Advanced AMS for Oracle NetSuite: RSMs New NetSuite Association Management Solution
Associations are a vital part of the world’s business landscape. They represent organizations and individuals, professionals, and communities. They have...

Person-Centered Systems: Part 2, Multi-channel Communications
In last week’s blog we discussed the idea of using a Person-Centered approach to designing your CRM system and the...

NetSuite Multi-Book: Adjustment-Only Book
What is an Adjustment-Only Book? An Adjustment-Only Book is a light version of Multi-Book accounting that gives users the ability...
Outsourced Manufacturing (a NetSuite 2020.1 release) is a Game-changer for Life Science Industry
Whether you are pharmaceutical, biopharma, or medical device company and use a third-party contract manufacturing organization (CMO), this new NetSuite...

Dynamics 365 for Operations: The numerous uses for project contracts is staggering
Blog Series Part 2 – Creating Project Contracts When creating a project in D365 F&O, the system requires that a...

Five Key Nonprofit Differentiators with Sage Intacct
If you run a nonprofit organization, you’re always looking for ways to do more with less. When it comes to...

Microsoft Field Service Schedule Board Report
A frequent request by clients is to provide schedule board details when you go to a daily or weekly view...

Dynamics 365 for Operations: The numerous uses for Project Contracts is staggering
Blog Series Part 1 – Building foundational knowledge I started with RSM about 3 months ago and found that there...

How to select alternate printed PDF form at time of printing without scripting or workflow
Often times NetSuite clients have multiple printed forms based on the detail that is being displayed on a specific transaction...

Field Service Scheduling – The Road from Manual to Automated Scheduling
The purpose of this blog is to explain the concepts of Microsoft Dynamics 365 Field Service Scheduling and to provide...

Learning the Microsoft Dynamics GP Table Structure
Whether you are the IT person, a GP power user, or both and tasked with extracting/importing data into or from...

Sage Intacct 2020 Release 1
In 2020 Release 1, Sage Intacct has added features to help you save time and increase the productivity of your...

Person-Centered Systems: Part 1
As we continue to acclimate to the new normal of decentralized work, many find themselves running into the same familiar...

Top 3 Most Useful NetSuite Chrome Extensions
Have you ever wondered if there were any NetSuite chrome extensions that could make your life easier? It seems that...

8 Reasons Your Health Care Business Should Use Sage Intacct
In the health care industry, one thing you can count on is change. As you keep up with the latest...

Microsoft Teams Live Events Offers Affordable Solution to Nonprofit Organizations
As the COVID-19 pandemic continues, strategies employed by governments to slow the spread of the virus have massive impacts on...

Working From Home With Sage Intacct
When you’re working from home, accessing everything you need to do your job can be challenging. If your business uses...

Latest FSLogix release simplifies remote logins for Microsoft VDI admins
Organizations that are equipping remote workers with Virtual Desktop Infrastructure (VDI) are finding that leaps in technology change can roll...

Microsoft Dynamics GP Security Access Processing POP Returns
After years of working with Dynamics GP, I recently encountered one of those unusual security settings that made no sense....

Top 4 Management Reporter Issues
I have been working with Management Reporter (MR) for over 10 years and understand the frustration many of our customers...

9 Ways Using Sage Intacct Can Help Your Franchise Business
When you run a franchise business, its parts are as important as the whole. While you stay aware of your...

How to maximize the use of fair value formulas in Advanced Revenue Management
NetSuite’s Advanced Revenue Management (ARM) module provides users that have more complex revenue recognition capabilities with the ability to allocate...
Dynamics GP Error – “This Transaction is Being Edited by Another User”
You’re trying to open an unposted transaction in Dynamics GP and receiving an error “This Transaction is being edited by...

When a SmartList returns no data and Dynamics GP does not provide an error message
One of the most common issues reported to the RSM Dynamics GP Help Desk is when a SmartList returns data...

Audio Conferencing in Microsoft Teams
In the current working environment that we are in, we are getting quite a few requests for Microsoft Teams conference...

Dynamics GP Error – “This Document Cannot be Marked for Voiding. It Has Been Either Partially Applied or is on Hold.”
This error is one we see come across our support desk a lot. A user attempts to void a document,...

Updates to M365 Licensing – April 2020
The licensing world at Microsoft is always a challenge for our customers to keep up with, as new products, features...

RSM NetSuite Support Desk
As more companies are implementing work from home policies, we face a whole new set of adjustments. We are all...

Dynamics 365 Customer Service: KB Automatic Filtering
I ran into a feature the other day that I thought would be worth writing an article about. This feature...

Dynamics GP Error – “You don’t have security privileges to open this window error message. Contact your system administrator.”
How often does one of your GP users receive a permissions error when trying to access a specific window in...
Dynamics 365 – 2020 Release Wave 1 | Updates
I wrote a total of three articles on the 2020 Release wave 1, which can be found on this blog....

Dynamics GP Login Issue – “This login failed. Attempt to log in again or contact your System Administrator”
Are you having trouble logging into GP? Are you entering your GP User ID and Password and receiving the below...
Dynamics 365 – 2020 Release Wave 1 | Part 3
On January 27 of 2020 the release notes came out for 2020 Release Wave 1 for Dynamics 365 and the...
Dynamics 365 – 2020 Release Wave 1 | Part 2
On January 27 of 2020 the release notes came out for 2020 Release Wave 1 for Dynamics 365 and the...

Auto Numbered Lines
Line Auto-numbering This recipe assigns unique, permanent numeric values to each line on a transaction. It is suitable for correlating...

10 things to consider when relying on Microsoft Teams for the remote worker
Remote working is here to stay (for a while). While most of us are adapting to video calls, pictures of...
Dynamics 365 – 2020 Release Wave 1 | Part 1
On January 27 of 2020 the release notes came out for 2020 Release Wave 1 for Dynamics 365 and the...

New Dynamics 365 Feature – Mass Reversal for Multiple Documents
If you’ve seen the default dashboard for Dynamics 365 since version 10.0.7, you may have seen a new tile called...
Cannot access this report because the dictionary containing it is not loaded in Dynamics GP
Have you ever gone to print a report in Dynamics GP and receive the error ‘Cannot access this report because...

Enhancements to Microsoft Teams to foster further collaboration while working remotely
We’re in unprecedented times during this COVID-19 pandemic and it has forced many businesses to shift to a remote working...

Dynamics GP Correcting 1099 Tax Type
At some point throughout the year, you may discover that a vendor has been set up in GP with the...

Top 3 NetSuite 2020.1 New Module Features
For 20 years, twice a year, Oracle has been providing updates on NetSuite addressing everything from customer requests to updating...

Unknown Dictionary Error in Dynamics GP
One of the most common errors we receive on our help desk is the “Unknown Dictionary” error, usually occurring when...

9 Advantages Sage Intacct Offers Your Nonprofit Organization
Though it may not actually be written in your nonprofit’s mission statement, one of your organization’s primary goals is to...

Enabling Users to Work Remotely with NetSuite
NetSuite is a cloud-based ERP, users are enabled to work from home without sacrificing productivity, which is especially critical as...

Nonprofits can increase their resources with iMIS and Sage Intacct integration
For nonprofit organizations, such as associations and member-based groups, iMIS is a common tool. This association software solution helps them...

Social Listening with Microsoft Power Platform
Social Listening with Microsoft Power Platform Hi. I’m George Casey, and I’m talking to you from RSM’s Technology Experience Center...

Embracing Technology to Work Remotely with Microsoft Teams
Many companies are now discovering the flexibility of working remotely. For many of us, this has become part of our...

Sign Up for Increased Efficiency with Sage Intacct Contract Updates
Signing a contract often marks the satisfying start to a new working relationship, but successful contract management can prove to...

Custom Commission Field
Purpose: Calculate Commissions based on profit per line by using Custom Commission Fields. USE CASE: “Commissions are paid based on...

Using Microsoft AI Builder for Object Detection
Using Microsoft AI Builder for Object Detection Hi, I’m George Casey here at the RSM Technology Experience Center in Denver...

Reconciling Inventory Received Not Billed (IRNB)
For any company that has and receives inventory items in NetSuite, this account can be a little daunting to reconcile....

Leverage Dynamics Remote Assist with Field Service
Have you ever had a technician working out in the field that was not able to complete the work due...

Custom Center Tab and Executive Dashboard
Purpose: Create a custom Center Tab with customized links and a Center Tab Dashboard, using Saved Searches and SuiteAnalytics Workbook...

Building a Microsoft Virtual Agent for Customer Support
Building a Microsoft Virtual Agent for Customer Support Hi, I’m George Casey here at the Technology Experience Center in Denver,...

Creating a custom field that pulls results from a saved search in NetSuite
This is a NetSuite tip on adding a custom field that uses a saved search to pull the results from....

Microsoft Power BI Key Influencers for Housing Data
Microsoft Power BI Key Influencers for Housing Data Hi, I’m George Casey and I’m at the RSM Technology Experience Center...

Enrollment to RSAT 101
During my initial experience with the Regression Suite Automation Tool (RSAT) in training, I felt overwhelmed and confused. Coming from...
Saved Search on System Notes Fields
Purpose: Saved Search to show the latest edit to a record using System Notes fields Use Case: Vendor Edits to...

Facial Recognition Sign In with Microsoft Power Apps
Facial recognition sign in with Power Apps Hi, this George Casey and I’m here in the technology experience center. Today,...

Additional Color Coding in Dynamics 365 Field Service Schedule Board using Emoji’s
Have you ever needed additional color-coding functionality in Dynamics 365 for Field Service other than system status and priority color-coding?...

Dynamics 365 Customer Engagement User Security Role Report using XRMToolbox
In Dynamics 365 Customer Engagement (D365 CE) there is an out of box report called “User Summary”. This report can...

How to run NetSuite Role Comparison
Separation of duties in an ERP system is crucial to maintaining compliance. For example, a user should not be able...
NetSuite Update: 2020.1 release notes are here
As you may have noticed during your last login, NetSuite has announced their 2020.1 release dates. You can find the...

NetSuite New Release Facts 2020.1
The New Release Portlet Will Provide Important Resources: Release Preview Date When your Release Preview/Demo environment will be ready. This...

Create Late Time Entry View
A Project Service client recently came to me asking for help making sure their team recorded their Time Entries within...

Dynamics Project Service Order Set to Read Only
I recently encountered a simple issue while working in Microsoft Dynamics Project Service to automate the creation of Project Contracts,...

Dynamics 365 Project Service Time Entry Greyed Out
I was configuring Dynamics 365 for Project Service for a client and noticed an issue with time entry. Users could...

Dynamics 365 Project Service Rounding Time Entry Duration
A client recently asked if it was possible to round their user’s time entries to the nearest quarter hour. After...

Using Advanced Filters in NetSuite OpenAir
Purpose: Using advanced filters to refine list views to display the data you need. The steps below will aid users...

RSM on Bob Scott’s VAR Stars 2019
RSM has been selected as a member of the Bob Scott’s VAR Stars for 2019, a group of 100 organizations...
Asset Management for Dynamics 365 Supply Chain Management – Setup Areas for Assets
In our continuing series on Asset Management, we will now discuss more of the detailed functionality and setup of assets....

1099 Reporting with Sage Intacct
While everyone else is saying “Happy New Year,” you might be thinking “oh no, it’s the beginning of another tax...

Living the regression suite automation tool life
Written in cooperation with William Sumner. For the past couple of months, we have been working with Latha and the...

Satya Nadella NRF Keynote Video
As a Microsoft partner, RSM and Microsoft work closely together to showcase how Microsoft technologies can positively impact the growth...

Month-End and Year-End Processing in NetSuite
There are several important things to know when closing the books for month-end and year-end processing in NetSuite. These include:...

Asset management module introduced for supply chain management
The latest release of Microsoft Dynamics Supply Chain Management, available as of October 1, includes a new Asset Management module....
Understanding Private Channels in Microsoft Teams
What is a Private channel? Private channels in Microsoft Teams have long been a top requested feature in Teams user...

Sage Intacct Spend Management offers an efficient way to monitor your company’s expenses and budget
At times, it might seem as if your company’s spend management is like taking money out of a piggy bank...

Simplify your company’s budgeting and planning with new Sage Intacct capabilities
Budgeting and planning for your business can be a more complex process than you ever imagined. If you’re relying on...
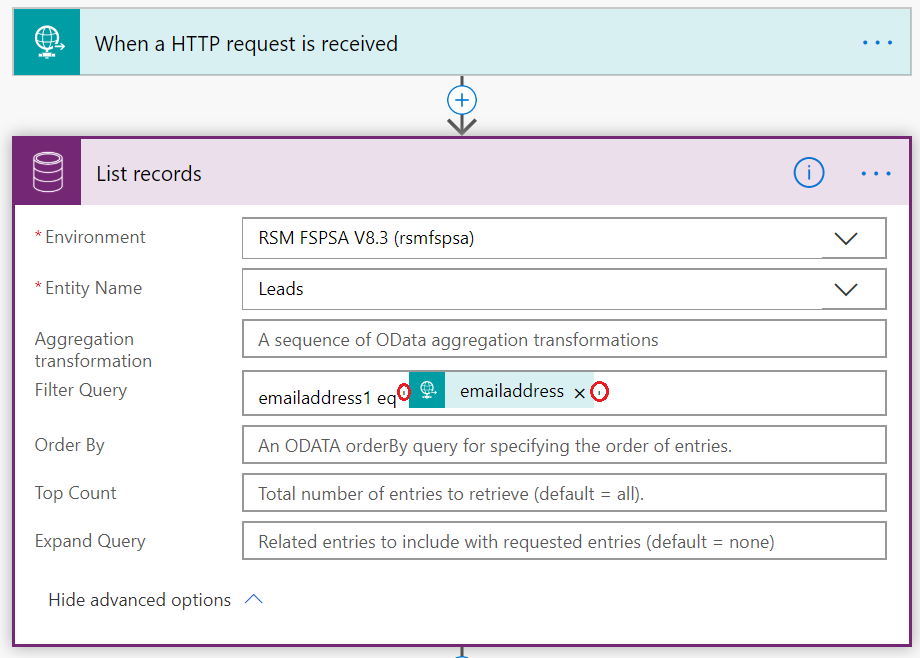
Power Virtual Agent & Power Automate
This week I was playing around with Power Virtual Agent and Power Automate. I needed to demo a virtual agent...
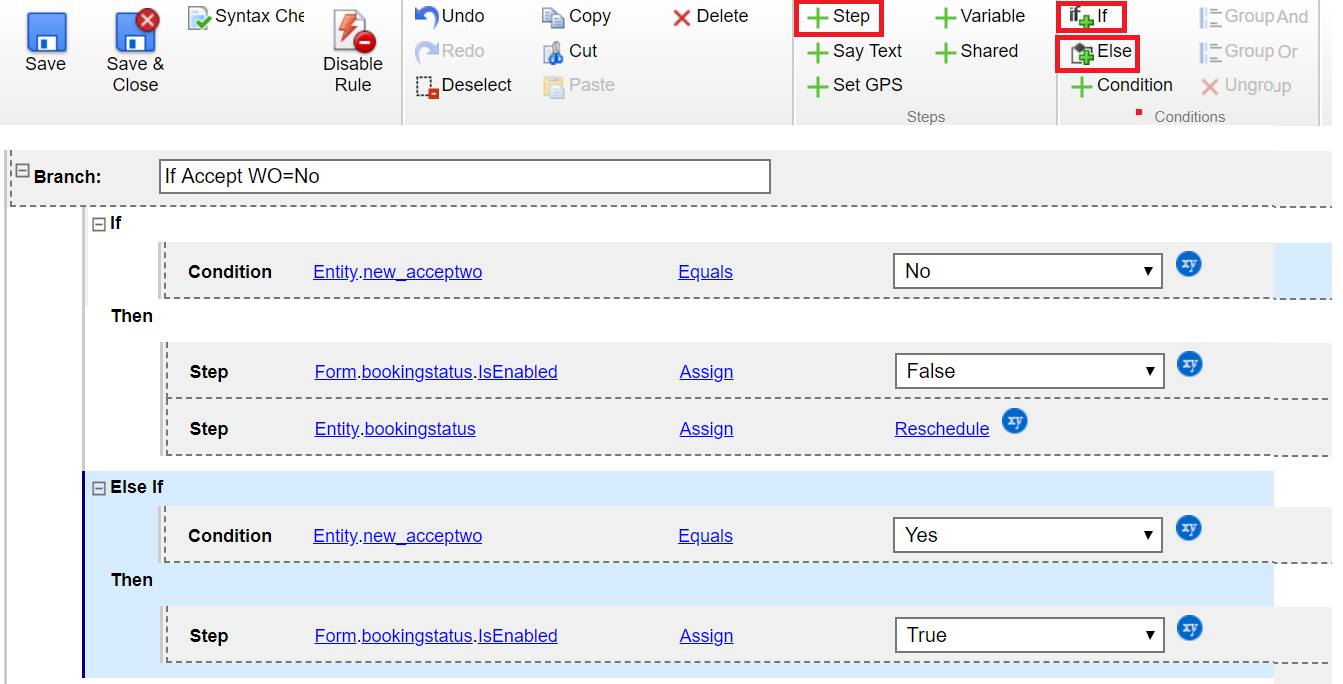
Dynamics 365 Field Service – Rejecting a booking
Field Service is a great tool for companies that send out remote workers, but what happens if that remote worker...
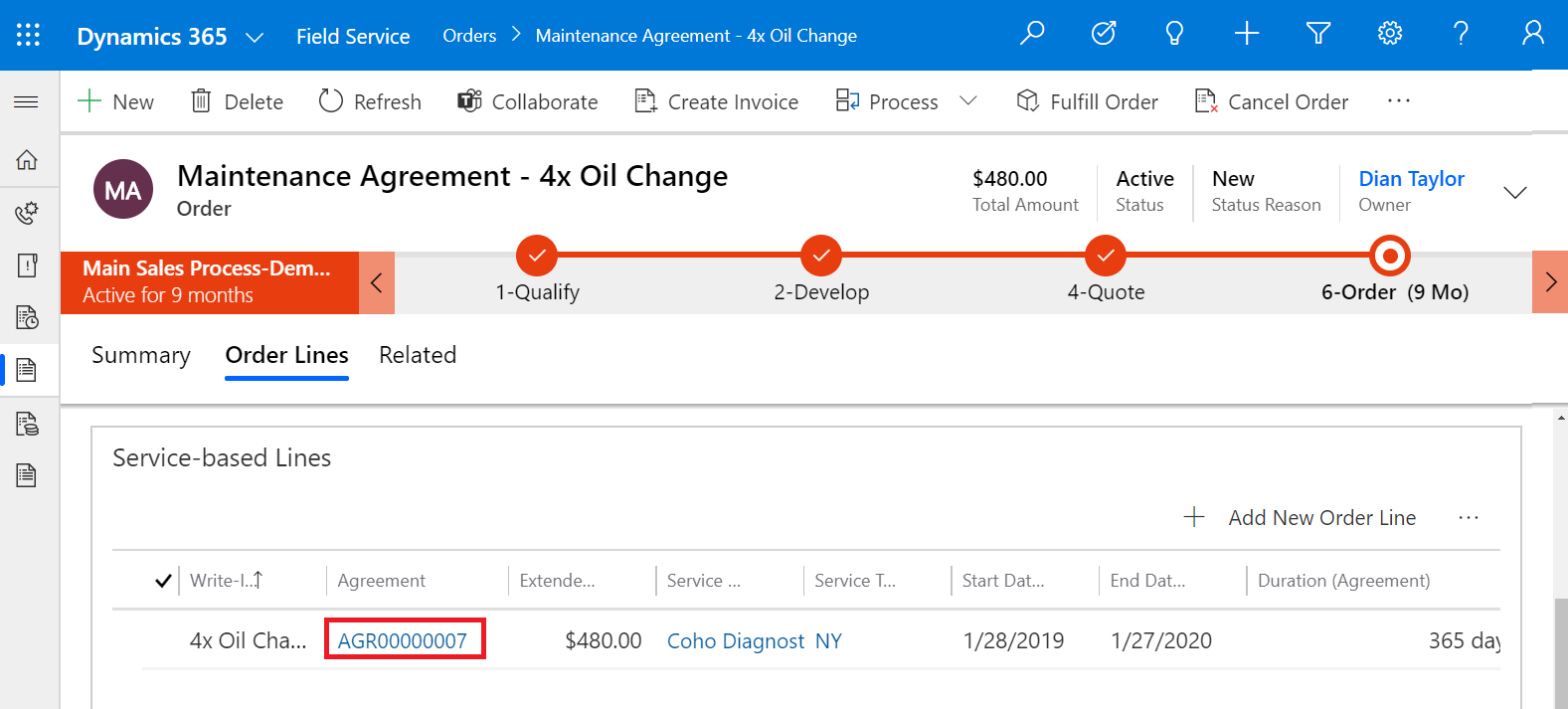
Dynamics Field Service, Project Service & Sales
If you have Field Service and/or Project Service installed in your Dynamics 365 instance you might be aware of the...
Adding Components to Unified Interface App(s)
Now that Microsoft put an expiration date on the legacy interface I thought it would be time to write a...
Customize Opportunity Close Dialog Box
After the October 2019 release wave, system administrators now have the ability to customize/configure the Opportunity Close Dialog box without...
Nested Grids in Dynamics 365
I came across this little gem when I was playing around with subgrids in Dynamics 365. We all know we...
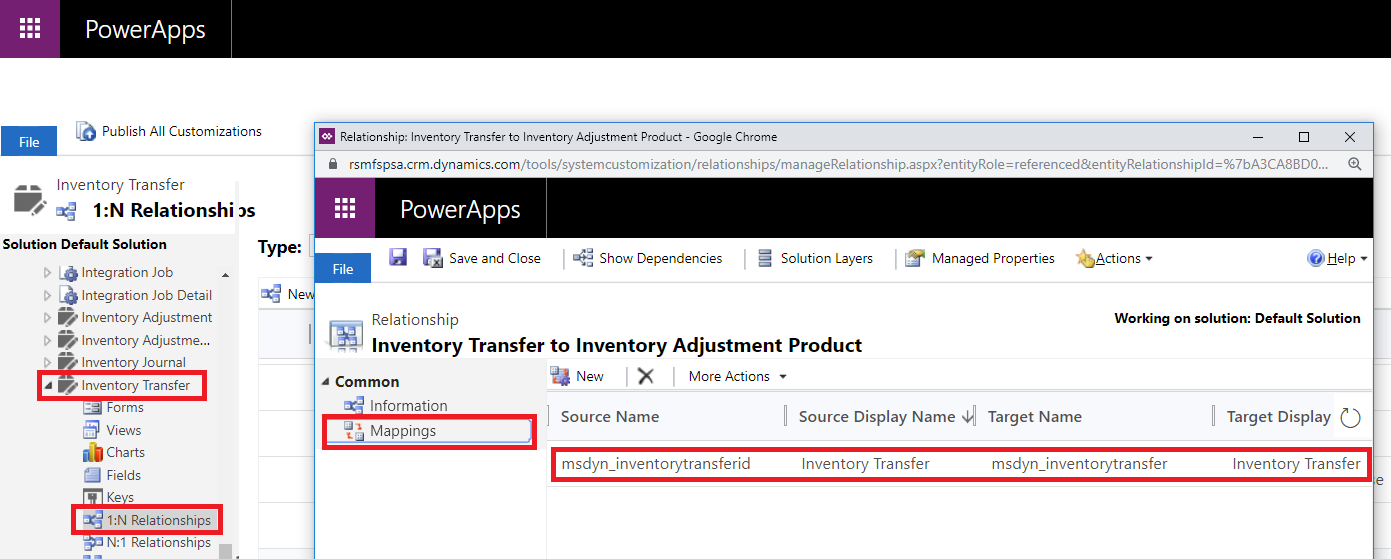
Inventory Transfers using the Inventory Dashboard
In this post I’m going to discuss how to use the previously created Inventory Dashboard to perform and inventory transfer,...
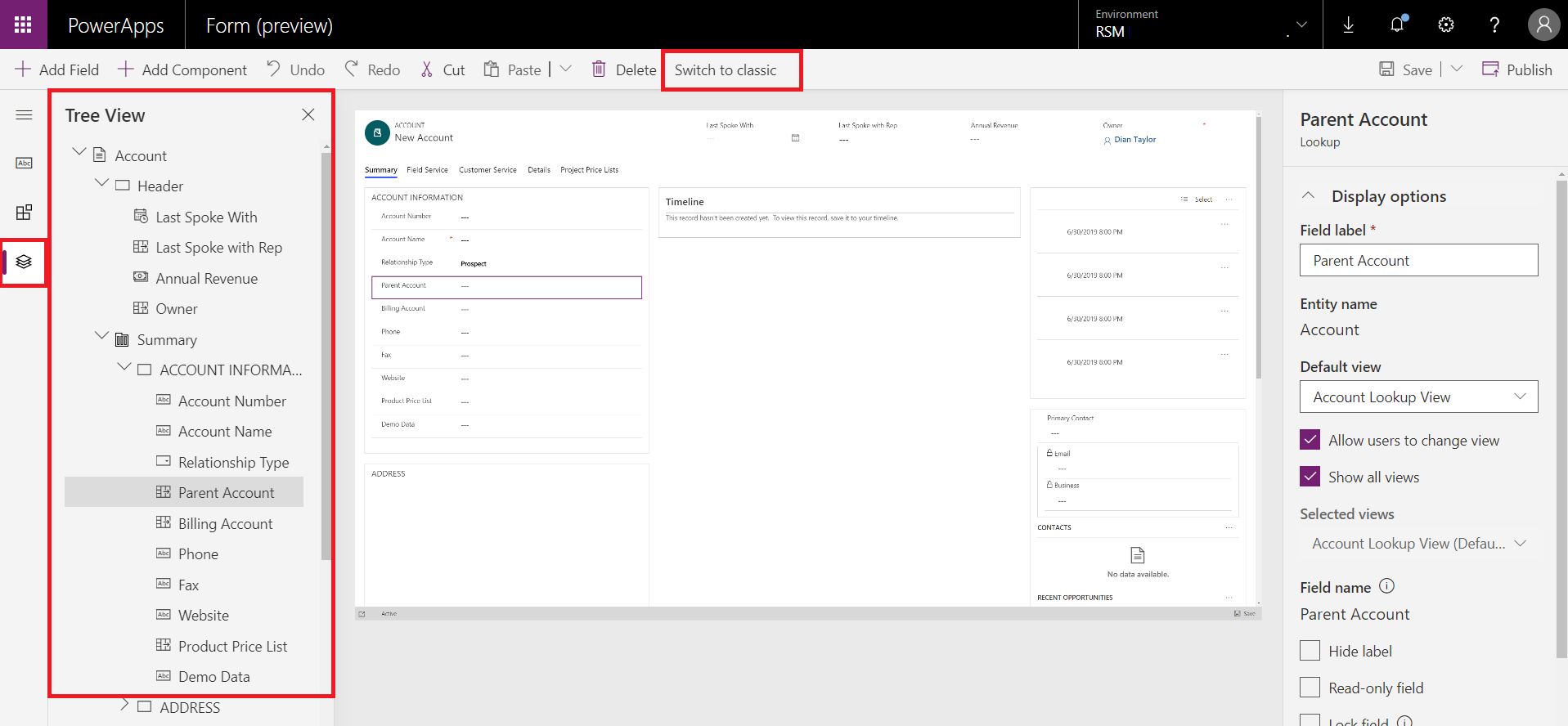
What I learned attending Dynamics 365 Saturday in Lawrenceburg, IN
Last August I attended the Dynamics 365 Saturday event in Lawrenceburg, IN. The event was packed with talented subject matter...

Streamline accounts payable with Sage Intacct automation options
With accounts payable automation from Sage Intacct and its Marketplace partners, your business can reduce invoice processing time and overall...

Switching to AP Automation? Here’s Everything You Need to Know
“What’s the status of that invoice?” asks your boss. “Umm…let me get that for you,” you respond as you begin...

Cash in on Sage Intacct’s enhanced bank feeds and reconciliation
How excited should you be about one of the newest features of Sage Intacct? Imagine a game show contestant winning...
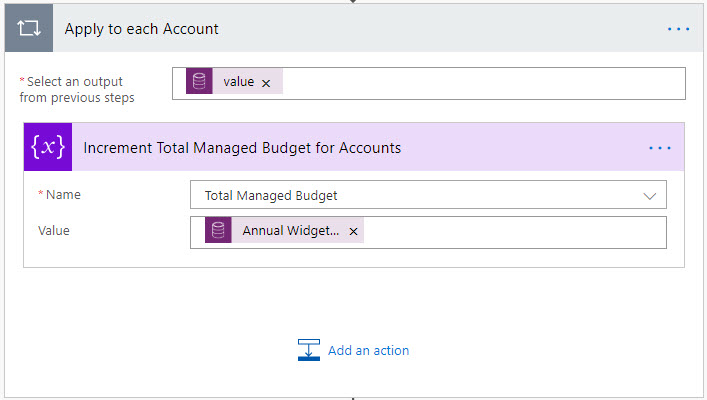
Dynamics 365 CE Multiple Entity Rollup Field with Power Automate
Out of the box rollup fields are very useful in Dynamics 365 Customer Engagement, but have limitations such as the...
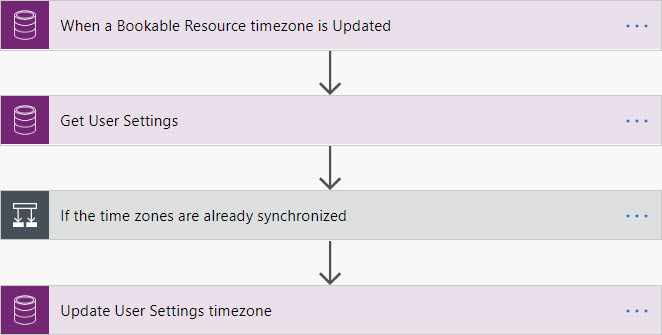
How to Prevent Infinite Loops in Power Automate Flows for Dynamics 365 CE
A common issue with using Power Automate Flows on Dynamics 365 CE records is inadvertently causing infinite loops. The workflows...
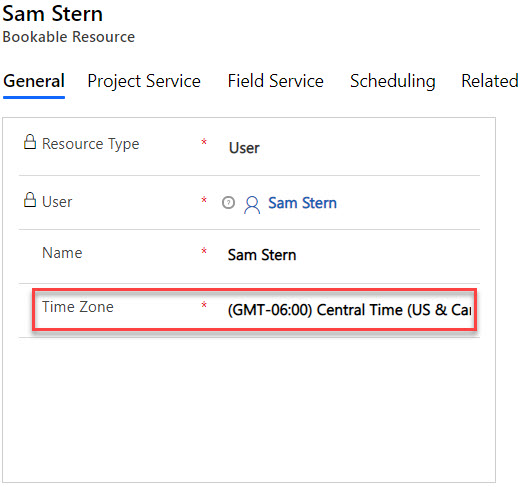
Dynamics 365 CE Synchronize User’s Bookable Resource Time Zone
The Bookable Resource record is scheduled according to the time zone selected on that record within Dynamics 365 CE. This works...

Video – Dynamics 365 Commerce and Connected Store
With the recent announcement of the new Microsoft Dynamics 365 Commerce and Connected Store solutions, we felt it would be...
Microsoft Dynamics 365 Commerce – Ste. Michelle Wine Estates story
Microsoft recently announced a new commerce platform, Microsoft Dynamics 365 Commerce. Built on Microsoft’s retail solution, this new commerce platform...

Add Custom Action to “Save &” Drop-Down on a Record
Purpose: Add a custom workflow button to the Save &… menu on a transaction. The steps below will aid in...

SuiteTax – NetSuite’s Next Generation Tax Engine
Guaranteed in Life: Death & Taxes Oracle NetSuite’s decision to build a next generation tax engine represents a wise investment...

Transitioning to Unified Interface
Using an existing environment to validate your legacy web client app with the Unified Interface This blog shows you how...
NetSuite Allocation Schedules
Leverage NetSuite allocation schedules to allocate expenses across departments, classes, locations, custom segments or subsidiaries. NetSuite provides flexible options for...
Approval Workflow – Rejection Reason
Purpose: Create a custom record to record rejection reasons as part of an approval workflow. Create a sublist on the...

Bet on a sure thing at Sage Intacct Advantage 2019 in Las Vegas
When you attend Sage Intacct Advantage 2019 in Las Vegas, you’ll be dealt a winning hand. No matter how long...

Show in which warehouse work order products are available on the Field Service Mobile App
Overview Field technicians probably want to know where the products they need (to complete a work order) are located so...

NetSuite News & Insights – September
Industry spotlight Trade associations RSM introduces NetSuite Association Management Solution for Trade Associations Utilizing the world’s leading cloud ERP for...

Microsoft D365 Finance and Operations New Hire Class of 2019
This summer, RSM is hosting its biggest Microsoft D365 Finance and Operations training class of almost 60 people. Over a...

Making Sense of How to Set Up Product Attributes in Dynamics 365 for Finance and Operations
Overview I do a great deal of training in Dynamics 365 for Finance and Operations and nothing seems to confuse...

Dynamics 365 Field Service Inventory Dashboard
Field technicians that have to go onsite and perform repairs and/or installations, have to keep track of what they have...

Top 10 Features of Sage Intacct’s Contract Management Module
Does your company have complex contracts with customers? Are you looking for deep financial and operational insights and a way...

Using Real Time Workflows as Security
Problem A while back I had a customer who wanted to prevent certain users to re-open a won opportunity in...

Auto Number Fields for Dynamics Customer Engagement
Dynamics 365 for Customer Engagement auto-creates unique ID’s for certain records types out of the box, for instance orders, cases,...

Top 3 NetSuite 2019.2 New Features
Twice a year NetSuite buries us in hundreds of pages of release notes detailing the new features soon to grace...

Floating Header Script Should be Used by All NetSuite Users
Are you ever viewing long transaction lists in NetSuite and wish you could freeze the panes like in excel? Well...

Introduction to Microsoft Dynamics 365 for Retail
With 89% of customers desiring a unified experience across channels, the pressures on retailers are growing. The need to engage...

Dynamics 365 – 2019 Release Wave 2 | Part 2
On August 2 the release wave 2 features for early access became available. I am super excited to discuss some...

NetSuite New Release Facts 2019.2
The New Release Portlet Will Provide Important Resources: Release Preview Date When your Release Preview/Demo environment will be ready. This...

NetSuite Update: 2019.2 release notes are here
As you may have noticed during your last login, NetSuite has announced their 2019.2 release dates. You can find the...

Email account isn’t configured with Dynamics 365 error
Problem Last week I had an issue with the Dynamics 365 for Outlook App. I had connected outlook to my...

Dynamics 365 – 2019 Release Wave 2 | Part 1
On August 2, 2019 the release wave 2 features for Dynamics 365 CE early access became available. I am super...

Know your Functional Currency before you setup that subsidiary in NetSuite
When establishing a new international subsidiary in a NetSuite, selection of currency can be confusing, as NetSuite does not use...

NEWSLETTER | NetSuite tips, ecommerce webcast, and important security updates.
Award RSM ranks #1 with Accounting Today’s 2019 value added reseller 100 RSM, the top firm on Accounting Today’s VAR...
Dynamics 365 Customer Service: Setup Mailbox for Automatic Case Creation
Overview In this article I am going to explain how we can setup a mailbox in exchange and tie that...

Dynamics 365 Customer Service – Automatic Case Assignment
In this article I am going to explain how we can use workflows to assign cases to a team in...

SuiteSolution- Vendor Prepayment
Overview: Have you ever run into a situation where you have to pay a vendor prior to receiving the goods...

Impact of Account-Specific Domains in NetSuite
In the first half of 2019, NetSuite will be rolling out account specific domains. This feature will be activated on...

The Benefit of eLearning
“The only thing worse than training your employees and having them leave is not training them and having them...

Microsoft Dynamics 365 CRM | Who “owns” the Business Applications within the Organization?
Overview Every organization has this discussion at some point in their journey and has to determine its own answer to...

Dynamics 365 App for Outlook shows Dashboard vs Contact/Lead Pane
Problem One of my coworkers reached out to me last week to see if I knew why a dashboard was...

Financial Period Close Configuration – Get the Most Out of Your Financial Period Close Workspaces!
Overview Utilizing the Financial Period Close workspace in Dynamics 365 Finance and Operations requires that you first configure the financial...

The Power of Project Stages
Anybody who has worked with project management and accounting in Dynamics 365 and has set up a project, knows that...

Filtering Dynamics 365 CE Fields in Flow
Overview: Microsoft Flow adds a lot of new functionality for Dynamics 365 CE beyond the capacity of workflows. One exciting...

May NetSuite News & Insights
Case Study RSM rapidly implements NetSuite for Apellis, a growing life sciences company When going public, Apellis needed to transition...

PowerApps – Saving Digital Signatures to OneDrive
Capturing digital signatures in a Microsoft PowerApp may be a key piece to your clients business, but how do you...

12 Key Components of the PowerApps Visual Designer (D365 CE Example)
Microsoft PowerApps is a product created to help you build your own applications with little code or need for software...

Keys to Managing a NetSuite ERP project
In my 15 years of leading ERP projects, my common theme for successful project outcomes is to focus on the...

Dynamics 365 and Common Data Services licensing changes
From your monthly phone bill and Netflix subscription to your car insurance and monthly rent, the amount you pay for...

Finding Missing Accounts in Management Reporter
Overview A common complaint at month end is that it’s hard to find what accounts are missing in Management Reporter. ...

Utilize Dynamics 365 for Mobile
If you want to be able to utilize Dynamics 365 for mobile as you might already you, you’ll need to...
How to address the new ASC 842 lease accounting standard in NetSuite
The new ASC 842 standard presents a wide range of implications that will require most operating leases to be reflected...

Microsoft Dynamics GP – SmartList Displays SOP Returns as Negative Numbers
Recently I have had a few inquiries about how SmartList displays and exports SOP return documents. Have you ever noticed...

NetSuite’s hidden SQL formula
Do you know about the NetSuite formula ‘ns_concat()’? This formula is used to display the output as a single comma...

Stop, Collaborate, and Listen with Microsoft Teams
Microsoft Teams brings together communication threads, chat, video meetings, file storage, and application integration. Like many Microsoft products, it is...

RSM recognized as innovation award finalist by United Fresh
RSM’s CLEARthru was recently announced as a finalist in the Best New Food Safety Solution category for United Fresh Produce...

Microsoft Dynamics GP: The Disk is Full Error
You have just logged in to Dynamics GP, and attempt to open one of the menu options and receive an...

Which reporting tool do I use in Microsoft Dynamics GP? (Continued)
Report Writer and SmartList In my last post I provided some basic conditions to consider in determining which reporting tool...

Dynamics 365 webcast series: Leveraging applications in Microsoft Dynamics 365
Having trouble managing multiple users and teams in Microsoft Dynamics 365? Do your users feel like there are too many...
Using Search in the Microsoft Cloud
Moving your enterprise content to the cloud allows you to capitalize on an underused (or underappreciated) tool of Office 365:...

Tips on how to use SmartSheet to manage a NetSuite ERP project
The main Project Management tool I recommend is a cloud-based tool like SmartSheet to develop and collaborate on the typical...

Why Chief Operating Officers are turning to Microsoft Dynamics 365 for Finance and Operations
In this video, you’ll see how Microsoft’s Dynamics 365 for Finance and Operations can play a critical role in the...

Dynamics 365: Enhanced Service Level Agreements, a quick setup guide
Overview Service Level Agreements (SLAs) are typically used on Cases to track different things whether it’s a Customer Service response...

Integration Manager and Default Distribution Accounts
Overview Users new to Integration Manager (or just rusty) often contact the RSM Dynamics GP National Help Desk with questions...
Trouble Getting SafePay to Read the Account Number in Dynamics GP
Have you ever had issues with Dynamics GP’s Safepay reading your bank account number? One of the most common issues...

Improving the customer experience on the Help Desk Performance Management: Part I – Service Level Agreements
Measuring the performance of your firm’s help desk is an integral part of understanding your client’s needs. In fact, in...

Microsoft Dynamics 365 April release
The April 2019 upgrade for Microsoft Dynamics 365 (D365) has a multitude of new and improved features. One of the...

Dynamics GP – 7 Things You Should Know About the Reports Dictionary
After many years of consulting and supporting Microsoft Dynamics GP, many customers still rely heavily on their Dynamics GP modified...

GeoCoding records in Woodford for the Field Service Mobile app (Built on Resco)
There is a powerful tool in Woodford called GeoCoder. This is an easy way to easily populate the Latitude and...

Mapping your warehouse and product inventory data for the Field Service Mobile App.
Overview The Field Service Mobile and Resco CRM Mobile apps are very powerful and have a lot of great functionality...

Management Reporter: Reports are not updating with the correct amounts, or at all
You are running your financial reports in Management Reporter Report Designer but the reports are not updating with the amounts...

Management Reporter: Report Queue stuck in Dynamics 365
Your customer calls you and lets you know that they are running reports for month end in Management Reporter Report...

Benefits of Customer Service Form for Non-Retail Dynamics 365 for Finance and Operations Users
Overview I’m often asked about the easiest way to find information about customers in Microsoft Dynamics 365 for Finance and...

Rework Batch Orders in Microsoft Dynamics 365 for Finance and Operations
This article will discuss reworking a batch order in Microsoft Dynamics 365 for Finance and Operations. Before we get started,...

Best practices for adding custom fields in NetSuite
NetSuite is uniquely capable of molding to meet the needs of your operation. Custom fields are at the heart of...

Oracle NetSuite SuiteWorld 2019 Recap
Our team had a great week at SuiteWorld 2019. We attended great sessions, listened to some exciting keynote speakers, connected...

Pre-cut melons still on the shelves or in your fridge, but how do you know if it was part of a recall?
Overview: This time it’s a Salmonella outbreak linked to 93 people so far.1 Caito Foods recently recalled pre-cut watermelon, honeydew...

Reprinting Checks from NetSuite
Overview: Below is a list of steps that you can take when you need to reprint checks out of NetSuite....

Understanding Workspaces in Microsoft Dynamics 365 for Finance and Operations
There are several navigation options you can use in Dynamics 365 for Finance and Operations to arrive at the same...

Microsoft Flow: Copy Email Attachment to OneDrive for Business and Approve Copy to SharePoint
Overview Microsoft Flow enables the ability to automate tasks across a multitude of business software’s. This is possible using connectors...

Microsoft Dynamics GP: How to Eliminate Multiple W2 Forms When There Are More Than Two Local Taxes Withheld
Now that W2 season is in the rearview mirror, it is a good time to reflect on the challenges we...

SmartConnect Error Fixes for Dynamics GP 2018
Overview: Recently, while importing data into Dynamics GP 2018, using SmartConnect, I ran across some error messages. My first instinct...

ASC 842 / IFRS 16 – NetSuite support for new Lease Accounting Standards
ASC 606 requires companies to overhaul their system processes for revenue recognition and perform complex analysis to recast revenue according...

Sage Intacct Improves Wholesale Distribution Productivity With New Features
Great news for wholesale distribution companies—Sage Intacct recently released new exciting features in their Inventory Control module to improve your...

Foreign Currency Expense Reports
Perhaps the biggest new feature with 2019.1 is the ability to reimburse employees in currencies other than the base currency...

NetSuite News & Insights – March Edition
Would you like to receive our NetSuite News & Insights in your inbox each month? Each month, RSM provides the...

Comparing Allocation Options in Sage Intacct
It’s no secret—allocations are time-consuming, error-prone, and yet, incredibly important for understanding financial performance. It’s vital for both businesses and...
Ready for the Close-Up: Making the Most of Software Screenshots
Whether it’s for technical support help, user documentation and training, or our own reference, we all take software screenshots occasionally....

Playing Well with Others: Budget Plans and Financial Report Designer in D365FO
Microsoft Dynamics 365 for Finance and Operations (D365FO) has a powerful Budget Planning feature set that allows organizations to build...

Batch Attribute Pricing in Microsoft Dynamics 365 for Finance and Operations
Have you ever gone to a specific grocery store to buy fruit and vegetables because you knew their quality was...

Dynamics GP Field Service work order won’t close due to “You may not complete due to a back order or in transit document” message
While working in the Dynamics GP Service Call Management module, the user received the error message, “You may not complete...

Creating direct ship delivery (DSD) POs in D365
Overview There are times when a retailer may need to create direct ship delivery (DSD) purchase orders in mass, such...

5 Tips on How to Succeed with Your ERP Implementation
Implementing a sophisticated ERP system for the first time is a lot of work. It can also be complex for...

Using Retail Allocations in D365
Overview Allocations and pre-allocations are common business processes in the retail industry for moving product currently in the distribution center...

Refunding an Open Balance (Customer Deposit)
Refunding an open balance gives money back to a customer who has overpaid or is due a refund. For example,...

Finance Teams: Here’s How to Put ASC 606 on Autopilot
In 2014, the Financial Accounting Standards Board and the International Accounting Standards Board issued two new standards — ASC 606...

NetSuite webcast: Managing growth and acquisitions with NetSuite OneWorld
Today’s organizations are increasingly operating on a global stage. The pursuit of growth opportunities, both organic and inorganic, has forced...

Duplicate SQL job “Remove Posted PJOURNALs” and the havoc it can unleash
Dynamics GP has a very important SQL job that cleans up records in a table called PJOURNAL. Without this job,...

Dynamics 365 – Where did my apps go?
One of the best features that Microsoft has released in the last couple of years is the ability to make...

Meet RSM at SuiteWorld
RSM is proud to be a Gold sponsor of Oracle NetSuite SuiteWorld, April 1-4, 2019, at The Sands Expo and...

NetSuite News & Insights – February Edition
Would you like to receive our NetSuite News & Insights in your inbox each month? Each month, RSM provides the...

Microsoft D365 for Finance and Operations in Retail
When you start a retail business there are many challenges and it involves many, many decisions; where/how will you sell,...

PowerPoint and Prezi: Presentation Delivery with Unique Styles
Overview Throughout most of my career and in college, most of the presentations I’ve designed, or used to present to...

Handling Trade Allowances in Dynamics 365 for Finance and Operations
Overview In a previous article, we discussed what a Trade Allowance was in Dynamics 365 for Finance and Operations (D365) and...

Dynamics 365 for Retail and the Omnichannel Experience
Overview Retail is an industry that is constantly changing, and retailers must also understand trends in order to keep their...

Part 3: Three compelling reasons to consider Microsoft Dynamics 365 Business Central
If your current ERP is several versions behind and you don’t want to go through the painstaking processes of upgrading...

Sage Intacct has released the new Sage Intacct Budgeting and Planning Tool for SMBs
There is nothing more important to the health of a growing business than the ability to look into the future...

NetSuite has announced their 2019.1 release dates – Here’s what you need to know
As you may have noticed during your last login, NetSuite has announced their 2019.1 release dates. You can find the...

Retail Catalog Approval Process with Workflow
Overview The retail catalogs in Microsoft Dynamics 365 for Finance and Operations (and Dynamics 365 for Retail) allows you to...

Standard Costing Setup in NetSuite
Standard costing helps identify cost-saving opportunities in manufacturing and procurement by allowing users to track cost variances by category. Required...

How Nonprofits Can Stand Out in Today’s Competitive Funding Environment
Today’s funding environment is competitive, and many not for profits are struggling to identify, pursue, and navigate the path to...

Solving an Excruciatingly Long GL Import
Steve Endow, owner of Precipio Services, has done a fair amount of volume testing of imports to Dynamics GP and...

Advanced Approvals SuiteSolutions
The Advanced Approvals SuiteSolutions is a great module to utilize if you are looking to address common approval requirements across...

NetSuite Supply Chain Control Tower; End-to-End Supply Chain Visibility
Supply Chain Management or SCM is defined as a wide range of activities required to plan and control production, inventory,...

GL Impact / Tax Impact of Using Class, Department, Location Segments on the Line or the Header of the Transaction?
Use Segments in the Header, or use them on the Transaction Line? How does this affect the GL Posting? Not...

Secure Your SuiteCommerce Site Without Sabotaging it: 7 Essential SEO Tasks during an SSL Migration
The day has arrived: You have reviewed the SSL upgrade process, the new SSL certificate is ready, your SuiteCommerce development...
Introducing Sage Intacct’s Revenue Recognition for Nonprofits
Nonprofit revenue recognition standards are constantly changing, and Sage Intacct has released a new feature to help not-for-profit organizations like...
Using Workflows to Set Item Sublist Fields
NetSuite recently added the ability to set sublist values via workflow, for the Items sublist. Prior to this new feature,...

Part 2: Three compelling reasons to consider Microsoft Dynamics 365 Business Central
Many companies quickly grow out of their business systems. They often have siloed systems, duplicate data, manual processes, insufficient reporting...

How Multi-Entity Businesses Can Grow Faster With Streamlined Consolidation
If you’re running a multi-location or multi-entity business, you face unique accounting challenges like decentralized payables and inter-entity transactions. With...

Tips for Effective Virtual Software Demonstrations
Have you been given the task of presenting your company website or specific software to a client or vendor? Is...

The Basics of Trade Allowances in Dynamics 365
FOR DYNAMICS 365 FOR FINANCE AND OPERATIONS Overview: The managing of trade allowances in Dynamics 365 for Finance and Operations...

Create Record Workflow Action in NetSuite
Create Record Workflow Action Purpose: Automatically create a project record upon saving a Quote/Sales Order and link records together. Add...

Fraud Detection for Checks – NetSuite and Positive Pay
What is Positive Pay? Positive Pay is an automated fraud detection tool that matches the account number, check number and...

Part 1: Three Compelling Reasons to Consider Microsoft Dynamics 365 Business Central
Are you looking for a new Enterprise Resource Planning (ERP) Software or have an older version of Microsoft Dynamics NAV?...
NetSuite Landed Cost – Mill Taxes
Purpose To record Mill tax as a part of the inventory cost, rather than an expense. Facilitate matching monthly cost...

Configuring User Options in Dynamics 365 for Finance and Operations
Overview: Out of the box, Microsoft Dynamics 365 for Finance and Operations has a number of personal option features that...

Are Incorrect Inventory Quantities and Values Plaguing your NetSuite System?
Do legacy inventory problems plague your system? Would you like to correct the inventory quantity and valuations mismatches? Overtime as you...

Personalizing your Dashboard Tiles in Microsoft Dynamics 365
Overview: Out of the box, Microsoft Dynamics 365 provides a comprehensive visual arrangement to help you navigate and find data...

It’s All About You: Audience Considerations for eLearning
Creating a great self-paced training experience depends significantly on identifying and understanding the audience that you are expecting to take...

Creating a work order from an opportunity in Dynamics 365 for Customer Engagement (yes, with opportunity products!!!!)
Users were always able to convert an opportunity to one or multiple work orders, but if the opportunity had opportunity...

Route Scrap for Manufacturing in Microsoft Dynamics 365 for Finance and Operations
One of the more complex screens in the Production Control module in Microsoft Dynamics 365 for Finance and Operations is...
Organization Change Management in a NetSuite ERP project
As the project sponsor or project manager of a mid-sized company, you start your project feeling confident that everything is...

How Multilingual Training Can Influence a Culturally Diverse Audience
Although challenging to provide training to a multilingual audience, it is vital to do so in an increasingly global community....

Exposing data entities in Dynamics 365
This article will explore one method of exposing data entities (OData) to the public for communication with external software applications....
Electronic Bank Payments & Advanced Electronic Bank Payments
Electronic Bank Payments SuiteApp (EBP) enables you to process bank payments of vendor bills, employee expenses, partner and employee commissions,...
NetSuite’s New Reporting Feature – Workbooks
If you’ve been hanging around SuiteWorld, the annual NetSuite user conference, within the last five years then you’ve heard about...

What’s new for Dynamics 365 for Field Service – October ’18
Microsoft’s release notes give a lot of information on the new features of the new Field Service release, but it...
Creating a Consolidated Balance sheet displayed by Accounting Period in NetSuite
When using a NetSuite Instance with multiple subsidiaries, clients will want to see a consolidated balance sheet of all the...

Hidden Heroes in SuiteAnalytics Workbook
Delivering long-awaited reporting enhancements like multi-level joins, a user-friendly drag and drop interface and a host of options for data...

Enhancing Month End Close in NetSuite
Month end closing tasks are a fundamental component for any business and a gap in NetSuite. Currently, the functionality that...

Views for Quick SSRS Report Development
Microsoft Dynamics 365 for Finance and Operations, as well as the two former Dynamics AX products (AX 2012 and AX...

Publishing SmartList Reports to Excel in Dynamics GP
Did you know that you have the ability to publish reports to Excel? SmartList reporting has been around since the...

Hands-on Learning: Practicing Software Skills During Training
Over the past two years, I have worked to design and develop training courses for Microsoft Dynamics 365 for Finance...

The Production Cycle in Microsoft Dynamics 365 for Finance and Operations
In this article, we are going to look at the Production cycle in Microsoft Dynamics 365 for Finance and Operations....

Upgrading Your Development Skills for Dynamics 365
Microsoft Dynamics 365 for Finance and Operations development is very different from what developers are using for Microsoft Dynamics AX...

Migrating Dynamics 365 Portal Records
Configuring a Dynamics 365 portal can be a challenging task and due to this complexity, you generally would not want...

eLearning versus Face-to-Face Learning: Advantages
eLearning is increasingly becoming a staple in training employees. As a result, where does the tried-and-true method of face-to-face learning...

Keeping in Touch: Contacting Coworkers Using the Dynamics 365 Unified Operations Mobile App Workspaces
In a business world where travel is often the expectation or the norm, it is important for employees to understand...

NetSuite webcast (9/11): Delivering Omni-channel retail experience with SuiteCommerce Advanced
Start the journey into the digital transformation of your online business with NetSuite and the SuiteCommerce Advanced platform. SuiteCommerce Advanced...
NetSuite Integrations using two factor authentication
NetSuite moving to 2 factor authentication, or “TBA” As you may or may not have heard, NetSuite is changing the...

NetSuite Release 2018.2 Coming soon – Important Information!
As you may have noticed during your last login, NetSuite has announced their 2018.2 release dates. We’ve summarized some of the...

NetSuite Custom Addresses
It goes without saying that Customer and Vendor Addresses are a key information component in conducting business. In NetSuite, address...

Known Issue with Collections Management and Customer Combiner
Have you had trouble using the Customer Combiner in the Professions Service Tools (PSTL) after implementing Collections Management? You may...

Get Patching! CVE-2018-0886 CredSSP Flaw in RDP Affects All Versions of Windows
Microsoft released an update in March which may or may not impact your ability to use Remote Desktop Protocol (RDP)...

NetSuite Out of Office Approval Solution
Approval routing is an important component of NetSuite and is widely used by customers. One of the challenges of these...

NetSuite Subsidiary Split – Possible Solutions
I recently had an experience with a company who, already live on NetSuite, approached our team for guidance after a...

Which reporting tool do I use in Microsoft Dynamics GP?
Have you ever needed to print a report or extract data out of Dynamics GP and wondered which reporting tool...

NetSuite – Importing Bank Details when using Electronic Payments
*(Bundle 211453, US version, free) After you have installed NetSuite‘s Electronic Payments bundle and set up your bank(s) template information,...
Becoming a NetSuite Consultant
Starting a new job is often daunting enough, but adding the task of having to learn a new Enterprise Resource...

Do You Know the Differences Between M and DAX in Power BI?
Both M and DAX are expression languages for Power BI. Both have more similarity to Microsoft Excel expressions than similarity...

Top Three Reasons to Use Microsoft Azure Environments
Setting up virtual training environments is an important aspect of any functional or technical training class for Dynamics 365 for...

Intern Observations: Dynamics 365 for Finance and Operations
A major benefit of an internship at RSM is the opportunity to learn Dynamics 365 for Finance and Operations from...

Visual Studio Tips for Developing for Dynamics 365 for Finance and Operations
The IDE environment has completely changed for AX 2009 and 2012 environments. MorphX is no longer what you will use...

Using Transaction Descriptions in Microsoft Dynamics GP: Reconcile Payables to GL
There are a few key concepts to understand how Transaction Descriptions and Reference fields work in Dynamics GP to make...

Transitioning from Java to X++ – Part Two
In the first article of this series, I covered the differences in operators between Java and X++. As a Java...

Seeking Side-by-Side Drag and Drop for Dynamics Development in Visual Studio
In Microsoft Dynamics AX 2012, developers were able to open a second copy of the Application Object Tree (AOT), or...

“Unhandled script exception” Error When Running the Historical Stock Status Report
We have gotten reports of GP users receiving the error shown in the screenshot below when generating the Inventory’s Historical...

Warehouse Management – What you Need to Consider and Know Before Implementing
As more and more companies beginning to upgrade to Microsoft Dynamics 365 for Finance and Operations, a rather sizable decision...

Retail Price Simulator for Dynamics 365
The Retail Price Simulator in Dynamics 365 offers users the ability to test out pricing on items that may have...

Screen Time vs Face Time: Selecting the Right Training Delivery Type
Training is an important element of professional career growth, and the successful delivery of training relies on careful consideration. Several...

Juggling multiple programs in one Dynamics 365 environment
As IT professionals, we love to solve complex problems with the tools that we have been given. You might have...

NetSuite webcast (6/6): Leveraging NetSuite for ASC 606 adoption
The effective date of Accounting Standards Codification (ASC) 606 is coming soon, bringing a new revenue recognition standard to both...
Reporting (and Searching) in a NetSuite Multi-Book Environment
In the past couple years, NetSuite’s Multi-Book Accounting (MB) feature has become increasingly popular. Many users are implementing it for...

NetSuite Multi-Book: Searching on Amortization and Rev Rec Schedules
For general information and tips on Multi-Book reporting and searching, see my previous post here. As you may or may...

NetSuite SuiteWorld18 Recap
After the first full year of integration with Oracle, NetSuite’s SuiteWorld conference gives us a good indication of how the...

IT Professionals – Are you ready for ASC 606?
Coming out of SuiteWorld last week, we were a bit surprised at the number of companies who still have not...
Applications Templates without Programming for Microsoft Power BI
One of the newest ways to extract data from Microsoft Dynamics 365 for Finance and Operation, Enterprise edition is to...

Boosting User Adoption with Learning Paths
You have recently helped to implement a new Dynamics 365 environment for an organization. Your team is looking for ways...

How to Setup Microsoft Dynamics 365 App for Microsoft Outlook
Do you or your employees want to be able to track your CRM contacts in Outlook? How about having your...

Assigning SSRS Reports to GP Windows for Self Service Users
I recently worked with a client that is using Requisition Management in GP2016. They wanted their requestors to be able...

GP Web Services and TLS 1.0
Recently, we’ve noticed that some users have encountered a few issues after they ran Windows Updates on their GP/SQL Server,...

How to leverage Organization Insights for your system
Have you ever wanted to track user adoption or system performance in a more streamlined way? The answer is Organization...

Fixing stuck batches in Dynamics GP
Locked records and stuck batches in Dynamics GP can happen for a variety of reasons including temporary loss of network...

Tips & Tricks for executing the best training videos
Here are some of the best practices we’ve found for recording training videos: Keep the videos short in length. No one...

Dynamics GP Project Accounting error: The Employee ID cannot be assigned as a Project Manager
You have an existing Project and would like to change the Project Manager. In the Project Maintenance window, you attempt...

Add more detail to your schedule board within Dynamics 365 for Field Service
Many dispatchers at organizations we have implemented Field Service or have asked this same question: “Can you add more information...

How to Update Work Flow Status in Dynamics GP
Have you ever accidentally submitted a GL Batch for approval while setting up WorkFlow? To correct the issue, you’ll need...

Dynamics 365: Create an App in 5 simple steps!
Dynamics 365 has an awesome tool called “Apps”, which is a great way to simplify the user experience based on...

How to Handle State by State Tax Treatment Differentials When Setting Up Payroll Codes in Dynamics GP
In an earlier post, we were warned of the dangers of having payroll codes with tax treatments that do not...

Retail Coupon Management in Dynamics 365
Dynamics 365 for Retail (and Finance and Operations) recently came out with the new coupon functionality that retailers have been...

Transitioning from Java to X++ – Part 1
A programmer coming from Java background into X++ programming owned by Microsoft will see a lot of similarities in terms...

Dynamics 365 Cycle counting plans and the mobile device – setup options
In Dynamics 365 for Finance and Operations, there are additional options for you to automatically create a Cycle counting plan...

Navigating through NetSuite Faster (Part 2): Keyboard Shortcuts
In part 1, Navigating NetSuite Faster: Global Searches, we covered tips and tricks that will allow users to quickly find records...

Navigating through NetSuite Faster (Part 3): The Navigation Portlet
The Navigation Portlet allows you to simplify your navigation to frequently used records in NetSuite. Using the portlet, you can...

Using User-Defined fields in Purchase Requisition Approval Workflow
When implementing requisition approval workflow, you can make several adjustments beyond the standard entry fields. Now, you can set your...

SQL View – Inventory Transactions with Lots and Reason Codes
Standard Dynamics GP Inventory Transaction reports and SmartLists do not include Lots or Reason Codes, but there are times that...

Master planning for retail mass merchandisers – Part 2
In part 1 of this article, we discussed configuration, setup and some basic performance considerations. In this portion, we will...

Printing Miscellaneous Checks using Mekorma
Printing Miscellaneous Checks with Mekorma MICR needs to be done correctly in order for the transaction to be be completed...

Master planning for retail mass merchandisers – Part 1
Retail mass merchandisers typically have very large item catalogs (100,000+ items) and most items are replenished automatically via master planning....

8 things to do at SuiteWorld 18 to maximize your experience
With SuiteWorld just days away and many having not previously attended, this top eight list will give you an idea...

When Should GP Users Consider Advanced Bank Reconciliation?
While GP’s Bank Reconciliation tool works fine for many situations, once banking gets a little more complicated, it may be...

Multicurrency Tips and Tricks: Rolling Retained Earnings in Management Reporter
Rolling retained earnings in management reports is one of the more problematic areas in multicurrency. In order for retained earnings...

Dynamics 365 editable grids functionality limitations
Editable grids is an out of box functionality introduced last year for Dynamics 365 CRM. This functionality has been discussed...

SmartList Tip: Unable to change display name field created from SmartList Designer
If you are struggling to change a display name field created from SmartList Designer, there are a few steps you...

Microsoft Dynamics CRM Online/Dynamics 365 Customer Engagement Online FetchXML Filter “In” Parameter
Issue Explanation When writing FetchXML to use as a data source for a custom report, a nice place to get...

Utilizing User Classes to Organize SmartList Favorites
Are you an organization with lots of companies/databases and an endless list of SmartList favorites? Would you like to group...

Dynamics GP – Payroll deductions missing for employee that is NOT subject to FICA
A company has added a health insurance deduction, dental deduction and a group life benefit. These are standard deductions and benefit codes we use for all employees. When they process payroll, the health deduction isn’t there and the dental deduction is the same as the group life benefit instead of what is setup in the card. The deductions show up correctly on the build check file report. There is an employee that is exempt from FICA tax, everything else is the same as other employees. Below is a huge list of why deductions may not be...

Microsoft Flow Functionality and Use Cases
Microsoft Flow is a new workflow engine that was released in 2017. Flow has many connectors to many different applications...

Upgrade to V9.0 (Fall 2017 Release) today!
The Dynamics 365 V9.0 (Fall 2017 Release) is finally here for existing customers! It seems Microsoft is following in the...

SQL Updates Made Easy Using Excel
Have you ever setup several inventory items in Dynamics GP and realized after the fact that you have assigned the...

Troubleshooting for multicurrency intercompany balancing
A common complaint at month end is the process of reconciling intercompany accounts. We hear that it’s painful, particularly when...
Microsoft Office 365 Collaboration – Office 365 Groups, Microsoft Teams, SharePoint Team Sites and Yammer
There are several apps in Office 365 which provide collaboration features and support to enable the collaboration within different teams...

Reconciling the General Ledger with the Payables Subledger Using SmartList Builder
For those of you who have clients that use SmartList Builder, you can create a SmartList that will help those...

NetSuite webcast (4/17): Accounts payable automation for NetSuite
In today’s mobile and digital environment, having information readily at your fingertips can be the difference between recording a profit...

On-Hand Inquiry Transactional Review in Microsoft Dynamics AX (365)
During each project, it is inevitable you eventually find yourself looking at the on-hand inquiry form within the inventory management...

How to Change a Vendor Type in Microsoft Dynamics AX (365)
During a go live it is possible when migrating vendor master data from a legacy system to Dynamics 365 that...

Outlook App brings Microsoft Dynamics 365 functionality into your most-used email applications
Whether you’re a seasoned Microsoft Dynamics user or new to Microsoft Dynamics 365 for Customer Engagement (formerly known as Dynamics...

Dynamics 365 Relevance Search
Enabling users to find the information they need has been streamed with Dynamics 365 Relevance Search. While leveraging Azure to...

PM_Key_MSTR error when Posting a Payables Batch
Welcome, I hope everyone is having a great day, but if you’ve found this blog chances are you have a...

NetSuite – How to find fixed assets in a Journal Entry
Do you need to know which fixed assets are used in the calculation of the Depreciation Journal Entry in NetSuite?...

Navigating through NetSuite Faster (Part 1): Nine tips using NetSuite global search
With the vast number of features and tools included in the NetSuite platform, finding a particular page or record can...

Top Ten New Features in the NetSuite 2018.1 Release
It is that time of year again, upgrade season. NetSuite 2018.1 is right around the corner. For those who do...

Can’t miss education for SuiteWorld 18
NetSuite’s SuiteWorld conference is coming soon, April 23rd – 26th in Las Vegas, NV. As a Gold Sponsor of the...

GDPR – What is it? Why should you care? Who does is apply to? When does this go into effect? Where do these rules apply?
The General Data Protection Recovery Act, or GDPR, is a new regulation that goes into effect on May 25, 2018....

Creating an aggregate data entity
In this article we will explore the aggregate data entity creation in Dynamics 365 for Finance and Operations, Enterprise Edition...

General Ledger Data Extract Too Large for SmartList
The typical scenario goes something like this: The auditors have requested that you give them an excel file that contains...

The Art of Dunning in NetSuite
One of the biggest headaches businesses face is collecting outstanding debts from customers. Most businesses experience the struggle of collecting...
Dunning on Customers in NetSuite
Best Use of Dunning on Customers Before configuring Dunning, users must decide to evaluate and collect AR on either the...

Dunning Levels in NetSuite
Best Use of Dunning Levels Once the decision to implement NetSuite’s Dunning Module is made, Dunning levels must be created....

Dexterity: Setting a Range on a Composite Field in Dynamics GP
This week, I faced a Dexterity customization for Dynamics GP in which I needed to set a range on the...

NetSuite Application Performance Management
Is your instance of NetSuite running multiple scripts and workflows? Are your experiencing slow page loading times? Do you have a...

4 Things You Need to Know About the FAM 17.2 Bundle Update
The Fixed Asset Management bundle provided by NetSuite has seen some major changes in the latest 17.2 release. These are...
Two Different Apps – Microsoft Outlook and Outlook Web App
RSM recently helped resolve an Office 365 case related to the creation of an Outlook group intended to enable collaboration among select...

Microsoft Dynamics GP – Fixed Asset screen freezing
Occasionally, RSM receives reports from clients that their Microsoft Dynamics GP fixed asset screen is experiencing stalling, or freezing altogether....
Allocating Items on Sales Order Based on Order Priority in NetSuite
NetSuite can provide many different ways to allocate items on a sales order. One common request is to allocate items...

Form Controls in Microsoft Dynamics 365
Form controls for text fields Microsoft is placing a greater emphasis on enhancing user experience while saving time, energy, and...

Dynamics GP OData Security
OData is a great new feature in GP 2016 which allows you to expose your GP data to any OData...

How to configure OData in Microsoft Dynamics GP 2016
One of the best new features in the release of Dynamics GP 2016 is the new OData service. If you...

So your Dynamics GP Web Client certificate expired?
Given that the Dynamics GP web client came out in 2013, we’re seeing that some of the certificates used on...
Office 365 – Employee Portal, Microsoft Teams and SharePoint
Recently, one of our clients shared with us that they will start building their new employee portal using Microsoft Teams....

NetSuite webcast (2/22): Saved searches tips & tricks for NetSuite
Whether you’re a user or administrator using NetSuite, you’ll find your day much easier if you’ve mastered a few tips...

Important Information Regarding NetSuite Release 2018.1
As you may have noticed during your last login, NetSuite has announced their 2018.1 release dates. We’ve summarized some of...

How to Update Existing Word Templates in Dynamics 365 CRM
With the introduction of word templates in Microsoft Dynamics CRM 2016, it allowed for easier reporting and the ability to...

Data entry errors exist – Dynamics GP
I have received several calls about a Payables Check Batch that was interrupted and sent to Batch Recovery. In Batch...
Office 365 – Document Life Cycle
Document Life Cycle is the process and set of various stages that a document goes through when a new document...

How to add Calendar Control in Microsoft Dynamics 365
With usage of mobile phones and tablets increasing in popularity for businesses across the world, there is higher demand for...

How Does Microsoft Dynamics 365 CRM Fit into ERP?
Microsoft Dynamics 365 as a suite of applications has shifted dramatically and rapidly in the last few years. With so...

Dynamics GP Payroll: “There are no Checks in this range to void”
Recently, I ran into an unusual problem where a client entered a manual check to adjust an employee’s pay record,...

NetSuite Approval Workflow Hints
NetSuite empowers users to create approval workflows for a variety of transactions that can be as simple or as complicated...

NetSuite webcast (1/30): Change management post go live
You made it through a successful launch of your NetSuite project. Users are happy and you’re delivering all the great...

Inventory Count Approval Routing in NetSuite
Inventory Adjustments are GL posting transactions that can have a significant impact to financials. There is currently no approval ability for...
Microsoft Sway Application Simplifies Communications
The Microsoft Sway application is included in most Office 365 plans, but many organization have struggled to find a purpose...

Office 365 Error – “Additions to this Web site have been blocked” – Mystery Solved
Recently, we encountered a very misleading error from SharePoint Online / Office 365 which took a long time to figure...

Digital transformation enables customer engagement
Customer engagement is evolving. Everyone is mobile, everyone is social, people trust opinions from their friends and peers more than...

Digital Transformation Brings Modern, Next-Generation, Enterprise-Ready Intelligence
The concept of digital transformation is changing businesses across the country. Technology is transforming our personal lives with apps and...

Driving digital transformation through enabling technologies
There is a fundamental shift changing in modern financial applications and the primary driver is the concept of digital transformation....

Leveraging Microsoft Dynamics 365 Field Services for Patient and Health Provider Services
Microsoft Dynamics 365 Field Services (Field Services) is a magnificent Dynamics CRM capability that enables organizations to optimize their field...

Microsoft Dynamics GP Refunds Made Easy
There’s no need to struggle with processing customer refunds anymore. Microsoft Dynamics GP includes a module called Refunds that is...

In-Transit Inventory Transfers Locked
Have you ever had to modify or delete an In-Transit Inventory record that was locked in the editing status or...

Audit Tracking in Microsoft Dynamics GP
Have your auditors ever asked to see a report that shows changes made to your setup windows or any changes...

Revenue recognition for projects
A common scenario for users of the Projects module in Microsoft Dynamics 365 for Finance and Operations, Enterprise edition is...

Building the Foundation for Dynamics GP Manufacturing: Things to Consider Before You Begin
Welcome to the wonderful world of manufacturing in Dynamics GP! This series is designed to help you build the foundation...

Year-end processing in NetSuite: Webcast – Dec. 7th
Live Webcast: Year-end processing with NetSuite RSM is offering our annual NetSuite year-end webcast. This complimentary webcast will focus on...

Exporting a Full GL Detail for your Auditor
It’s that time of year again. No, not the Holidays just yet! It is your auditors! This is the time...

Giving it More Than 100% – Sales Teams and Partners
There are a few instances in NetSuite when you may need to calculate contribution percentages. The typical examples are Sales...

Power Query in Excel for Microsoft Dynamics AX 2012
One of the key legacy support items is extracting data from Microsoft Dynamics AX 2012. For our purposes, we will...

Power Query in Excel for Microsoft Dynamics for Finance and Operations, Enterprise edition
One of the continuing ways to extract data from Microsoft Dynamics 365 for Finance and Operation, Enterprise edition is to...

Power Pivot Data Exploration in Excel for Microsoft Dynamics for Finance and Operations, Enterprise edition
One of the continuing ways to extract data from Microsoft Dynamics 365 for Finance and Operation, Enterprise edition is to...

Power Pivot Data Exploration in Excel for Microsoft Dynamics AX 2012
One of the key legacy support items is extracting data from Microsoft Dynamics AX 2012. For our purposes, we will...

Be a Saved Search wizard in NetSuite – Webcast Oct. 31st
Whether you’re a user or administrator using NetSuite, you’ll find your day much easier if you’ve mastered a few tips...

Transitioning from Customer Support Representative to Customer Advocate/First Choice Advisor Part II
It’s not enough to get your support team to shift from a mindset of Customer Representative to Customer Advocate/Advisor; you...

Transitioning from Customer Support Representative to Customer Advocate/First Choice Advisor Part I
Those of us who are Microsoft Dynamics GP support professionals know all too well the pressure to take as many...
Exploring Visualizations for Power BI
When working with Power BI, a great way to test the functionality is to attach your desktop to a sample...

Joining Windows 10 Devices to the New Microsoft Azure Active Directory – Part 1
Configuring Azure Active Directory for AD Join Microsoft has made sweeping structural changes within the new Microsoft Azure portal. Gone...

10 Things Microsoft Dynamics GP Users Should Know About SmartLists
Whether you’re new to Microsoft Dynamics GP or have been using the program for a while, you may have found...

New Apple Update Creating Issues with Office 365 and Exchange 2016
The new iOS 11 Apple update was released this week and some users are experiencing issues with Office 365 and...

Digital Transformation – What Does This Do if You’re Using Dynamics 365 Enterprise?
Digital Transformation is the profound transformation of business and organizational activities, processes, competencies and models to fully leverage digital technologies. ...

NetSuite release 2017.2 is coming your way
As you may have noticed during your last login, NetSuite has announced their 2017.2 release dates. You can find the...

Microsoft Dynamics 365: Update Dangers Using X++ Code
The programming for update statements has quite a punch in X++ code for Microsoft Dynamics 365 for Finance and Operations...

Microsoft Dynamics 365 for Finance and Operations: Data Entities
Data entities are a new concept in Microsoft Dynamics 365 for Finance and Operations. They replace previous concepts in Microsoft...

Microsoft Dynamics Lifecycle Services Demo Cloud Environments
Oh no! You’ve been asked to perform a demonstration on Microsoft Dynamics 365 for Finance and Operations, Enterprise edition tomorrow...

Automated Location Assignment Feature in NetSuite
For many years, wholesales and distribution NetSuite customers have had to build scripted solutions in NetSuite to apply logic to...

Optimizing your business with NetSuite CRM – Webcast
Learn how NetSuite CRM can increase employee efficiency and enhance the customer experience Implementing a new ERP system can be...

Printing in Landscape Using Advanced PDFs
In NetSuite, there is a universal preference that determines if your transactions print portrait or landscape. If you go to Setup -> Company...

Microsoft Dynamics 365: Troubleshooting Workflow
The workflow process is vastly expanded in Microsoft Dynamics 365 for Finance and Operations (MsDyn365). The built-in capabilities of line...

Dynamics 365 for Finance and Operations: Using the Excel Data Connector
The new Microsoft Dynamics 365 for Operations and Finance includes several Microsoft integrations that make doing work easier. One of...

Introducing Microsoft Dynamics 365 for Talent: Leave and Absence Management
Microsoft recently introduced the Microsoft Dynamics 365 for Talent technical preview. As you can imagine, there are so many new...

SSRS – MEM Trial Balance Reports
Several of our Dynamics GP customers who have deployed the Binary Stream Multi-Entity module have experienced a random sort order...

Dynamics GP: Where is my 3rd Party Table?
I encountered a “cannot find table” error on a custom table and I was especially confused because I had just...

What’s New with Fixed Assets in GP 2016 R2?
One of the coolest new features in GP 2016 R2 is the POP to Fixed Assets link which now includes...

Import data into NetSuite: tips & tricks webcast July 19th
NetSuite users can import data into NetSuite in a variety of ways, from comma-separated value (CSV) files to integrations using...
Four Ways to Leverage Your Existing Infrastructure for Office 365 Authentication
When it comes to having a successful Microsoft Office 365 deployment, it is important to keep the end user’s experience...

Microsoft Dynamics 365 for Sales : Error When Adding a New User
This error message occurred when I was in the Office 365 Admin Portal adding licenses to several users for our...

Troubleshoot Master Planning in Microsoft Dynamics 365
It happened to me and it could happen to you. Starting a new Microsoft Dynamics 365 (formerly Dynamics AX) implementation...

Wells Fargo Payment Manager
We have had several requests to assist clients with generating an ACH file out of Dynamics GP in the Wells...

Setup and Enable in Dynamics 365 for Operations
A behind the scenes feature in Microsoft Dynamics 365 for Operations (MsDyn365) is the setup and enabling for existing and...

Management Reporter Login Issues after Dynamics GP Password Change
When using the Dynamics GP Legacy integration in Management Reporter, the user is asked to enter their GP UserID and...

Leveraging NetSuite for ASC 606 adoption | June 21 webcast
The effective date of Accounting Standards Codification (ASC) 606 is coming soon, bringing new a revenue recognition standard to both...

NetSuite Tips and Tricks: Advanced Product Searching on Transaction Lines
NetSuite offers users many ways to search for items on transaction lines. Below are some of the more commonly-known methods...

Microsoft Dynamics 365 for Operations: Service Orders
The Service management module of Microsoft Dynamics 365 for Operations is a solution for any company that provides service after...

A Basic Primer for Setting up Intercompany Transactions
We all have an idea what intercompany transactions are. You have a large parent company and a corporate office. The...

Security in Microsoft Dynamics 365 for Operations
Introduction Security in Microsoft Dynamics365 for Operations is essential now. Securing the objects that you have created is a requirement...

Allocations across a Main Account
In accounting, there are main accounts that are utilized across multiple areas of the company. The accounts may be...

Recording Credit Card Transactions
Importing those voluminous monthly credit card transactions Are you like many customers dreading the recording of the American Express or...

Microsoft Azure Internet of Things (IoT)
As compute power continues to grow at an exponential rate, companies are constantly looking for new ways to harness and...

Five step model for revenue recognition for ASC 606 with NetSuite
60% of software companies running NetSuite haven’t started on the path to ASC 606 compliance yet. There’s still time to...
Posting Time by Project Type in NetSuite
The Post Time functionality makes it easy to create a GL impacting transaction to record the labor costs of projects....

Optimize Your Supply Chain with NetSuite
In today’s competitive business world, industry-leading organizations continually look for ways to create a competitive advantage over their competition. In...

6 Takeaways from SuiteWorld17 + Keynote Recordings
There are a lot of topics to write about coming out of NetSuite’s SuiteWorld conference, but thought I’d do a quick...
Enterprise Content Management (ECM) and SharePoint for Financial Institutions
Microsoft SharePoint is an easy to use intranet/extranet, and internet sites that make it simple for everyone to access critical information, regardless of...

Using Microsoft To-Do for effective task management
A new task management product, Microsoft To-Do, wasn’t recently released by Microsoft and is available to consumers and Office 365 subscribers. To-Do...

Top 5 List of Commonly Used SQL Scripts in Microsoft Dynamics GP
Favorite SQL Scripts These are my most commonly used SQL scripts on every Microsoft Dynamics GP implementation that I perform,...

Inventory Lots and IV Reconcile in Dynamics GP
What do you do if you haven’t run IV Reconcile after checking “Enable multiple bins” in Inventory Control Setup and...

Some SmartConnect Errors and How to Fix Them
Here are a few errors that may be encountered when using SmartConnect and some simple steps to try and fix...
Data Loss Prevention (DLP) policies in Office 365
In today’s society, technology plays a vital role in our everyday routine and it is heavily depended upon. What we tend...

SQL 2016 with Microsoft Dynamics GP (CAUTION!!)
Don’t let the caution headline lead you to believe SQL Server 2016 and Microsoft Dynamics GP 2016 are not compatible;...

Ensure Employees’ Payroll Tax Codes Match the Tax Treatment Record
I’ve come across several instances when a client calls and says that they have not withheld the proper amount of...

Microsoft Dynamics ERP Implementation Tips
The decision to do an ERP Implementation is daunting for many Clients and once the decision is made to proceed,...

Microsoft Dynamics CRM 2015, 2016 and 365 Legacy Form Rendering
As costs have come down to much more reasonable prices for cloud hosted business applications, more and more organizations are...

Dynamics AX: Sending XML Files to a Microsoft Message Queue
I’ve been working with Scribe Insight to integrate Microsoft Dynamics AX 2012 with Microsoft Dynamics CRM 2016. I’m using...

Restricting Access to NetSuite
An important part of any implementation is defining the roles that employees will use and configuring the permissions to fit...

Microsoft Dynamics GP 2013: Fixed Asset Depreciation Reports
With the release of Microsoft Dynamics GP 2013, Microsoft introduced many new enhancements to the Fixed Asset module. One of...

Microsoft Dynamics CRM and Resco Mobile CRM: Using Dynamic Map Pins
Recently, I worked on a new Resco implementation for one of our clients. During UAT, their end users saw a...

Microsoft Dynamics CRM/Dynamics 365: Advanced Find or Workflow
If you have ever built a large advanced find in Dynamics CRM, you know how time consuming it can be....

NetSuite for Retail – seamless omnichannel platform
RSM’s survey of retail executives was recently released and showed the importance retail leaders place on omnichannel retail as a...

Getting Started with Microsoft Flow
Last month I used Microsoft Flow for the first time, and all I can say is, “Where have you been...

Microsoft Dynamics 365: Utilizing Workflow Templates for Cases
When it comes to case management in Microsoft Dynamics 365, Dynamics CRM 2016, 2015, and/or 2013, workflows can be greatly...

Microsoft Dynamics CRM And Resco Mobile CRM: Using Global Maps and Location Services
Resco Mobile CRM (Resco) has a Global Maps area that can be added to the home screen. When adding the...

Dynamics CRM Security Roles and Removing Quote Products
If you have ever wanted to restrict a user’s ability to remove a quote product from a quote you may...

Dynamics 365 for Operations: Using the Investment Project
The Project Module and accounting in Microsoft Dynamics 365 for Operations can be very valuable for any kind of business,...

Microsoft Dynamics CRM FetchXML Link Entities
Anyone who develops reports in Microsoft Dynamics CRM Online knows that the data sets have to be written in FetchXML;...

User Interface Design For Microsoft Dynamics 365 for Operations
Introduction to User Interface Design Programming the user interface is a requirement of new development within Microsoft Dynamics 365 for...

Microsoft Dynamics 365 for Operations: Financial Reports (formerly Management Reporter)
First thing is to get used to the new name: Financial Reports. Management Reporter was renamed Financial Reports in Microsoft...

X++ Control Statements For Microsoft Dynamics 365 for Operations
Introduction to X++ Control Statements Programming control statements are the source of many operations within Microsoft Dynamics 365 for Operations...

Activating a Hardware Station in Dynamics 365 for Operations – Part Two
Hardware Station in Dynamics 365 Part one covered activating and installing the Modern POS in Microsoft Dynamics 365 for Operations....

Case Management In Microsoft Dynamics 365 For Customer Service
In an effort to increase the efficiency of Customer Service operations in Microsoft Dynamics 365, Microsoft offers an extensive set...

Editable Subgrids: Out-of-Box vs Third Party Solutions
The Dynamics 365 debate of the year: Should I go out-of-box for editable subgrids or use a third party solution? Which...

Scan-Back and Vendor-Funded Coupon in Microsoft Dynamics AX
Dynamics AX accelerator for retailers. In a retail environment, manufacturers and/or vendors will often provide funding for the retailer to...

Roaming VMware Horizon credentials with Microsoft Office Click-to-Run
One of the great things about Office 365 and VMware Horizon is that it makes life as the IT administrator...

Free Text Invoicing in Microsoft Dynamics 365 for Operations
A free text invoice is an invoice that is not attached to a sales order and does not require a...

Creating Mobile Device Menu Items in Dynamics 365 for Operations
If you’ve taken a look at the Warehouse management module in Dynamics 365 for Operations and the screen to create...

Tips to Ensure User Adoption of Microsoft Dynamics 365
The key to any successful business application implementation, Microsoft Dynamics 365 included, is user adoption. I have found that user...

Visual Studio Development Environment in Dynamics 365 for Operations
Microsoft Dynamics 365 for Operations is the new version of Microsoft Dynamics AX. It is a cloud-based enterprise solution. This...

Activating a Hardware Station in Dynamics 365 for Operations
Last week, I was tasked with activating a hardware station in Dynamics 365 for Operations. Easy, right? Dynamics 365 for...
Information Rights Management (IRM) for Office 365
Information Rights Management (IRM) is a form of IT security technology used to protect documents containing sensitive information from unauthorized...

Managing Restricted Funds in Microsoft Dynamics GP
Reporting tools available in Microsoft Dynamics GP can assist nonprofits in overcoming the challenge of managing restricted funds and maintaining...

Dynamics 365 Business Rules
Introduction of Business Rules in Dynamics CRM was a game changer in Dynamics CRM 2013. Business Rules have really made...

Database Manipulation in Microsoft Dynamics 365 for Operations
Data manipulation in Microsoft Dynamics 365 for Operations (MsDyn365) empowers developers with the tools to insert, update, and delete data...

What’s Next for Microsoft Dynamics 365 for Sales?
Microsoft recently introduced the Dynamics 365 Roadmap. The roadmap gives you a glimpse of features that have already been released...

Dynamics GP: Adding EFT Data to the Vendor Master Trigger
Beginning with Microsoft Dynamics GP 2010, Microsoft began offering the Professional Services Tools Library (PSTL) for free. The PSTL includes...

Microsoft Dynamics 365 for Operations: Using Task Recorder
The concept of the task recorder is not new, however, with the release of Microsoft Dynamics 365 for Operations, the...

Dynamics AX: Configuring Product Search in Enterprise Portal
Since being introduced in October of 2002, Enterprise Portal (“EP”) has enabled employees, customers, and vendors to interact directly with...

Microsoft Dynamics AX: Item Data Management in a Franchise Environment
Microsoft Dynamics AX uses many tables and fields to house item data and perform Dynamics AX operations. This is useful...

Microsoft Dynamics AX: Pricing Strategies for Franchises
When performing a Microsoft Dynamics AX implementation for a company with franchises, there can be some challenges for implementing and...

Requirements Gathering in Project Planning – What’s a Soffit?
If your client does not know what a ‘soffit’ is, that’s your problem, not theirs. I arrived home the other...

Microsoft Dynamics GP Fix for W-2 Form RS Numbers
I was recently approached by one of our Dynamics GP functionality consultants looking for a solution to convert the W2...

Using Financial Dimensions in Financial Report Designer
As we go into 2017, I’m sure everyone is still getting comfortable with the new name, Financial Report Designer. In...

Layer2 Cloud Connector for SharePoint and Office 365
Line-of-business connectivity and enterprise search are core capabilities within SharePoint that drive user adoption, productivity and ROI across the organization....

Replenishing Inventory Using NetSuite Transfer Orders
In NetSuite’s 2016.2 release, a new feature was introduced that can greatly improve inventory management for wholesale distributors and retailers....

Microsoft Dynamics 365 On-Premises is Released
Those eagerly waiting to try out Microsoft Dynamics 365 on-premises can now download the update from Microsoft and play with...

Retail Scheduler Parameters in Microsoft Dynamics 365 for Operations
Setting up retail parameters in Microsoft Dynamics 365 for Operations is one of the first steps for setting up retail...
5 Reasons You and Your Auditor Will Love NetSuite
“Greg Cole, the Auditor is here!” said the CFO as I would walk through the silence of my newest client’s...

Create A Video In Microsoft PowerPoint Using Office Mix
Microsoft PowerPoint is one of the most frequently used slide-based presentation programs on the market. It’s likely that, at some...

Dynamics 365 For Operations Location Wizard Improves Warehouse Management
If you used the Location wizard as part of Dynamics AX 2012 R2, or afterwards for standard warehousing, I think...

Microsoft Dynamics CRM — The Necessity for Software Training
All too many times, I have seen software implementation projects fail to gain User Adoption. There can be many reasons...

Microsoft Dynamics CRM — Why is Project Management Important?
Have you ever seen a Work Plan or SOW for a Microsoft Dynamics CRM implementation, and there were line items...

Microsoft Dynamics CRM as XRM
We have all come to know and love Microsoft Dynamics CRM as one of the leaders in the CRM Market. ...

Data Management in Microsoft Dynamics 365 for Operations
This article is a continuation of the discussion about the new workspace called Data Management in Microsoft Dynamics 365 for...

Save Time Importing Records with Mail Merge Macro
Have you ever needed to import thousands of records that can’t be done using Integration Manager? And have you thought...

Health and Human Services Compliance Is A Critical Part Of Your Software
According to an article on NJ.com, the U.S. Department of Health and Human Services examination of 100 claims submitted by...

Mass Update GL Account Segments in Microsoft Dynamics GP
Chances are when you began using Microsoft Dynamics GP and loaded the chart of accounts, you may not have thought...

Microsoft Dynamics GP: Advanced Interfund Management
Microsoft Dynamics GP’s Interfund Management module is often part of the equation for implementing Dynamics GP in not- for-profit entities...

#TechnologyDay – Increased speed of applications delivered over the internet
Today is National Technology Day (#TechnologyDay), so I thought I’d weigh in on one trend I see for 2017 and...

Financial Report Designer
In my last blog, I talked about the changes to Management Reporter 2012 for Dynamics AX and Dynamics 365 for...

How to Customize EFT Files in Microsoft Dynamics GP
Out of the box, Dynamics GP supports several formats, which on most occasions will work, with some effort in setup....
Out of Office, Still in Control with AP and Payment Automation
Earlier in 2016, we wrote about how employees are enjoying the benefits of telecommuting thanks to advances in cloud computing and mobile technology....

Preventing duplicate transaction numbers in NetSuite
It seems simple enough – you want every transaction to have a unique transaction number. So, you go to your...

What Oracle NetSuite will look like in 2017
Last Thursday, Dec. 1st, Oracle held its first public meeting to talk about the future of NetSuite now that it...

Microsoft Dynamics 365 for Operations Tips and Tricks – November 2016
As a trainer, I have noticed a common theme while training newer AX users, as well as long time AX...

Microsoft Dynamics 365 for Operations: Data Management and Excel
This article is a continuation of the discussion about the new workspace called Data Management in Microsoft Dynamics 365 for...

RSM now an authorized SuiteCommerce Advanced developer
As NetSuite Worldwide Partner of the Year 3 of the last 4 years RSM is now authorized to implement SuiteCommerce...
Work Smart with the Microsoft Surface Product Family
There is more to the Microsoft Surface family of products than just tablets! Microsoft envisioned a complete line of products...

Migrating to Advanced Revenue Management (ARM) – are you ready?
Now that we’re into the third release of Advanced Revenue Management (ARM), we’re starting to hear more and more people...

Field Service UI & Functionality Enhanced for Microsoft Dynamics 365
Field Service for Microsoft Dynamics 365 is scheduled to be released on Tuesday, November 29, 2016. Below are the new...

Microsoft Dynamics 365: The Next Generation of Cloud Based Business Apps
Microsoft has officially released the Dynamics 365 Suite as of November 1, 2016 and it’s creating a significant amount of...

Microsoft Dynamics 365: How to Keep your Data Clean
When working with applications like Microsoft Dynamics 365, one of the most common concerns we hear is, “how do we keep...

What’s New in Microsoft Dynamics 365 CRM?
On November 1, 2016, Microsoft Dynamics CRM went through a re-branding to follow along with the Office 365 product offerings....

Connecting to Dynamics CRM Online From Scribe Online CRM Adapter
I had run into an issue that was new for me. I had been connected to a test Microsoft Dynamics...

Dynamics GP — PM_Key_MSTR error when Posting a Payables Batch
Welcome, I hope everyone is having a great day, but if you’ve found this blog chances are you have a...

Reflections on Microsoft Dynamics CRM and a Look at the Future
I was recently preparing for a demo to a prospective client. During my personal introduction, I told the people I...

Microsoft Dynamics 365 Improvements From Microsoft Dynamics AX 2012
Microsoft made some significant improvements to the new Dynamics 365 for Operations development environment, and I want to take this...

Improvements to Management Reporter in Dynamics 365 for Operations
As a Management Reporter user, I was excited to see the changes to Management Reporter 2012 for Dynamics AX and...

Work Templates and Location Directives in Dynamics 365 for Operations
When you use Warehouse Management in Dynamics 365 for Operations you are required to set up and use both Work...

Microsoft Dynamics 365 Product Suite – 6 Amazing New Products
You may be wondering what the difference is between Microsoft Dynamics 365 for Operations, Microsoft Dynamics 365 Enterprise Edition, and...

Dynamics 365 Licensing Models
In a previous post, we reviewed each of the products that make up Dynamics 365; let’s discuss the two licensing...

Exception Handling In X++ with Dynamics 365 for Operations
Not everything goes as planned in life or in programming. Programmers begin writing code to perform some automated task and...

Fully Utilizing the Business Process Flow in Microsoft Dynamics CRM
Business process flows (BPF) have been around since Microsoft Dynamics CRM 2013 and conditional branching was added to business process...

Microsoft Dynamics CRM 2015: Case Timer Functionality
Recently during an online implementation of Microsoft Dynamics CRM 2015, we had a client who wanted a timer to make...

Microsoft Dynamics CRM 2016 Online: Word Templates are Awesome!
Word Templates are a new feature of Microsoft Dynamics CRM Online 2016. Microsoft has great documentation on how to create...

Microsoft Dynamics CRM 2015: Using Branching Business Process Flows
During a recent online implementation of Microsoft Dynamics CRM 2015 I had a client who needed to have a different...

Microsoft Dynamics 365 Online: The New Hub for ERP and CRM
Microsoft Dynamics 365 Online was released Tuesday, Nov 1, 2016, and is packed with plenty of new features, functionalities and...

Microsoft Dynamics CRM Lead Capture Using ClickDimensions Web Forms
ClickDimensions is consistently the top-rated Microsoft-certified marketing automation application for Microsoft Dynamics CRM, and for good reason. As an embedded...

Slicing/Dicing Your Financial Reports by Custom Segments in NetSuite
In 2015, NetSuite introduced the concept of custom segments, which allowed users to post transactions to more than just the...

Use Office 365 Admin App to Manage your Dynamics CRM Online
If you are a Microsoft Dynamics CRM Online organization, Microsoft created a mobile application that allows a system administrator to...

Troubleshooting Data Sync Issues Management Reporter and Dynamics GP
You’ve just closed the month or year for one or more of your entities in Dynamics GP and you’re now...

Importing Payroll Deductions and Benefits in Microsoft Dynamics GP
Those of you who use the Microsoft Dynamics GP Human Resources Module in conjunction with payroll are aware of the...

Using FetchXML to Access User Information from the Resources Party List
I was recently tasked with creating an SSRS report for an organization with Microsoft Dynamics CRM 2015 on-premise. The report...

Using Dynamics AX Data Import Export Module to Upload Fixed Assets
Uploading legacy data into Microsoft Dynamics AX is not always an easy task. For example, when you want to upload...

Overlooked steps for an Office 365 exchange migration
With more and more organizations moving to Office 365 and taking advantage of the cloud and more and more online...

Simplifying your Chart of Accounts in NetSuite
If there is one thing an accountant holds dearly to their heart, it is their chart of accounts. Believe me,...

Optimizing MR Report Speed after FRX Migration with Dynamics GP
Frustrated that your Management Reporter reports are running extremely slow after FRx Migration? Here are some easy tips to help...
Introducing the New Cloud POS in Microsoft Dynamics AX
With the new version of Microsoft Dynamics AX, one of the most exciting changes is Cloud POS. Microsoft has replaced...

Vendor/Customer Modifier and/or Combiner in Dynamics GP
Have you ever created a new vendor and realized weeks later that you had already created that vendor under another...

In Dynamics GP – Depreciation Expense is Low and Depreciation Button Unavailable
You created your GL Batch from FA and you notice Depreciation is lower than expected. Possible causes: system interruption, lost...

Microsoft Dynamics CRM: Two Easy Ways to Improve CRM Forms
Overview HTML Web Resources are not new to Microsoft Dynamics CRM, but I believe they are an often overlooked way to...

Dynamics AX 2012 – How to Correct a Posted Invoice
Microsoft Dynamics AX employs strict controls around the modification of posted financial transactions, but there are times when we make...

Microsoft Dynamics CRM Configuration – Basic Tips Part 3
This is the last part in the Microsoft Dynamics CRM configuration series. The topics covered here go a little deeper…perhaps...

Restricting User View in Microsoft Dynamics AX 2012
A client in the jewelry retail space recently was faced with the requirement of securing a specific warehouse location’s on-hand...

Microsoft Dynamics CRM Configuration – Basic Tips Part 2
This is the second part of a 3 part series. We are discussing some tips and best practices when it...

Microsoft Dynamics AX 2012 — Using The Number Sequence Framework to Identify Transactions
Microsoft Dynamics AX has a number sequence framework to generate alphanumeric number sequences that are used to identify transactions like...

Microsoft Dynamics CRM 2015: Finding Inactive Accounts
One of our CRM 2015 Service Pack 1 clients has recently begun to clean their data by merging duplicate account...

Migrating Custom Code to Microsoft Dynamics AX 2012
Overview A Microsoft Dynamics AX 2012 upgrade contains several steps, as shown in the following illustration. Planning Code...

Difference between Microsoft Dynamics CRM 2015 and Service Pack 1
Microsoft Dynamics CRM, like all business software, is a wasted resource if it is not adopted by the organization’s user....

Microsoft Dynamics CRM 2015 – The Future of the Dialog
As I look at the current feature set for Microsoft Dynamics-CRM, it seems that the existing dialog functionality doesn’t fit. ...

Incorporating the 8D Process in Microsoft Dynamics AX 2012
One of the most popular processes for managing quality assurance issues is the 8D process or the eight disciplines process...

Product Reservations for each Sales Order in Microsoft Dynamics-AX
Many businesses today are running lean, especially with regard to stocking inventory. At times, businesses can find themselves with low...

Microsoft Dynamics CRM 2015 Features: Business Process Flows
The Business Process Flows were created for Microsoft Dynamics 2013. As with most new features, the 2013 version of Business...

The Underutilized “Case” in Microsoft Dynamics CRM
I find it interesting that Microsoft Dynamics CRM tends to be the ‘Silver Bullet’ to most ERP issues. This is the...

Microsoft Dynamics CRM Configuration – Basic Tips Part 1
As you begin to dive into Microsoft Dynamics CRM configuration, it is helpful to follow a few standards, best practices...

Let NetSuite matrix items simplify your item master
Do you sell items that come in different colors, sizes, lengths, memory size or any other differentiating qualities? Have you...

How to make mass changes to decimal places for inventory items in Microsoft Dynamics GP
A client once asked me if there was a way to change the quantity decimals places on the item maintenance...

Presidential Election – Oracle Acquisition of NetSuite – should I put my NetSuite ERP purchase on hold?
I’ve been following a number of things over the past couple of months since Oracle announced the acquisition of NetSuite....

Is Revalue Inventory Standard Cost Really 100% Complete?
Let’s say your company uses standard costing to help identify possible issues with item costs. You are the account administrator...

Can self-driving cars boost productivity?
The age of self-driving cars is among us. While first we thought it was a fantasy and wouldn’t happen in...

Managing Vendor Rebates with the NetSuite Rebates Management SuiteApp
Many distribution companies, especially those selling industrial products, resell product from manufacturers and are granted rebates from the manufacturers for...

NetSuite Release 2016.2 is Coming! Are You Ready?
If you are a daily user of NetSuite you are most certainly familiar with the twice-yearly New Release portlet on your...

Alert: Avalara discontinuing 1099 services
As of June 2016, Avalara has decided to discontinue its 1099 services. Going forward, Avalara 1099 users will only be...
Training for success in your ERP implementation
The first thing that is often cut in any project is training. The dollars are looked at as expendable. The...

NetSuite Permissions: How to figure out what permissions you need to add to a role
Need a quick and easy way to figure what permissions you need in NetSuite to access specific functionality? Try using this...

Why the Oracle NetSuite deal makes sense
News broke today that Oracle entered into a definitive agreement to acquire NetSuite for approximately $9.3 billion. Coming from a...

Why is NetSuite global search returning results for unrelated transaction numbers?
Have you ever performed a global search in NetSuite for a specific transaction number and received multiple results with seemingly...

Microsoft Dynamics CRM 2016 Online – How to remove “Promote to Admin” hidden security role?
With the recent Spring update to Microsoft Dynamics CRM 2016 Online, we have a new functionality called “Promote to Admin”...

Using Azure Stack to deploy Microsoft Azure on premise
Microsoft Azure Stack enables you to deploy a private Microsoft Azure cloud platform that you can run and manage in...

NetSuite SuiteWorld 2016 Recap
NetSuite’s SuiteWorld conference was held in San Jose, Calif., May 16-19. RSM was a Platinum sponsor at the event which...

Migrating large on-premises SharePoint sites to Office 365
Many organizations have adopted SharePoint, in it’s beginning stages, and today are faced with a lot of content that has grown...

Margin-Based Pricing using Mass Update Feature
Every company strives to achieve healthy profit margins, but this can become a laborious task if they sell thousands or...

NetSuite Has a New Revenue Recognition Engine
New to NetSuite Revenue processing? Advanced Revenue Management automates revenue forecasting, allocation, recognition, reclassification, and auditing through a rule-based event...

NetSuite SRP – Charge Based Project Billing
Have you ever wondered when you would use the Charge Based Billing Project Type in NetSuite? One scenario is when...

ClickDimensions Spring 2016 Updates for Microsoft Dynamics CRM
The ClickDimensions April 2016 release is now available for ClickDimensions customers using Microsoft Dynamics CRM 2011, 2013, 2015 or Dynamics...
Testing for Empty Image Fields with NetSuite Saved Searches
Many companies that sell products want to store images of these products on their NetSuite item record. When these images...

Notification: NetSuite Sandbox eCommerce Testing Issue
It has come to our attention that as of 2016.1, any client that does a sandbox refresh will experience a customer issue with...

Importing Special Language Characters Into NetSuite i.e. Chinese, Korean, Russian, Arabic
If this article was being written in an academic setting, it would probably fall under the shadow of plagiarism. We...
Adding Bing maps in Office 365
Maps are in virtually any app or portal we use on a day-to-day basis. SQL server consumers have utilized this...
Excel services in SharePoint
Imagine a scenario where an organization leverages Microsoft Excel to generate and share reports and charts with their stakeholders and...

How to solve error ID3242: The security token could not be authenticated or authorized when connecting Scribe to Microsoft Dynamics CRM
Are you trying to connect to Microsoft Dynamics CRM from Scribe Insight and getting the error message “ID3242: The security...

When opportunities in Microsoft Dynamics CRM are not part of the business process
Microsoft defines an opportunity as “a lead who is now almost ready to buy – in other words, it’s a...

Today’s mid-market Financial Controller can learn from the past to succeed in the future
The role of the Financial Controller in middle market companies has evolved leaps and bounds in the past decade. Years ago,...

5 things that rock my world in the 2016 Spring Wave of Microsoft Dynamics CRM Online
Microsoft just announced the Microsoft Dynamics CRM Spring 2016 Wave will be available for online customers in quarter 2. There...

Mitigating ERP Implementation Failure through Change Management
There are many points of failure in ERP Implementations. The points of failure revolve around three main areas – people,...
Utilizing your Office 365 investment
Welcome to the cloud, new Office 365 subscriber. Do you know what you actually get with your shiny new subscription? Sure,...

Microsoft Dynamics CRM 2016 feature: Case management just got better
With the released of Microsoft Dynamics CRM 2016, one of the key features is enhancing the customer experience for organizations....

Cumulative Translation Adjustment Exposing the Detail
Cumulative Translation Adjustment Purpose: To provide the detail behind the cumulative adjustment row on the consolidated balance sheet. The Cumulative...

Take advantage of browser profiles in Office 365
“Let me show you what that looks like on our Office 365 tenant!” Many of us in consulting, whether sales,...

Challenges that some Microsoft Dynamics GP users face when creating SmartList reports
Many users struggle when it comes down to creating new SmartLists reports using either SmartList Builder Tool or Microsoft Dynamics...

Microsoft Dynamics CRM for phone mobile app issue: Open activities appear locked
During a recent Microsoft Dynamics CRM 2015 online implementation we stumbled upon an issue with editing Activities in the Dynamics...

Microsoft Dynamics CRM 2016 new signature control feature for phones and tablets
With the release of Microsoft Dynamics CRM 2016, there is a bundle of new features for administrators and developers out-the-box....

Displaying an image captured by the mobile signature control in the Dynamics CRM web and Outlook clients.
The release of Microsoft Dynamics CRM 2016 has introduced some great new functionality, including new controls for the mobile client...

Tips for Setting up Microsoft Dynamics GP multi-currency for use with Management Reporter
Creating translated financial reports in Management Reporter is, in large part, dependent on how you setup multi-currency in Microsoft Dynamics...

NetSuite reporting – dates or periods (part 1)
When running reports (not searches) in NetSuite, there are a few date-related settings that may determine what information you see...

NetSuite reporting – dates or periods (part 2)
While the Report by Period setting in conjunction with the Allow Transaction Date Outside of Posting Period setting can create...

Bundling and transferring sandbox customizations in NetSuite
Bundling allows you to batch up your customizations and configuration as your own personal app and then share them other...

What is Microsoft’s ECM strategy?
Depending on what you read, Microsoft’s ECM (Enterprise Content Management) strategy of cloud first, mobile first which are the tools...
Mass deleting records in NetSuite
If you have erroneous records in NetSuite, don’t waste your time deleting each one-by-one. In NetSuite, it is possible to...

Microsoft Dynamics CRM 2015 Update 0.2 benefits on-premise users
Microsoft Dynamics CRM 2015 update 0.2 is released for on-premises customer. This update contains mostly hotfixes and support functionality. Changes...

Finding the right partner: Your first step on the path to a successful ERP implementation
You’ve identified the need for a new enterprise resource planning (ERP) system, secured upper management’s support, and established the scope...
What is missing from Microsoft Office 2016?
For all of the new features being offered in Microsoft’s rollout of Office 2016 there is one essential tool missing:...

Use owner and access teams to customize group privileges in Microsoft Dynamics CRM
Teams in Microsoft Dynamics CRM are a group of users who can be assigned similar privileges. There can be exceptions...

Are you prepared for Microsoft Dynamics CRM 2016 upgrade?
Microsoft Dynamics CRM 2016 is released, you can read more about the new features and capabilities in this What’s new...

FreeMarker Logic and Advanced PDF/HTML Templates with NetSuite
NetSuite’s Advanced PDF/HTML templates truly empower users with endless options for customizations to printed forms, with the support of FreeMarker....

NetSuite New Release Facts 2016.1
As you may have noticed during your last login, NetSuite has announced their 2016.1 release dates. Firstly find the New...

Considerations when Evaluating Accounts Payable Solutions for NetSuite
Is managing all of your payments becoming too time consuming? Processing checks one way, then processing ACH payments in NetSuite...

Using Shared Calendars in NetSuite
NetSuite has robust calendar capabilities. These Features can be leveraged to coordinate projects internally. Using NetSuite as a calendar has...

NetSuite Customization with Forms and Fields
There are many ways to customize NetSuite, for example companies can publish dashboards, create saved searches, and use workflows to...

Creating Dependent Drop-Down Lists with NetSuite
If you have used or administered NetSuite for any period of time you are well aware of its flexibility with...

Set Custom Layouts within Standard NetSuite Financial Statements
NetSuite provides standard income statements and balance sheets, organized by account type. These may be factually correct reports, but companies...
Does my organization have a disaster recovery solution or a backup solution
By now, I assume we have all heard the statistics that 80% of organizations that face a catastrophic event, without...

Managing floor stock production in Dynamics AX
Production often requires an item for which the quantity is not precisely defined. Usually these are relatively inexpensive items, and...

What’s added in Microsoft Dynamics CRM 2015 Update 1 for online and on-premises users?
In a perfect world, we all want Microsoft Dynamics CRM 2015 Online updates to match Dynamics CRM 2015 on-premises in...

Considerations for successfully implementing NetSuite
Often the management team sponsors overlook critical aspects of implementing a “new breed” enterprise management system such as NetSuite. In...

Backup and disaster recovery for Microsoft Dynamics GP
How do I protect my Microsoft Dynamics GP environment from data loss? The answer, very often is, “It depends.” Each...

Changes to iOS 9 Security May Impact NetSuite for iPhone Users
This week, NetSuite released the following statement about changes to Apple’s security policy that will affect NetSuite customers using NetSuite...

Resolving the issue when Outlook crashes after installing Microsoft Dynamics CRM Client for Outlook
I’ve run into several situations that when installing or updating the Microsoft Dynamics CRM Client for Outlook, immediately after opening...

Setting Field Defaults with Custom Workflows
Custom workflows in NetSuite are designed to be a point and click way to do some of the functions that...

Understanding Microsoft Dynamics GP module integration : Best practices for posting setups
Navigating through the posting process in Microsoft Dynamics GP can be challenging if you do not understand how the system...

Displaying external item numbers on purchase orders in Microsoft Dynamics AX
The ability to increase communication between customers and vendors is always essential. Microsoft Dynamics AX allows its users to better...

Publishing custom Saved Searches to the Customer Center in NetSuite
Most people love the word “free,” but things that you get for free often don’t provide a whole lot of value. ...

Manage Projects, Resources, Profitability and Billing with NetSuite
Has managing projects become a cumbersome process? Are you managing projects in one system, resources in another and billing somewhere...

The new features in Microsoft Dynamics GP 2015 R2 and why you should stay current
Microsoft Dynamics GP is on track for the promise of bi-annual significant update releases. Adding many new features with the...

Managing customer furnished material in Microsoft Dynamics AX
While Dynamics AX is a very comprehensive ERP solution, there is really no completely tailored solution for managing customer furnished...

When no customer service is great customer service and how to know what’s most effective for your business
I am flying back from my family’s usual stomping ground, Disney World. During this trip, we utilized for the first...

Deleting a company in Management Reporter 2012
Management Reporter is a common tool for the Microsoft Dynamics ERP solutions, Dynamics AX, Dynamics GP and Dynamics SL alike....

Run your professional services business using NetSuite
NetSuite provides a single platform for professional services firms to run their entire business from lead to project to cash....

Don’t get caught with your phone system down
Many people talk about the dark days of IT as cloudy days. However, the cloud has been a significant improvement...

Increasing communication within NetSuite
Does your business strive for increased communication within your ERP/CRM system? NetSuite offers many different solutions including both out of...

Why health and human services agencies are turning to Microsoft Dynamics CRM for case management
In the Health and Human Services (HHS) industry, there are many investments being made in technology, software and business process...

Changing from a single EFT format to multiple EFT file formats in Microsoft Dynamics GP
We recently had a client who needed to process an EFT payment in Microsoft Dynamics GP to an individual’s personal...

Migrating Data From Your Legacy System to NetSuite
When choosing a new customer relationship management (CRM) solution or enterprise resource planning (ERP) solution, it is inevitable that if you are an existing...
Dissecting the administrator’s Microsoft Office 365 experience with Microsoft Dynamics CRM
Last week I attended the CRMUG Summit in Reno and leda session called Dissecting the Administrator’s Office 365 Experience with...

Tracking contact’s organization history in Microsoft Dynamics CRM Online
Have you ever come across a situation where a contact leaves a company but joins another company that is also...

Think a requisition process is just overhead? Here are 10 ways it drives real value.
At face value a requisition process seems fairly mundane and low priority. In reality it provides a terrific opportunity to...

Microsoft Dynamics GP with single sign on functionality and simplified IT administration
As organizations grow, so do their need for larger, more complex environments. As a result, users are becoming all too...

Creating notes for shipping documents in Microsoft Dynamics AX
Using the Notes functionality within Dynamic AX can be very helpful. Notes can be used to alert warehouse personnel to...

October webcast series – deep dive into the Third Platform
Social, Mobile, Cloud, Big Data and the Internet of Things. You may be using some of these technologies in your...

NetSuite SRP – Project Management Using Generic Resources
Generic Resources are used as place holders until specific resources are identified when project managers and resources planning a project....

IQity for NetSuite – A Collaborative Manufacturing Platform
IQity is a leader of ‘Manufacturing in the Cloud’ solutions and services for SMB enterprises and divisions of large companies....

Designing NetSuite Roles and Permissions: Best Practices and Tips
Assigning permissions in any ERP system is always a balancing act. You want to make sure that your users don’t have...

Storing the “Last Activity” on a Microsoft Dynamics CRM record
One of the most common requests in the xRM world (Download our white paper, Extending CRM: Utilizing xRM to expand...

How to use Microsoft Dynamics AX 2012 Task Recorder to create a Life Cycle Services Business Process Modeler
Microsoft’s Life Cycle Services is cloud-based workspace that improves the efficiency and collaboration of Microsoft Dynamics AX 2012 implementations. Life...

Escheatment and unclaimed property procedures in Microsoft Dynamics GP
It’s very common for companies in Microsoft Dynamics GP to have open reconciling items on their books for checks that...

Utilizing the Search Form Portlet on Your Home Dashboard
Do you find yourself constantly looking up all transactions related to a specific entity on a daily basis? If so,...

Dashboards Part 2: Using Published Dashboards and KPI Scorecards to Drive Organizational Goals
NetSuite is known for its intuitive layout and flexibility for displaying information, but these features are often not leveraged by...

Dashboards Part 1: Tailoring your NetSuite Dashboard with Custom Reminders and KPI’s
You bought your ERP system on the promise of having one single data source and the numerous and profound insights...
NetSuite Skills Score: A Professional Services Manager’s “Ace in the Hole”
One of my NetSuite clients told me that her key to success at her software company was to always have...

E-Commerce Made Easy With NetSuite SuiteCommerce
It has never been easier to take your business to the next level, by optimizing your omni-channel efforts, with the...

10 scenarios where Microsoft Dynamics CRM is a smarter choice for nonprofits
Let’s face it, there are a plethora of systems designed specifically for nonprofits, whether it is a CRM platform, member...

Setup and process for intercompany trade in Microsoft Dynamics AX 2012 R3
Dynamics AX 2012 R3 allows for the capability to handle intercompany trade transactions. Intercompany trade transactions allow organizations to sell...

Four top Microsoft Dynamics CRM end user training tips
Effective end user training on Microsoft Dynamics CRM is a key factor to a successful implementation. Clients often ask for...

AP and Payment Automation with MineralTree Invoice-to-Pay for Netsuite
Do you find it time consuming to process your AP invoices, expense reports and payments? RSM has partnered with MineralTree...

Important Information About Your Upcoming NetSuite Upgrade
NETSUITE RELEASE 2015.2 As you may have noticed during your last login, NetSuite has announced their 2015.2 release dates. As...

NetSuite Case Study: Packaging Leader in Minneapolis
Many companies that choose to implement NetSuite are growing quickly and like the flexibility of a cloud based, SAAS ERP...

ERP Shout Out — Why Microsoft Dynamics GP is a leading player in the middle market
Already an established leader within the ERP community with well over 47,000 customers, there is a renewed enthusiasm for Microsoft...

Microsoft Dynamics CRM 2015’s new mobile app for smartphones
Two years ago, I wrote a blog about using Microsoft Dynamics CRM 2013 mobile client on tablets, The Future of...

If you know it in Excel, you know it (mostly) in NetSuite Saved Search
Many who work in or with the accounting department have some knowledge in Excel and have probably become comfortable with...

Microsoft Dynamics AX 2012 R3 — Royalty Management
One of the new features in Dynamics AX 2012 R3 is the inclusion of the royalty management module. In order...

Commerce ready ERP system with NetSuite
In today’s online and connected world, all businesses are affected by digital commerce and if you aren’t thinking about its...

When customizations make sense for your ERP project
Often times you will hear that the evil word “customization” come out of every software implementation at great cost and...

Tracking Donor Advised Funds without losing donor data in Microsoft Dynamics CRM
When implementing Microsoft Dynamics CRM for non-profits, one of the biggest pain points I hear from clients about other systems...

Need an Accounts Payable Historical Aged Trial Balance in SmartList or SQL for Microsoft Dynamics GP?
How many times has a Microsoft Dynamics GP client asked for a trial balance report that they can easily see...

Budgeting, Forecasting and Statistical Accounts with NetSuite Advanced Financials
Advanced Financials provides extended functionality to your budgeting and forecasting cycles that is worth exploring. Before considering an external tool...

Improving visibility into your business through NetSuite
With an ever changing business environment, getting timely visibility in to your business operations is really crucial. To be Best-in-Class,...

Wholesale Distribution – Shipping Container Management Solution
NetSuite has done a wonderful job of consistently adding new functionality to support wholesale distributors and manufacturers. But, there is...

How to track emails outside of the Microsoft Dynamics CRM system
In some cases, small features in Microsoft Dynamics CRM mean a lot. I recently learned this while doing a training...
Five considerations for selecting an enterprise resource planning (ERP) system
Identify your key stakeholders and include them throughout the selection process. Embarking on this journey alone can be treacherous. Not...

Maximum Field Length in NetSuite
Have you ever wanted to find a field’s maximum length in NetSuite, but were unable to do so? This could...

Error when opening Workflow Document from email using Microsoft Dynamics GP Web Client
Recently, I was working with one our Colorado clients and ran into an interesting issue. When the user was attempting...

How to configure a Server Side Setup for Email Router in Microsoft Dynamics CRM
In my last blog, The Microsoft Dynamics CRM email router made simple, I talked about the basic concept of the...

Easily Upload Files to NetSuite using File Drag and Drop
Does your company struggle with efficiently uploading and organizing files within NetSuite? Within minutes of setup, your company could easily...
Managing Fixed Assets with NetSuite
Is excel currently being used to manage fixed assets? Why not bring fixed assets into your ERP and let NetSuite...

Tech Support Alert: U.S. Payroll Round 4 tax tables have released – North Dakota
Microsoft announces the following important releases: Dynamics GP U.S. Payroll March 2015 Hot Fix Dynamics GP U.S. Tax Update Round...

Microsoft Dynamics CRM 2015 Update 1: Getting Started with Office 365 Groups
The Dynamics CRM 2015 Spring Update contains a wonderful new preview feature titled Office 365 Groups which will allow for...

Six questions to ask yourself when determining the right time to upgrade your Microsoft Dynamics CRM system
This is a question that our clients often ask us when there is new version of Microsoft Dynamics CRM is...

Microsoft Dynamics GP brings robust ERP solutions to health care organizations
If you are looking for a robust, cost effective ERP solution in the health care industry, you should evaluate Microsoft...

Support Your Global Enterprise – Using NetSuite CSV Import with Japanese Characters
As globally-connected companies move toward NetSuite, the need to display information in multiple languages is increasing in importance. NetSuite natively...

NetSuite SRP Job Costing – Posting Time on Projects
Do you run a services organization in need of a new Project Accounting solution? If so, you’re in luck! NetSuite...

Get rid of spreadsheets and use NetSuite for calculating and paying commissions
Many companies share similar processes for a number of different accounting functions. For example, a standard billing and collections process...

NetSuite Apple iOS and Android Apps Keep Today’s Workforce Mobile
Gone are the days of working 9:00 to 5:00 at the same office Monday through Friday. Today’s work environment is...

How to recreate the data mart in Management Reporter for Microsoft Dynamics
Are you seeing bad or missing data in Management Reporter for Microsoft Dynamics? You may need to recreate your data...

F&B Executive Insights: Microsoft Dynamics AX and Your Existing Microsoft Technology Are a Match Made in Heaven
From razor-thin margins and fluctuating commodity prices to strict demands for regulatory compliance and evolving consumer expectations, the challenges facing...

Executive Insights: Microsoft Dynamics AX for Retail and Native Social Network Integration
Capturing and retaining a core audience is a critical part of staying competitive and profitable across almost every enterprise, but...

Updating full name format on existing Microsoft Dynamics CRM contact records
Recently, a client came to me with the request to change how the Full Name column was displayed in Microsoft...

When and why to upgrade your Microsoft Dynamics GP system
Clients upgrade their Microsoft Dynamics GP system for many reasons. For some, it’s to keep in compliance with payroll taxes...

Microsoft spotlights usage of Microsoft Dynamics CRM for public sector in New Jersey agency
Our client, Camden County Board of Social Services, selected RSM to implement Microsoft Dynamics CRM for its state agency. Camden...

Microsoft Dynamics GP’s Management Reporter Data Mart: what is it and when you’d recreate
If you use Management Reporter, and you have probably heard of the Data Mart. The Data Mart is a way...

Microsoft Dynamics AX 2012 Quick Trick: Generating list of AOT changes utilizing the project filter
Microsoft Dynamics AX 2012 is an incredible piece of software. It allows extreme flexibility for both end users and developers....

C# Development Tips for Microsoft Dynamics CRM
At RSM, we prioritize the use of out of the box features of Microsoft Dynamics CRM to solve business problems....

What does the Microsoft GP 2015 R2 release mean to the Dynamics GP user?
Microsoft Dynamics GP 2015 R2 was just released. So what does that mean to the Dynamics GP user? At a...

When Quick View and Copied Fields should be used in Microsoft Dynamics CRM 2013
The Quick View was introduced in Microsoft Dynamics CRM 2013 and addresses design issues that had existed regarding related entities and...

Microsoft Project integration with Microsoft Dynamics AX 2012 R3
Microsoft Dynamics AX 2012 R2 Cumulative Update 7 includes an out-of-the-box integration to Microsoft Project. This article will show how...

Microsoft Dynamics CRM Outlook Client: How to manage importing too many contacts
The power of having your Microsoft Dynamics CRM system and Outlook closely integrated is well documented, but what happens if...

Microsoft Dynamics CRM 2015 Spring update released — first impression
Microsoft Dynamics CRM 2015 major Spring update has been officially released for Dynamics CRM Online. After experiencing the new changes,...

How to manage automatic client updates in Microsoft Dynamics GP
I recently got asked how IT can manage and deploy the updates for Microsoft Dynamics GP for several client workstations...

The focus on marketing in a CRM implementation
There has been a shift in the conversations we have been having around Microsoft Dynamics CRM. More often than not,...

NetSuite SuiteWorld 2015 recap
NetSuite’s SuiteWorld conference was held in San Jose, Calif., May 4-7. RSM was again a Platinum sponsor for the event...

Executive Series: Unlocking IoT and Omnichannel Retail Insights for Competitive Advantage with Dynamics AX
As the Internet of Things (IoT) continues to explode, connecting all manner of devices with the Internet, consumers are interacting...

What to consider when migrating data to Microsoft Dynamics CRM
When you begin a Microsoft Dynamics CRM Specialists, there is one very important question you need to ask yourself very...

The Microsoft Dynamics CRM email router made simple
One of the things I am frequently asked for help with is the Microsoft Dynamics CRM email router. Whether it’s...

What is Service Based Architecture for Microsoft Dynamics GP
Service Based Architecture is being introduced in Microsoft Dynamics GP 2015, and represents part of a larger paradigm shift for...

Visit RSM at NetSuite’s SuiteWorld conference in San Jose
Next week, May 4-7, 2015 is SuiteWorld, NetSuite’s annual user conference. As NetSuite’s 2014 Worldwide Partner of the Year, RSM...

Feature Spotlight: Microsoft Dynamics CRM Marketing
Over the course of my Microsoft Dynamics CRM career, I’ve worked with versions 4.0, 2011, 2013, and now 2015. In...

Integrating Microsoft Lync to Microsoft Dynamics AX
Over the last few years Microsoft has made significant improvements with its software. One aspect, which has seen tremendous improvement,...
It’s a Small World After All—Why Multi-Site, Multi-Language and Multi-Currency ERP Capabilities Are a Must for Today’s F&B Leaders
As manufacturers look to globalization to expand operations and strengthen strategic partnerships, the F&B supply chain is expanded to include...

Security vs. Control: Airplanes, the Cloud and Office 365
So, I had time to write this on an airplane tonight, and it was fundamentally uncomfortable. It was hot, crowded,...

Microsoft Dynamics CRM 2015 spring release at a glimpse
The Microsoft Dynamics CRM 2015 spring release AKA Vega will launch in Q2 2015 and promises some great new tools...

Using Microsoft Dynamics AX Application Integration Framework (AIF) for high volume integrations
Microsoft Dynamics AX 2012 has a plethora of available integration tools, often leaving implementers confused on what tool should be...

NetSuite Grid Order Entry
NetSuite Grid Order Entry (GOE) can be a huge time saver for distribution companies who fill complex orders with multiple matrix...

What is Microsoft Dynamics CRM’s Service Activity
Microsoft Dynamics CRM has quite a few “out of the box” activities that can be leveraged, i.e. Phone Call, Task,...

Leveraging workflows for consistent salutations and household mailing capabilities in Microsoft Dynamics CRM
Salutations are important data points when it comes to bulk communication with contacts in your database. With the right salutation...

Using Microsoft Dynamics CRM case management in public sector
Lately we have had some interesting Microsoft Dynamics CRM projects in public sector, which highlights the power and versatility of...

How to mask the bank account number in Microsoft Dynamics GP reports such as Direct Deposit Statement in Report Writer
There is a KB article, How to use Report Writer to create a calculated field to mask the bank account...

How to sync Microsoft Dynamics CRM Contacts to your smartphone’s Contacts
I recently had a client in the Real Estate Development market where we implemented Microsoft Dynamics CRM 2015. This was...

Leveraging Microsoft Dynamics AX Personalization — Save, Reset, Load and Retrieve Buttons
Microsoft Dynamics AX Usage Data is quite powerful in a number of ways, one of which is when users want...

Custom ERP Solution Streamlines Operations and Boosts Visibility across Pharmaceutical Supply Chain
While being able to quickly retrieve and consolidate critical data across a variety of business activities is an essential function...

How to create a subreport to calculate a distinct total in Microsoft Dynamics CRM Online using SSRS BIDS Report
When writing reports against data for Microsoft Dynamics CRM Online, I am often faced with limitations of writing dataset queries...

Syncing tasks and calendar reminders from Microsoft Dynamics AX to Microsoft Outlook
While working with a client to propose Microsoft Dynamics AX as a solution to replace a legacy CRM and ERP...

Customer master data upload using Microsoft Dynamics AX Data Import Export Framework (DIXF)
Customer master data is the basic requirement of any ERP master data. When you have to upload large amount of...

Team Foundation Server for Microsoft Dynamics CRM
In Microsoft Dynamics CRM, there is a great tool that is extremely powerful and highly underutilized – Microsoft’s Team Foundation...

Microsoft Dynamics CRM Error: Unable to get property ‘form_onload’ of undefined or null reference
Recently, we were working with a client preparing to upgrade to Microsoft Dynamics CRM 2015 from Dynamics CRM 2013 Spring...

Changing the rollup calculation frequency in Microsoft Dynamics CRM 2015
One of the exciting new features, introduced in Microsoft Dynamics CRM 2015, is the rollup field type. In my colleague’s...

Retrieving purchase order from Microsoft Dynamics AX 2012 using custom built Application Integration Framework (AIF) service
I recently got a call from one of my client who told me that they have an urgent request to...

Retail Executive Insights: Technology that Makes Your Customer-Facing Employees “Chief Empowerment Officers”
Knowledge is power, and today’s consumer has more control than ever before. By simply logging in online or turning on...

Understanding usage of transient fields in Microsoft Dynamics CRM
A transient field is one for which the contents of the field are typically valid only at the point the...

New Advanced Find filter criteria “Under” and “Not Under” in Microsoft Dynamics CRM 2015
Microsoft Dynamics CRM 2015 is shaping to be a much better upgrade than its previous predecessors. Along with some new...

Changing default SmartList options in Microsoft Dynamics GP
I frequently get asked by my Microsoft Dynamics GP clients if they can increase the default SmartList maximum records from...

Microsoft Dynamics CRM Online 2015 Update 1 Announced: What are you excited about?
Microsoft Convergence 2015 has wrapped up in Atlanta and the week was full of news and excitement about the future of...

Connectivity, Commerce, and Retail CFOs: Harnessing Technology to Drive Growth, Part 1
In a world where consumers can both shop without leaving the house and communicate directly with brands with the click...

Connectivity, Commerce, and the Retail CFO: Harnessing Technology to Drive Growth, Part 2
In Part 1 of this blog series, we examined how retail CFOs are leveraging technology, specifically advancements in e-commerce and...

Microsoft Dynamics CRM as the foundation of your digital strategy
Customers are becoming “less loyal” in the traditional sense, so it’s crucial for retailers to provide multiple channels that allow...

How to use Smart Rounding in Microsoft Dynamics AX for customize pricing rules
This blog contains all the information needed to create custom rounding rules when establishing pricing for a company’s items for...

Tips for implementing e-signatures in Microsoft Dynamics CRM
Even though electronic signatures were established in 2000 by the US Federal government’s ESIGN Act, there are still relatively few...

How to set up Microsoft Dynamics AX vendors for 1099 processing
Do you vendors that need 1099s but you are unable to set up them up 1099 processing in Microsoft Dynamics...

Learn how to copy and paste journal entries from Microsoft Excel with new Microsoft Dynamics GP 2013 R2 feature
One of the new feature released in Microsoft Dynamics GP 2013 R2 is the ability to copy and paste journal...

Leveraging NetSuite Sublists for Improved Analytics
NetSuite has long been appreciated by its customers for strong analytical tools such as Dashboard Reports Snapshots, Saved Search Portlets,...

Setting security in report manager for deployment Microsoft Dynamics GP SSRS reports
Part of setting up and deploying Microsoft Dynamics GP SSRS reports is making sure the security is configured. There are...

Subsidiary Navigator OneWorld Dashboard Portlet
Managing multiple subsidiaries in a OneWorld instance of NetSuite may present company and account executives with extra challenges when viewing...
Why data is critical to your ERP implementation success
Very often we hear about the attributes that go into choosing a new ERP system: Will it handle this or...

Microsoft Convergence recap from a Dynamics CRM Perspective – Part 1: opening keynote, Microsoft Dynamics Marketing and unified user experiences
After almost a week at Microsoft Convergence 2015, Microsoft’s premiere event for Microsoft Dynamics users, here are my key take-a-ways...

Microsoft Convergence recap – Part 2: “Microsoft Dynamics CRM Suite”
As a Microsoft Dynamics CRM consultants, there were three topics at Microsoft Convergence that I was most interested, Microsoft Dynamics...

Microsoft Dynamics CRM spring release “Carina” highlights — mmm…CRM.
Microsoft Convergence 2015 just wrapped up in Atlanta. There were many exciting announcements…almost too many to absorb. The pace of...

Creating custom reports in NetSuite
NetSuite offers a number of reports out of the box. In cases where these reports do not meet a specific...

Using Marketing Lists to bypass the limitations of the Advanced Find functionality in Microsoft Dynamics CRM
The Advanced Find feature in Microsoft Dynamics CRM is one of the most powerful tool at the fingertips of end...

Using Microsoft Dynamics AX Data Import Export Framework (DIXF) module to upload vendor data
Uploading large amounts of data into Microsoft Dynamics AX is not always an easy task. For example, when you are...

Calculating a manual or percentage discount in the sales process with Microsoft Dynamics CRM
In the sales process, the ability to find and meet the prospect’s price point is important to winning the deal....

Setting up payroll blended rates in Microsoft Dynamics GP
The standard overtime rate is at least time and a half (1.5) and that is real easy to set up...

No more JavaScript to calculate fields in Microsoft Dynamics CRM 2015
One of the new features in Microsoft Dynamics CRM 2015 is the addition of calculated fields. This is something that...

Solving SQL Server Reporting Services “cannot create connection to data source” error
Have you ever received this error when trying to run a SQL Server Reporting Services report? An error has occurred...

Microsoft Windows 10 – A Paradigm Shift Toward Simplicity & Empowerment
As you may have heard, Microsoft is busy preparing for it next big operating system release, Windows 10. Over one...

What are the hidden costs of excluding user adoption in your Microsoft Dynamics CRM implementation plan?
Over my career I have spoken with a number of CIOs and technical decision makers who make CRM software and...

Understanding the basics of Role Based Security for Microsoft Dynamics AX 2012
Security in Microsoft Dynamics AX 2012 is based on roles where the access is granted to roles and those roles...

How to identify who has Accounts Receivable or Accounts Payable invoice marked in Microsoft Dynamics AX
Have you ever been asked to apply cash to an invoice in Microsoft Dynamics AX through an Accounts Receivable Payment...

Does the Microsoft Dynamics CRM 2011 for Outlook client work with Microsoft Dynamics CRM 2013?
As our clients upgrade their existing Microsoft Dynamics CRM environments to Microsoft Dynamics CRM 2013, one of the more common...

Ensuring Cloud ERP Implementation Effectiveness with NetSuite through Solution Testing
In today’s world, businesses are investing heavily in technology to ensure their business run better. However, this technology only provides...

How professional services function in Microsoft Dynamics CRM
We are more frequently implementing third party packages to open Microsoft Dynamics CRM up to function in professional services organizations...

Taking your ERP implementation from “Good to Great”
I would imagine that a good portion of our readers have read, or at least heard of Jim Collins’ enormous...

Customization of the global search in Microsoft Dynamics CRM 2015
One of the most exciting new features of Microsoft’s latest release of Microsoft Dynamics CRM is the multi-entity quick find...

It’s Tax Season! Automatically Update the NetSuite Sales Tax Tables
Whether adding new summary accounts to the chart of accounts or setting up email alerts, the beginning of a new year...

Clients, good defect and issue reporting “Help Me, Help You” with your Dynamics CRM implementation
When it comes to serving our clients in the Microsoft Dynamics CRM space, or pretty much any software space for...

The benefits of Identity Management in Microsoft Dynamics GP
One of the great new features included in the Microsoft Dynamics GP 2015 release is an improvement to Identity Management....

Microsoft Cloud Platform Roadmap
I have been working with Microsoft for the largest portion of my career; be it as a customer, a partner,...

Customer Service Enhanced by Leveraging Technology in NetSuite
The “Cloud” Everyone has heard about the “Cloud” and how it can save their business. We have all seen the...

Use Data Propagation functionality to map custom fields in Recurring Appointment Entity to Appointment Entity in Microsoft Dynamics CRM
The recurring appointment functionality was introduced in Microsoft Dynamics CRM 2011. It allows users to create many recurrences of an...

How to identify active users in Microsoft Dynamics GP
Identifying active user in Microsoft Dynamics GP is a subject that comes up all the time. If a Dynamics GP...

Role center and dashboard basics in Microsoft Dynamics AX
When someone first sees Microsoft Dynamics AX 2012, one of the most eye catching features is the role center dashboards. ...

Microsoft Dynamics CRM 2015: An upgrade with more conveniences
Microsoft Dynamics CRM 2015 has been officially released for online and on-premises customers. After playing around with the new version,...

NetSuite Saved Searches Part 4: Search Results By Email
We rely on technology now for almost everything, including reminding us to do a task, or alerting us when there...

NetSuite – The ERP System for Deal Makers
As the economy continues to improve, there has been an increased flow of investment capital into the private sector in...

Attach files to notes in Microsoft Dynamics GP and move OLE notes from previous versions
Document attach is available in Dynamics GP 2013, and with each release, it is getting more functionality. The document attach...

Balance sheet formatting in NetSuite
The out-of-the-box balance sheet report tends to raise a frequently asked question by financial reporting managers of NetSuite customers: How...

The benefits of integrating SharePoint with Microsoft Dynamics CRM
As customers begin to really accept and utilize a Microsoft Dynamics CRM system, many clients might find themselves in a...

Using Autodim.exe with Integration Manager to run integrations across multiple companies in Microsoft Dynamics GP
Do you run several integrations with Integrations Manager across multiple companies in Microsoft Dynamics GP? Do you find yourself doing...

How sales managers gain insight into their sales team’s productivity using NetSuite CRM
A much underrated tool in NetSuite that clients quickly skip over with their consultants during implementation is the CRM activities...

Keeping a neat house during custom development — Microsoft Dynamics CRM and “Technical Debt”
In the world of custom development, there is a lot of discussion regarding “technical debt,” a metaphor attributed to Ward...

#1 Tip for year-end close in Microsoft Dynamics GP General Ledger – proper account types
Of course creating a backup before you close the general ledger is very important, but the most common issue that...

What is xRM? Out of the box thinking for Microsoft Dynamics CRM
The technical world is full of acronyms, many of which we lose track of the actual words the letters represent....

Protect business data with Microsoft Azure RMS (Rights Management Services)
Protect your business and don’t make the news for the wrong reasons We’ve all seen the stories about security breaches...

What’s new for Microsoft Dynamics CRM 2015?
In December, Microsoft released the newest edition of Dynamics CRM, which they call Microsoft Dynamics CRM 2015. This is the...

NetSuite Email Alerts – Stay Informed – Be Proactive
NetSuite Email Alerts help you to stay informed throughout the day by emailing the contents of the portlets on your home...

Creating reports for Microsoft Dynamics GP using dynamic queries
Most Microsoft Dynamics GP users love SmartLists and those that have deployed them, love Excel Refreshable (ER) Reports. ER Reports give...

NetSuite Adds Summary Accounts to the Chart of Accounts
With the 2014.2 release NetSuite has added summary accounts to enhance the Chart of Accounts and reporting. Before this release...

How to enable logging in the Connector For Microsoft Dynamics CRM
When running integrations for Microsoft Dynamics CRM 2011 using the Connector for Microsoft Dynamics, you may see error messages in...

Import marketing lists in Microsoft Dynamics CRM with custom import solution
We find ourselves being asked to import marketing lists into Microsoft Dynamics CRM on a regular basis. Customers new to...

Microsoft Dynamics CRM 2015 new functionality: How to do aggregate and calculate rollup data
Microsoft Dynamics CRM 2015 was released for online and on-premise on December 1, 2014, and out-the-box, it has some neat...

The Importance of Training: Part 3 – end-user training and evaluation for Dynamics CRM
Continuing on the topics introduced in my previous article titled “The Importance of a Training Plan: Your Implementation Depends On...

Killer app for dialogs – Extend customer addresses in Microsoft Dynamics CRM without code
The address (AKA customer address) entity is an important entity in Microsoft Dynamics CRM. However, one major frustration is that...

Tips on Creating Custom Forms, Views and Menu Items for Microsoft Dynamics AX
Custom forms, views and menu items can greatly enhance a Microsoft Dynamics AX user’s experience. And once learned, this is...

Open Dialog Process in Microsoft Dynamics CRM 2013 using JavaScript
For those of us who are familiar with calling Dialog process through custom JavaScript in Microsoft Dynamics CRM 2011, you...

Human relationship management (HRM) capabilities in Microsoft Dynamics CRM
How can you turn Microsoft Dynamics CRM 2013 into a human relationship management (HRM) system? By importing a couple different...

Update to the Intercompany Processing function in Microsoft Dynamics GP 2015
With the release of Microsoft Dynamics GP 2015, Microsoft is making an effort to address some of the limitations of...

Tips for improving Scribe performance for Microsoft Dynamics CRM
Our Microsoft Dynamics CRM clients often have a need to integrate their Dynamics CRM environment with other data sources. It may...

Zero in, win faster, sell more — Microsoft’s Sales Productivity Suite give your three products for one great price!
The new age of selling has arrived. Customers increasingly make their buying decisions based on their own research which has forced...

Get me a “SharePoint Type”
There is an old Hollywood joke about the four stages of an actor’s career, with apologies to Mr. Bacon: Who...

Consider a SharePoint and ADFS plan before a Microsoft Dynamics CRM 2013 implementation
Many times when starting a project utilizing Microsoft Dynamics CRM 2013, we talk to customers about any design work for Dynamics...

Understanding the Microsoft Dynamics CRM 2013 versioning strategy
The Microsoft Dynamics CRM 2013 product team is being very intentional with their 2013 software releases. This is due, in...

Creating a Product using the Catch Weight functionality in Microsoft Dynamics AX 2012
The Catch Weight functionality was introduced to Microsoft Dynamics AX with version 2012 and designed for the food and beverage...

NetSuite reports right from your desktop
NetSuite’s web query reports allow you to get report results directly from your desktop without having to go to NetSuite. ...

Microsoft Dynamics CRM and Power BI for everyone — Microsoft Sales Productivity Promotion
Recently, Microsoft launched a Sales Productivity Promotion where the combination of Microsoft Dynamics CRM Online, Office 365 and Power BI...

Modifying Microsoft Dynamics GP SQL reports
SQL Reports provide a great way to access your Microsoft Dynamics GP data without needing to login to Dynamics GP....

NetSuite Android App Availability
A big advantage of NetSuite as an ERP/CRM system is the ability to view and interact with your data from...

Using NetSuite dashboards to optimize your business
In today’s rapidly moving world, businesses need to make decisions quickly in order to remain in a competitive position. Not...

Microsoft Dynamics CRM 2013 Rollup 1 for Service Pack 1 released
Microsoft has released Update Rollup 1 for Service Pack 1 for Microsoft Dynamics CRM 2013. In my previous blog post,...

Codeplex’s SiteMap Editor for Microsoft Dynamics CRM versions 2011 and 2013
I had the opportunity to attend the CRMUG Summit in St. Louis this year and sit in on a session...

Using Teams in Microsoft Dynamics CRM
Recently one of our Denver Microsoft Dynamics CRM clients asked if it was possible to see a comprehensive list of...

Set up CAPTCHA in your online lead forms to protect your NetSuite data from spam
NetSuite’s online forms are a great way to capture new leads, update customer information or even register for events. One...

SharePoint Online with Office 365 vs. SharePoint Server
I’m sure you all have been hearing a lot about Office 365 and SharePoint Online over the past several months...

Microsoft Dynamics CRM 2013 field security profiles explained
One of the great features that Microsoft incorporated into Dynamics CRM 2013 is the ability to lock down certain pieces...

The Importance of Training: Part 2 – train the trainer
Continuing on the topic of training from my last post, The importance of training: Part 1 – the training plan,...

2014.2 NetSuite Tweak – Horizontal Labels
Often Overlooked 2014.2 NetSuite Interface Tweak may Enhance your Users’ Experience I have heard many pros and cons regarding the...

Extending NetSuite – Vendor Center
This posting runs through using SuiteScripts and Suitelets to extend NetSuite functionalities in limited areas. Some Centers such as the Vendor Center, Employee...

Microsoft Dynamics CRM 2013 “Data Encryption Feature Isn’t Activated” error when moving database from online to on-premise environment
We recently migrated a Microsoft Dynamics CRM 2013 online database down to an on-premise environment and stumbled upon an error when...

Track and Apply Landed Costs in NetSuite
Charges that are required to transport and make a stock item ready for sale are referred to as landed costs....

Microsoft Dynamics CRM 2013 errors in Google Chrome
In the course of our daily life, it may not matter very much which browser we use. Sure, colors may...

Comparing Microsoft Dynamics CRM Online versus on-premise deployment
Deployment choices have trade-offs and to make good decisions, organizations need to equate values on the following factors so that...

Recent Email Preference Change in NetSuite’s Purchase Order Approval Routing
NetSuite has very recently changed the default settings for Purchase Order Approval Routing. Your account may be unknowingly sending unapproved...

Sales and use tax for NetSuite: It touches every financial transaction
It is imperative to consider sales and use taxes as part of every NetSuite implementation that involves financial modules. Whether...

Retail Inventory Availability with Proximity for Dynamics AX 2012 R3
Inventory availability views and calculations has gone through quite a few changes over the last few versions of Dynamics AX,...

Microsoft Dynamics CRM Insights: a look at the features
My last two blogs, first covered enabling insights for Microsoft Dynamics CRM Online: Getting the most out of your CRM...

Maintaining an Org Chart within Your NetSuite ERP
Who is Jim’s manager? What is Pam’s title? Who are the resources are on Mike’s development team? For most companies,...

Sway – Microsoft Office 365 New Core Application Introduced
RSM Technology Management Consulting representatives recently attended one of Microsoft’s U.S. stops in their global Office 365 Summit Tour. The...

NetSuite Implementation Best Practices: Do It Now, or Fix It Later
We all know NetSuite implementations and ongoing optimization can be a challenging time for your organization. There are always lots of tasks to...

Using a CRM solution helps demonstrate good customer service
Last year I blogged about going to Disney World on vacation and how the use of a Microsoft Dynamics CRM system...

What the revenue recognition rule changes mean to IT and ERP
Accounting Standards Update (ASU) 2014-09, Revenue from Contracts with Customers (Topic 606), has created quite a stir in the accounting...

Segregating Retail Store Information in Dynamics AX 2012R3 Retail
Overview One of the biggest benefits of using Dynamics AX in a retail environment is the ability to work on...

New Microsoft Dynamics CRM 2013 case routing rules
Microsoft Dynamics CRM uses routing rules in the Case Management Module to automatically direct cases to the right people at...

Batch posting for Microsoft Dynamics GP — Part 3: How to fix batches stuck in posting
Even with all of the preventive measures for stuck batches in place, invariably you still may experience a posting interruption...

Test Scenarios for your NetSuite Implementation
TEST SCENARIOS – Get a complete list of TEST Scenarios for your NetSuite implementation – Use the NetSuite Implementation Bundle...

The importance of training: Part 1 – the training plan
Training at all levels of the organization is critical to the overall success of the implementation. Functionality is no longer...

Accounting for Construction in Progress in Microsoft Dynamics GP Fixed Assets – Part 2
In a previous post, I described the recommended procedures for recording construction in progress (CIP) assets in Microsoft Dynamics GP....

Grow and Streamline Your Wholesale Distribution Business with NetSuite
As a strategy, many wholesale distribution companies are focused on a balance between revenue growth and cost savings. Others are...

eXtremeCRM 2014 and What to Expect for Microsoft Dynamics CRM 2015
After three days of eXtremeCRM 2014, Microsoft has left many high expectations for the future of Microsoft Dynamics CRM. While...

eXtremeCRM 2014: Looking beyond Microsoft Dynamics CRM 2015
At the closing of eXtremeCRM 2014, Microsoft Dynamics CRM group product manager Venkat Sathyamurthy discussed the vision of Microsoft Dynamics CRM...

Microsoft Dynamics CRM — Moving between on-premise and online, and vice versa
We have had a few customers that have decided, for whatever reason, to move from Microsoft Dynamics CRM on-premise to...

Five ways Microsoft Dynamics CRM Insights can help you improve relationships
My last blog, Enabling insights for Microsoft Dynamics CRM Online: Getting the most out of your CRM investment, covered deployment...

Codeplex’s CRM2011 User Settings Utility for Microsoft Dynamics
One of the most common questions I get from customer using Microsoft Dynamics CRM is how do I manage the...
Using Power BI to light up Microsoft Dynamics Business Applications reporting
Power BI, simply stated, is a Microsoft business intelligence platform designed to combine the familiarity of Microsoft Office (with over...

Route for upgrading from older versions of Microsoft Dynamics CRM to Microsoft Dynamics CRM 2013
We have had a number of customers that are looking to move from Microsoft Dynamics CRM 4.0 (3.0 in one...

Batch posting for Microsoft Dynamics GP — Part 1: Batch posting vs. transaction level posting and batch edit lists
Although Microsoft Dynamics GP allows individual transaction level posting, we recommend using batch posting whenever possible. Batch posting allows you...

Batch posting for Microsoft Dynamics GP — Part 2: Cause and prevention for stuck batches
Transactional errors are not the only reason for a batch to be interrupted and fail during posting in Microsoft Dynamics...

Microsoft Dynamics CRM 2011 SQL server error while deleting solution
I attempted to delete a managed solution in my test environment of Microsoft Dynamics CRM and halfway through the process,...

Do I need to upgrade my Microsoft Dynamics CRM 2011 for Outlook client to use Dynamics CRM 2013?
As our clients upgrade their existing CRM environments to Microsoft Dynamics CRM 2013, one of the more common questions I...

Using Revenue Recognition Schedules in NetSuite
NetSuite has many great features, some of which slip under the radar and are underused. One such feature is Revenue...

Enabling insights for Microsoft Dynamics CRM Online: Getting the most out of your CRM investment.
The most successful sales, marketing and customer service organizations effectively manage their relationships in order to better serve their customers....

Adding additional user fields to a Microsoft Dynamics SL screen
All too often, Microsoft Dynamics SL clients run out of user fields when looking to maintain additional information. This shortage...

Managing Intercompany Expenses with NetSuite OneWorld
NetSuite OneWorld is a great tool for multi-subsidiary companies looking to manage all subsidiaries through one instance of NetSuite. Compared...

Microsoft Dynamics CRM 2013 data imports limitations
We get a lot of questions as far as data imports and more specifically updating. Microsoft Dynamics CRM 2013, just...

How to record Construction in Progress (CIP) in Dynamics GP Fixed Assets
Clients frequently want to understand the options for tracking construction in progress (CIP) assets in Microsoft Dynamics GP. CIP assets...

Subscription and contract invoicing solutions in Microsoft Dynamics AX
In the world of products and services, for the consumer and business, the concept of invoice and payment is simple:...

NetSuite user group webcast – Exploring the 2014.2 release
We’re all excited about the upcoming 2014.2 release of NetSuite. There’s some key things that you need to be aware...

Standard Costing Management and Reporting Simplified with NetSuite and Saved Searches
Managing inventory cost is important to a company’s growth and success. NetSuite offers multiple costing methods for valuing inventory and...

NetSuite Mobile for iPhone
Mobility and productivity have become a popular topic in today’s business world. NetSuite provides a solution to your business mobility...

Using the Dynamics AX Collection Classes
The Microsoft Dynamics AX collection classes provide simple data structure implementation to allow developers to store and access simple types...

Microsoft Dynamics AX helps thriving manufacturing companies manage growth in supply chain
According to the 2014 RSM Manufacturing & Distribution Monitor report, thriving manufacturers and distribution companies show similar patterns in investment,...

Leveraging KPI Scorecards in NetSuite
Many people use the terms “dashboard” and “scorecard” interchangeably, but there is a significant difference between them. A scorecard is...

Preparing for NetSuite’s New Release 2014.2
NetSuite’s newest release 2014.2 is expected to be a major release in terms of how the application looks and functions....

Software companies use NetSuite to get a 360 degree view of their customers
Technology companies are familiar with the concept of system requirements but often the internal systems found at a technology company...

Business rules in Microsoft Dynamics CRM 2013 are missing one key feature
I have read many of the blogs written by my colleagues about the great new features of Microsoft Dynamics CRM....

Getting ready for budgeting season with the latest budgeting tools
It’s getting close to budgeting time and you may be thinking there has to be another way other than Excel...

Top 5 updates from the NetSuite 2014.2 release
NetSuite’s upcoming 2014.2 update has a lot of improvements across many areas. Your favorites will depend on what portions of...

Update Rollup 3 for Microsoft Dynamics CRM 2013 released: install or not to install?
With each new Update Rollup of Microsoft Dynamics CRM 2013 being released, you have to think carefully if it is worth...

How to know when to look at a new ERP system
Many companies have turned to RSM over the years to help them evaluate the selection of an Enterprise Resource Planning...

Using StickyNotes in NetSuite to Inform Your Users
Tired of using notepads, bookmarks and sticky notes to keep track of unique information? Start tracking that information in NetSuite!...

The phase out of Business Portal — What now?
There are a significant number of Microsoft Dynamics GP users who have used the Business Portal application for entering things...

Pros and cons of Microsoft Dynamics GP 2013 Roll Down Segment Changes feature
Roll Down Segment Changes is a new feature added to Microsoft Dynamics GP 2013 that allows users to make a...
White Paper: Extending CRM: Utilizing xRM to expand your relationships
The term xRM, where “x” is an algebraic variable that represents any business relationship you want to manage, is used...

Hiding a section and fields in Microsoft Dynamics CRM 2013 using Business Rules
Business Rules within Microsoft Dynamics CRM 2013 allows users to add functionality to the system that in previous versions of Dynamics CRM...

Microsoft Tools That Help: Creating Consistent UI with the Dynamics AX Form Checker
Creating Consistent UI with Dynamics AX Form Checker “To do the job right you need the right tools” is the...

Tech Article: Configuring Balance Sheet Templates in Microsoft Dynamics AX 2012
Configuring Balance Sheet Templates in Microsoft Dynamics AX 2012 Management Reporter 2012® incorporates many new features such as interactive report...

Why Business Rules are the biggest change to Microsoft Dynamics CRM 2013
In Microsoft Dynamics CRM 4.0 and Microsoft Dynamics CRM 2011, if you wanted any type of automation on your record...

Microsoft Tools that Help: How to Create an Entity Relationship Diagram
“To Do the Job Right You Need the Right Tools!” The slogan of a favorite blog site of mine, Microsoft...

Formatting date and time fields in a mail merge for Microsoft Dynamics CRM 2013
The mail merge feature in Microsoft Dynamics CRM 2013 allows users to automatically add the names, addresses, and other information...

Microsoft Dynamics CRM 2013 Issue Assistance: “Are you sure you want to leave the page?” pop-up on Save
During the previous few months of working with Microsoft Dynamics CRM 2013, there is one issue I’ve seen time and...

Dashboard Security in Microsoft Dynamics CRM 2013
Microsoft Dynamics CRM 2013 has brought us many new functionalities and features such as new user interface (UI) model, business...

Integrating Microsoft Dynamics CRM with Bing Maps REST Services
A new feature of Microsoft Dynamics CRM 2013 is the out-of-the-box Bing Maps integration. It provides the user with a...

RSM Named Worldwide Partner of the Year for Second Consecutive Year
For the second straight year, RSM was the recipient of the Worldwide Partner of the Year award. The announcement was...

Ahead of the Game: H-E-B’s Early Adoption of Enterprise Technology Means Competitive Advantage in Today’s Marketplace
The food manufacturing industry faces many challenges, from consumer demands, operational inefficiencies to governmental regulations. For many companies, adopting enterprise-wide...

Configuring Workflow for Microsoft Dynamics AX 2012
Introduction In the first article Simplifying Workflow, we reviewed the steps for running the workflow infrastructure configuration wizard, creating a...

Simplifying Workflows for Microsoft Dynamics AX 2012
Introduction The workflow process is vastly expanded in Microsoft Dynamics® AX2012. The built in new capabilities of line item approval,...

Microsoft Dynamics CRM 2013 Opportunity Error Fix: Object doesn’t support property or method ‘Form_onload’
While recently working with a Microsoft Dynamics CRM 2013 online environment, an error appeared on the Opportunity form. “There was...

Sub-grid Auto Reload Limit has Changed in Microsoft Dynamics CRM 2013
Those that worked with Microsoft Dynamics CRM 2011 know you can insert more than four sub-grids on a form. However, only the...

Family of NetSuite services is NOT vulnerable to Heartbleed; TribeHR patched on 4/8/14
The Heartbleed vulnerability represents a significant threat to security on many websites. However, the NetSuite service is not vulnerable to...

Microsoft Dynamics GP 2013 Progress Bar Issues
Microsoft Dynamics GP 2013 includes a new progress bar feature on the Depreciate Routine, but it is a bit touchy. ...

Setting up Mailboxes in Microsoft Dynamics CRM 2013 for Online Clients
In Microsoft Dynamics CRM 2013 Online, there are a great deal of changes to how Microsoft Dynamics CRM will manage e-mails...

Scribe Fails to Connect to Microsoft Dynamics CRM 2013
We had this happen to one of our clients as a result of the Microsoft moving them from the LiveId...

Microsoft Dynamics CRM 2013 Mobile Client and JavaScript: Do they play nice together?
As with most Microsoft Dynamics CRM implementations, there tends to be an abundance of JavaScript that accumulates on the forms...

Internet Explorer 11 and Windows 8.1 support added for Dynamics CRM 2013
We’ve received many calls from users of Dynamics CRM 2013 that have been struggling with compatibility issues when using Internet...

A Faster Way to Create Records in Microsoft Dynamics CRM 2013
For many of us who have used Microsoft Dynamics CRM 4.0 or Microsoft Dynamics CRM 2011, you will notice that creating...

Restoring the Email Configuration option in the Microsoft Dynamics CRM 2013 Settings Area
It seems that with organizations that were migrated from Microsoft Dynamics CRM 2011 to Microsoft Dynamics CRM 2013, the Email...

Retail Database Sizing Using SQL Express
AX2012 R2: Retail POS Database Sizing From time to time I am asked what version of SQL Server the client...

Selecting Hardware for Microsoft Dynamics AX for Retail
How to Select Hardware for Microsoft Dynamics AX for Retail? Clients Ask: “Which Should I Buy? Can I Use...
11 Reasons Why CRM Implementations Fail
For many companies, CRM is all about acquiring new customers, keeping your existing customers, increasing sales to existing customers and...

The Whirlwind of Microsoft Dynamics Convergence Comes to an End
What a week! The week of Microsoft Dynamics Convergence was filled with so much information to gather, absorb, retain and disseminate....

Microsoft Dynamics Convergence has officially begun!
Day two of Microsoft Dynamics Convergence started with a great drum line from Spirit of Atlanta Drum & Bugle Corps, as...

First Taste of Convergence: CRMUG PreGAME 2014
I was told that Monday would be the PreGame for Microsoft Dynamics Convergence, which officially begins tomorrow, so I figured it would be a light...

Quick Date Selector in NetSuite
A nice feature in NetSuite is being able to create useful dashboards. The dashboard allows you to be able to...

Working with Business Process Flows in Microsoft Dynamics CRM 2013
One of the exciting new features of Microsoft Dynamics CRM 2013 is Business Process Flows. This feature provides many benefits including:...

Migrating root business unit using Connector for Microsoft Dynamics
We recently assisted a client who decided to migrate their Microsoft Dynamics CRM 2011 on-premise implementation to Microsoft Dynamics CRM...

Why can’t I change my personal settings in Microsoft Dynamics CRM 2013? A simple fix to a big personal problem.
In Microsoft Dynamics CRM 2013, there are a significant amount of nuances and changes for personal settings that have caused...

Common HTML codes to format NetSuite Saved Searches
NetSuite allows users to manipulate the output of Saved Searches. Basic HTML codes can be added to a NetSuite saved search...

Export Limitation from Microsoft Dynamics CRM to Microsoft Excel
The 10,000 records export limitation from Microsoft Dynamics CRM to Microsoft Excel is certainly a hurdle for a lot of...

Microsoft Dynamics CRM 2011 “Access is denied” error resolved
Many of us who have implemented Microsoft Dynamics CRM or wrote Jscript Odata from the SDK will sometime stumbled upon an...

Reconciling Customer Credit Card Payments in NetSuite with Merchant e-Solutions
NetSuite offers the ability to process credit card transactions instantly over the internet by integrating with different payment gateways. These...

Clearing Microsoft Dynamics CRM Common Script Error
Many companies that use Microsoft Dynamics CRM, use it along with the Microsoft Outlook plug-in. This offers the ability to track...

Solving Microsoft Dynamics GP’s Unable to Enter Invoice against PO Receipt Issue
I recently had a repeat support request. That is, same issue but from a different client. So, I thought I...

Five ways to jump start your Microsoft Dynamics ERP system
Many users have been working with their ERP system for five or ten years and paying the enhancement each year. ...

Update Rollup 16 for Microsoft Dynamics CRM 2011 is available
Microsoft has released Update Rollup 16 for Microsoft Dynamics CRM 2011 for on-premises customers. Update Rollup 16 contains over 150...

NetSuite sensible saved searches – Part 3: Highlighting and filters
In the non-virtual world when an items needs emphasis or a flag to remind, we often use markers such as...

Microsoft Dynamics CRM 2011 to 2013: Changing Your Outlook Client
This is a step-by-step guide to uninstalling Microsoft Dynamics CRM 2011 for Outlook from your computer, and installing Microsoft Dynamics...

Microsoft Dynamics CRM 2013 Update Rollup 1 is Released
For many of us who upgraded to Microsoft Dynamics CRM 2013 or have used since it was released, you will...

White paper: Spend visibility and shared services, strategies to address growing pains for long-term care organizations
In a recent white paper, Spend visibility and shared services, strategies to address growing pains for long-term care organizations, RSM...

Important message for Dynamics GP users who need to print 1099s
We are starting to get a lot of calls from customers who are getting ready to print their 1099s. For...

Issues and options for running Microsoft Dynamics CRM versions 2011 and 2013 in Windows 8.1
With the release of Windows 8.1, many businesses that have been running Windows 8 are upgrading so they can get...

How Data Mart in Management Reporter 2012 helps Analytical Accounting
If you are using Analytical Accounting (AA) in Microsoft Dynamics GP, there are benefits from implementing the Data Mart in...
O365 SharePoint 2013 Folder Creation Code Using the Client Object Model
A lot of organizations today are taking advantage of Microsoft Dynamic CRM’s integration into SharePoint because SharePoint is by far...

Interpreting a Microsoft Dynamics CRM 2011 custom report parse error
A client recently received the following error after uploading a custom report to Microsoft Dynamics CRM 2011 and trying to...

Tips for importing emails into Microsoft Dynamics CRM
I recently had to import a series of email records into Microsoft Dynamics CRM which became a little more challenging...

Understanding the different options for tracking E-mails in Microsoft Dynamics CRM
The power of Microsoft Dynamics CRM as far as tracking emails is great. It is also a little overwhelming. I...
How a CRM system can make you look foolish
I recently ran across a situation where utilizing a CRM helped to make a company look foolish. I was getting...

Pros and Cons of Repurposing a Microsoft Dynamics CRM Native Entity
With Microsoft Dynamics CRM’s ability to easily configure and customize a system to fit any business process, questions frequently arise...

Microsoft Dynamics CRM 2011 JavaScript OnChange of Checkbox Field —Now Instant!
For us Microsoft Dynamics CRM consultants or developers who has ever written JScript codes for on-click of checkbox field for...

How to backup your Microsoft Dynamics CRM Online or Salesforce.com database for local use
With many clients moving to the cloud, there are still some concern about who owns the data and how the client...

Replacing a Field Label in Microsoft Dynamics CRM with an HTML Web Resource
When configuring forms within Microsoft Dynamics CRM, a form’s field label has a 100 character maximum. In certain instances, 100...

How to set up Microsoft Dynamics CRM 2013 for mobile tablets
Microsoft has definitely improved the functionalities of running Microsoft Dynamics CRM on tablets in their latest version, Microsoft Dynamics CRM...

How to create dashboard pie charts in Microsoft Dynamics CRM 2011 with hyperlinked detail views
A client recently asked us for a pie chart report illustrating the breakdown of account types, and hyperlinked to a...

How to populate a text attribute with checkbox labels values in Microsoft Dynamics CRM
In the past we’ve been asked to present an attribute on a form in Microsoft Dynamics CRM that will provide a concatenated...

Microsoft Dynamics CRM 2011 to 2013 Upgrade — Custom Ribbon Button Issue
Our client recently went through an upgrade from Microsoft Dyanmics CRM 2011 Online to Microsoft Dynamics CRM 2013 Online and I noticed some...

Finding related NetSuite transactions for advanced searches
In NetSuite, all transactions from sales orders to invoice and purchase orders to bills are related. Finding the right records...

Microsoft Has Been Listening! New Customizations Functionality in Dynamics CRM 2013
Lately, I’ve found it increasingly rare that I take the time to read the instruction manual before jumping into something...

Fixing Microsoft Dynamics CRM’s Outlook Plug-in Installation Authentication Issues
Recently, when installing the Outlook plug-in for Microsoft Dynamics CRM, we have been running into authentication issues when using the...

Full Micrsoft Dynamics CRM 2011 functionality for iPad using Safari
A few months ago, this blog detailed the steps for users to gain Full Microsoft Dynamics CRM 2011 functionalities for...

Reasons to Migrate to Microsoft Exchange 2013
Today there is a lot of buzz around Cloud and when it comes to communications and collaborations, Office 365 is...

Prevent unwanted Microsoft Dynamics CRM 2011 contacts syncing down to outlook
From my past implementations of Microsoft Dynamics CRM 2011 for Outlook, the scenario of having unwanted CRM Contacts synced down...

Understanding when to develop business processes for Microsoft Dynamics CRM Connections
With the introduction of Microsoft Dynamics CRM 2011, one of the new features was the Connection entity. The purpose of...

Understanding Chart XML in Microsoft Dynamics CRM
With all of the data being stored in your CRM system, it’s important that information managers and executives are seeing it...

How to configure Microsoft Dynamics CRM 2011 deep linking for mobile browsers
Have you ever created a workflow to send an email with a link to the record? If you’re in the...
Cloud platform considerations when choosing an Cloud ERP solution
In very simple terms, Cloud Computing or in this case, Cloud ERP provides your organization with an ERP solution and...

New licensing options for Microsoft Dynamics CRM 2013
At the Orion Partner Blitz Training, Microsoft announced three new licensing level options for Microsoft Dynamics CRM Online 2013. This...

Microsoft Dynamics GP 2013 Service Pack 2 installation error
When attempting to install the Microsoft Dynamics GP 2013 Service Pack 2 (12.00.1482), I received a message stating “The path...

Using Microsoft Dynamics GP 2013 tenant functionality
Microsoft Dynamics GP 2013 now comes with tenant functionality. This enhancement lets you have more than one instance of Dynamics GP...

Microsoft Dynamics CRM 2011 vs. Microsoft Dynamics CRM 2013
With all the hype and boom around the new version of Microsoft Dynamics CRM 2013 release, let’s take a look...

Microsoft Dynamics CRM 2011: JavaScript to calculate a percentage discount on the Quote Product
In Microsoft Dynamics CRM 2011, have you ever needed to apply a discount to a single product on a Quote...

Best Practices in Training: The Key to a Successful ERP Implementation – Part 3
This third and final installment of the three-part blog series, “Best Practices in Training: The Key to a Successful ERP...

Best Practices in Training: The Key to a Successful ERP Implementation – Part 2
This second installment of the three-part blog series, “Best Practices in Training: The Key to a Successful ERP Implementation,” will...

Best Practices in Training: The Key to a Successful ERP Implementation – Part 1
After selecting the right ERP system, the next major challenge for an enterprise is in the implementation, where success is...

Microsoft Office 365: Enterprise Plans Explained
One major advantage of a product offering like Microsoft Office 365 is being able to mix and match Enterprise Plans. ...

Issue with ActivityFeeds.Plugin.ActivityClose interfering with the creation of records
We’ve seen some strange issues at several Microsoft Dynamics CRM 2011 deployments where the ActivityFeeds.Plugins.ActivityClose plugin gets registered as a...

Loading a Merchandising Hierarchy with No Programming!
If you are like me, you probably are getting tired of creating hierarchy loaders to setup Retail systems. The good...

Custom Fields with Values Derived from Saved Search Results
With Release 2013.2, NetSuite introduced a powerful new way to calculate the value of a custom field. With the new...

NetSuite Saved Search Tutorial
NetSuite’s Saved Searches allow users to develop reusable custom reports that link directly to business information whether it be sales,...

Microsoft Dynamics AX 2012 Upgrade Tips
As featured in the “Fall 2013 AXUG Magazine”, below is a small sample of some of the high-level recommendations from...

NetSuite Electronic Payments Bundle: Using Electronic Payments
Remember those days when you received your wages in check as an employee, deposited the check in the bank and...

Checking if a user is a member of a Team (by team name) using JavaScript
Occasionally we need to conditionally take an action programmatically on a form such as hiding fields, etc. based on a...

Business process enhancements in Microsoft Dynamics CRM 2013
With the introduction of Microsoft Dynamics CRM 2013, there are many improvements and enhancements but one of the areas I...

STOP: Yammer Time! — Microsoft’s Next Social Revolution
“It’s dead,” Jive CEO Tony Zingale stated when asked about Yammer during a panel discussion at Fortune Brainstorm Tech. A...

How to set up Microsoft Dynamics GP Payroll deductions for union dues calculations
The formulas used to calculate union dues are often complicated, non standard deductions that require special treatment in Microsoft Dynamics...
Attend RSM’s 2013 Microsoft Dynamics Summits
This fall, RSM will hold its fourth annual Microsoft Dynamics™ Summit events in an expanded footprint. The cities include Malvern,...

Creating Date Sensitive Functionality for not-for-profit organizations in Microsoft Dynamics CRM
We recently had a client in state and local government industry that required records to be activated and deactivated depending...

Business Rules in Microsoft Dynamics CRM 2013
Attending the CRM 2013 partner blitz a few weeks ago certainly got me very excited about some of the new developments and investments...

Microsoft Dynamics CRM error: The issuer of the security token was not recognized by the IssuerNameRegistry – Solved
“The issuer of the security token was not recognized by the IssuerNameRegistry. To accept security tokens from this issuer, configure...
Microsoft Collaboration Technology Supports Refresh Success
I am pleased to have presented my first RSM webinar with Microsoft. It’s on a set of topics near and...

Microsoft Office 365 – Enterprise Features for Any Size Business
The cloud is one of the hottest buzzwords in business today. I can summarize the mission statement of Microsoft® Office...

A new version of Microsoft Dynamics CRM is coming out, why implement now.
A new version is coming out, why implement now? With the onset of Microsoft Dynamics CRM 2013, which was just...

In Microsoft Dynamics CRM 2011, cannot add new phone call or task on contact form – Solved!
A client had been experiencing an issue while using the Polaris forms in Microsoft Dynamics CRM 2011. The client had...

NetSuite sensible saved searches — Part 2: Grouping and summarizing
Most commercial systems have the ability to extract valuable data from your ERP/CRM databases through reports and exports to spreadsheets...

Take CRM beyond sales management to personalized service
I am flying home from vacation to my family’s favorite destination, Disney World. I took note on this trip to...

When to use Scribe vs building data intergration or migration
I recently had a customer that is implementing Microsoft Dynamics CRM 2011. They were asking why we were recommending using...

Intercompany Processing in Microsoft Dynamics GP
Microsoft Dynamics GP is aimed at the middle market and organizations in that space are often comprised of multiple legal...

Microsoft Dynamics CRM And Microsoft Outlook – What’s under the covers?
A few months ago, we were tasked to re-deploy Microsoft Dynamics CRM 2011 for one of our clients. The servers...

“Click to Call” the New Microsoft Dynamics CRM 2013 Phone Feature
Microsoft Dynamics CRM is only getting better! The new phone feature will enhance the user’s communication experience by simply clicking...

Leveraging Microsoft Dynamics AX 2012 Advanced Rules in Account Structures
The flexibility of creating Account Structures (AS) with any number of Financial Dimension (FD) nodes is extremely beneficial when building...

Understanding Table Relations in Dynamics AX 2012
In Dynamics AX implementation, sometimes you need to know the table relations for one reason or the other. For example,...

Complimentary webcast: Overview of NetSuite’s version 2013.2 key enhancements
NetSuite released updates to their product this summer. Join us on Wednesday, August 28th to learn about some featured enhancements...

Microsoft Dynamics CRM 2013 User Interface: Easier, quicker, more functional and more tailored to the way you work
“Our dilemma is that we hate change and love it at the same time; what we really want is for...

The Microsoft Dynamics CRM 2013 image attribute type – major or meh?
One of the new enhancements in Microsoft Dynamics CRM 2013 is the ability to add an image to any record...

Conditional Batch Jobs
Batch jobs are a convenient way to process resource-heavy tasks without locking up a client session. Most batch jobs are...

The Future of Mobile Client in Microsoft Dynamics CRM 2013
After attending a Partners only session of the upcoming new Microsoft Dynamics CRM 2013, I found one prominent feature which...

Microsoft Dynamics CRM 2013 Entity Table Merge for SQL Server
As a partner organization we have the opportunity to get some early sneak-peeks into what’s coming down the pipeline with...

Microsoft Dynamics CRM 2013: A first look
Microsoft recently hosted a webinar to introduce us to Microsoft Dynamics CRM 2013, originally called Orion. The presentation and product...

Using an Agile Hybrid approach to the implementation of Microsoft Dynamics CRM
We have good success implementing Microsoft Dynamics CRM utilizing a project methodology based on the Agile method. The Agile approach...

ERP Implementation: Top 10 Critical Success Factors (Part IV)
Part four of this blog series examines the final three critical success factors: targeted data migration strategy, thorough system testing,...

Data ownership and accountability: Who is responsible in your CRM system?
Time and time again, we continue to see the internal business process struggles of data ownership. The question becomes ‘Who...
Microsoft Office 365 – Business Drivers for SMB’s to Take the Cloud Plunge
Cloud computing continues to be more affordable and accessible than ever before and is becoming the great equalizer for SMB’s...

How to upgrade to Dynamics CRM 2011 by creating entities from customized in Dynamics CRM 4.0
Recently I ran into an issue with a solution import failure for a customer that was trying to move a...

Microsoft Dynamics CRM 2011 Cannot Open Mail Merge From Web Client – Solved
Most marketers depend on the Microsoft Word’s mail merge function to speed up the process of creating letters, labels and...

ERP Implementation: Top 10 Critical Success Factors (Part III)
Part three of this blog series examines the next critical success factors: approved solution design, user/SME participation and engagement, process...

White paper – Transitioning to Microsoft Dynamics AX: Evaluating data migration solutions
As many Microsoft Dynamics GP users evaluate their ERP systems needs, they no doubt look within the Microsoft Dynamics suite...

Tracking large opportunities as a parent to smaller future opportunities
We have had a few clients over the past several years using Microsoft Dynamics CRM that have struggled trying to...

Dynamics CRM 2011 Update Rollup 14 is now available.
Update Rollup 14 for Dynamics CRM 2011 (UR14) is now available. It is primarily a break/fix release squashing several Outlook...
ERP Implementation: Top 10 Critical Success Factors (Part 2)
In this second installment of the Top 10 Critical Success Factors, this blog will examine the first three success factors...

Microsoft Dynamics GP SmartList Export Solutions Save You Time in Excel
Are you utilizing SmartList for Microsoft Dynamics GP to its fullest extent? You know about exporting to Excel for data lists...

Magic Way to Increase Speed with Microsoft Dynamics GP SmartList Export
Many of us rely on SmartList queries to get financial data out of Microsoft Dynamics GP and into our favorite...

Data ownership: who really owns your data in a CRM deployment
We have heard a lot of concerns about data ownership at new client sights. These concerns are not whether the...

ERP Implementation: Top 10 Critical Success Factors-Part One
For many companies, the long and sometimes tedious process of selecting an ERP system is considered easy compared to...

What’s new and what you need to know before upgrading to Microsoft Dynamics CRM 2013 (“Orion”)
“If I had asked people what they wanted, they would have said faster horses.” While there is some debate about...

4 Quick Ways to Enhance Your ERP Solution
Here are a few suggestions for extending your investment with your current ERP solution without having to endure complex implementations....

Illuminating Discrete Subcontracting for Microsoft Dynamics AX 2012
The discrete subcontracting process for Microsoft Dynamics® AX 2012 uses the standard bill of materials (BOM) approach to create an...

Is your CRM system a “Big Brother?”
I typically walk into meetings when Microsoft Dynamics CRM is getting introduced to the end users and a comment is...

3 Tools to Improve Performance Testing in Microsoft Dynamics AX 2012
When it comes to implementing an ERP solution, in my experience, there is an absolutely critical area that is...

CRM Implementation Success Factor: User Acceptance Starts at the Beginning
Sometimes the hardest challenge in switching systems is not the data migration or translating business requirements, it is the adoption...

Pharmaceutical Manufacturer Describes Experience Working with Microsoft Dynamics AX
Osmotica Pharmaceutical is a global specialty pharmaceutical company, headquartered in the United States. In 1986, they begun operations as the Research &...

Using Microsoft Excel as a Data Entry Tool for Microsoft Dynamics CRM
Suppose the business sales representative of a company are on the road and traveling for 12 hours. On the road, their internet...

Demystifying LEAN Subcontracting Implementation for Microsoft Dynamics AX 2012- Part Two
Imagine the subcontracting process for Microsoft Dynamics® AX 2012 resembles a large body of water in which you need to...

Creating a Custom Interactive Grid on a Microsoft Dynamics CRM Entity Form using SSRS
There are many resources documented in how to create a report to appear in a CRM form such as: http://andreaswijayablog.blogspot.com/2011/08/crm-2011-embed-report-in-iframe-and.html...

Don’t Hope for Project Success. Plan for It.
Implementing a new ERP system can seem like a daunting task at the beginning, but if certain guidelines are followed...

Options for Microsoft Dynamics GP 2013 Cloud Deployment
As cloud computing for ERP heats up, Microsoft Dynamics GP 2013 is finally starting to respond. Many of us have...

Configuring the Real Time Web Service 6.1 for Microsoft R2 Point of Sale
Here is a quick walkthrough of how to configure the Real Time Web Service 6.1 in R2. This document assumes...

Kicking the Cloud ERP Tires? Here’s What You Need to Know.
You are probably seeing a lot of “we’re in the Cloud and we’re cool so use us” advertising and wondering...

RSM Named as NetSuite’s Worldwide Partner and Americas Solution Provider Partner of the Year
The announcement that RSM was awarded Worldwide Partner and Americas Solution Provider Partner of the Year was made in San...

What’s New in Microsoft Dynamics GP 2013 for Distributors
Distributors and direct sales organizations will benefit from a new feature in Microsoft Dynamics GP 2013 Sales Order Processing. Suggested...

Expanding Microsoft Dynamics CRM Mobile Experience with Photo Capture on iPad
As a Microsoft Dynamics CRM consultant, I always wish we could have the whole Dynamics CRM web browser experience on...

Making a Number Sequence Shared in AX 2012
Note: the instructions to make the following change will make a number sequence shared across ALL companies. This does not allow you...

Cloud ERP Doesn’t Break the Bank
Even with the improvement in the economy, many companies are still very cost-conscious so adding a new technology like cloud ERP...

Video: Microsoft Dynamics ERP and CRM Connector
This 9 minute video demonstrates a common scenario for the Dynamics CRM Connector for Dynamics GP. I demonstrate the qualification of...

Microsoft Dynamics AX 2012 for Retail – Good Stuff Right out of the Box!
Whew! That Microsoft Dynamics AX 2009 retail project is finally finished! The store is open, and after a few hundred modifications,...
Before You Abandon Your ERP System, Consider Optimizing
Let’s face it, the demands of an implementation project along with the pressures of their “day jobs” mean that most...

Reporting Access for Everyone with Microsoft Dynamics GP
I help many of my clients evaluate Microsoft Dynamics GP, and one area that is extremely important in their eyes...

Examining X++ Query Statements for Microsoft Dynamics AX 2012
The query statement in X++ is a primary method of retrieving and manipulating data in Microsoft Dynamics AX 2012. A...

Empowering Data Manipulation for Microsoft Dynamics AX 2012
Data manipulation in Microsoft Dynamics AX2012 empowers the developer with the tools to view, insert, update, and delete data elements...
Mid Market Companies Soar to the ERP Cloud with Success
For mid-market companies, the process of selecting and implementing a new cloud-based ERP system like NetSuite, may be difficult to navigate on their...

Full Microsoft Dynamics CRM 2011 functionalities for mobile devices without third-party solutions
As many of you are aware, running Microsoft Dynamics CRM 2011 on mobile device does not offer you the full...

Exploring X++ Control Statements for Microsoft Dynamics AX 2012
Programming control statements are the source of many operations within Microsoft Dynamics AX 2012. This article explores four of the...

Managing the Microsoft Dynamics AX for Retail Whirlwind – Effective end-user training
Ask anyone who has been involved in a retail store opening and they will attest to to the ever-increasing cyclone...

Why Should You Put Your Microsoft Dynamics GP system in the Cloud?
Working with Microsoft Dynamics GP for the past 14 years has allowed me to witness the evolution of many information...

Navigation Tips for New NetSuite Users
Even for the most tech savy people, migrating to a new a software system and learning to navigate it is...

DataAreaId and Partition and Very Slow Queries
Forgetting to add DataAreaId in a SQL query is an issue I see a lot while resolving performance issues for...

Overview of Instant Configurability of NetSuite (aka SuiteBuilder)
The instant configuration Netsuite gives is an advantage in the ERP and CRM market. Netsuite offers the point-and-click functionality through their SuiteBuilder...

Top 4 People Related Pitfalls to a Successful ERP Implementation
It is easy to understand why people would consider an ERP implementation as an “IT Project” or “computer issue”. After...

Hosting provider implements Microsoft Dynamics GP for process integration and significant savings
This Colorado-based company provides cloud hosting and recovery solutions to a global customer base. They inherited Microsoft Dynamics GP after a acquisition...

Spring is the Perfect Time to Migrate from FRx to Management Reporter
Now is the perfect time to migrate your FRx reports to Management Reporter (MR). You have made the decision to...

Creating Pivot Table Forms and Reports in AX
Many times in AX, users would like to manage their items in a matrix or dimensional grid. I’ve used this technique...

The Rapid Innovation of the SaaS NetSuite model
One of the benefits of a SaaS system, such as NetSuite, is the continuous stream of new features. NetSuite provides...

Dynamics AX 2012 Trace Parser Setup
If possible, run the long running process in a testing/performance environment where there are not several other processes running at...

Demystifying LEAN Subcontracting Setup for Microsoft Dynamics AX 2012- Part One
Introduction The subcontracting process for Microsoft Dynamics® AX 2012 resembles a large body of water that you need to cross....

E-Commerce Defining Its Scope and Risks within Retail Industry
The retail sector has been faced with many challenges in recent years, but a bright spot has emerged within the...

MS Peeking Under the Hood at MRP
Master Scheduling Material Requirement Planning It wasn’t that long ago, that running ‘MRP’ was a process that was done only...

Netsuite Global Search – Tips and Overlooked Features
One of the features many new users overlook in NetSuite is the Global Search. Global Search helps users find information...

Scribe Adapter for Dynamics CRM Connection Error “The authentication endpoint AsymmetricToken was not found on the configured Secure Token Service!”
Let’s say you are migrating from a legacy CRM system to Microsoft Dynamics CRM 2011 Online – Office 365 environment...

Introducing Microsoft SQL Server 2012
Introduction This article describes the exciting new versions and features of the recently released Microsoft SQL Server 2012. Since the...
Integration of CRM with ERP, the Why and ROI
I’ve been fortunate to have worked on the implementation of over 250 CRM systems from several different software publishers over...

Dynamics CRM 2011 Online – Office 365: Internet Explorer Certificate Errors Windows Server 2003
You may notice that there are many articles regarding Certificate Errors in Internet Explorer. Most of what you will find...

Lower TCO, increased functionality prompting migration from Salesforce.com to Microsoft Dynamics CRM
We are seeing a growing trend of organizations migrating from Salesforce.com to Microsoft Dynamics CRM for their customer relationship management...

Creating a Simple Windows 8 App for Dynamics AX
Wouldn’t it be nice to be able to browse your Dynamics AX data directly from Windows 8? In this short...

Comparing NetSuite Kits, Assemblies and Item Groups for Distributors and Manufacturers
NetSuite provides three options for wholesale distribution and manufacturing to track item collections in support of a variety of requirements. So what are they...

4 Steps to Improve Your Metrics in Your NetSuite Warehouse
The challenges facing warehouse managers today are as tough as they have ever been. They include: Supporting the revenue growth...

Infographic: Fuel productivity of customer-facing teams with Microsoft Dynamics CRM
Are you evaluating customer relationship management (CRM) systems? Salesforce.com and Microsoft Dynamics CRM are recognized leaders in the market. This infographic...

Consuming Web Services Using Dynamics AX MorphX
In this article, I will describe a tool and technique to enable Microsoft Dynamics AX 2009 (DAX) to interface with...

Dynamics CRM 2011 Build Unmatch query SSRS report using FetchXML
One of the limitations of the Advanced Find feature of Microsoft Dynamics CRM and by extension, Fetch XML using the...

Microsoft Dynamics CRM 2011 UR12 – Report cannot be displayed
There are many reasons why you might get the “Report cannot be displayed” error message for custom reports and/or out...

Identifying Unused Code
Introduction In the process of implementing and maintaining Microsoft Dynamics® AX, many modifications are created and modified while a portion...

The good, the bad, and the wish list about Microsoft Dynamics CRM 2011 latest Update Rollup 12 (Polaris)
If you are using Microsoft Dynamics CRM 2011 online, you probably noticed there are couple new user interface (UI) forms...

Creating an Application Integration Framework to Microsoft Dynamics AX (DAX) 2012
For anyone that has worked with DAX’s Application Integration Framework (AIF) in previous DAX versions, knows that a typical interface starts...

Dissecting Dynamics AX Role Centers
Wouldn’t it be nice to come into work in the morning, open up Dynamics AX, and see everything that you...

How to increase the use of Microsoft Dynamics CRM in your sales organization
A common problem that confronts users of Microsoft Dynamics CRM, or any other CRM application, is convincing sales people to...

Improved Procurement with Purchase Sales History Analytics
Purchase/Sales History Given the volatility of today’s economic environment, it is imperative for organizations to leverage as much leading edge...

Employee Center User vs. General Access User
With all the roles that can be customized in NetSuite it can be confusing what the differences are between a...

Using Cases to Manage New Product Introduction
Although Dynamics AX is not a completely new product development and formulation system since it does not calculate nutritional details or perform...

RSM’s Dynamics AX Wireless Warehouse Functionality
One of the best ways to manage inventory is through the utilization of handheld bar code reading guns. This not...

Taming Form Parts in AX2012
A form part is a type of fact box that you can insert into a list page form or a...

4 Things to Consider When Getting Started with Social CRM
Social CRM has become a buzzword that many organizations struggle to understand. Is it CRM? Is it a technology? Is...

E-commerce and what the brand experience means for your organization
As the economy continues its uncertain path, businesses across the globe are looking for new ways to drive growth while...

Implementing Dynamics AX 2012 General Ledger Dimensions – Part 4
Part 4 – Account Structures: Implementation Considerations In parts 1-3 of this series, we’ve examined the various decision criteria around...

Using Models to Create Demand Forecasting in Dynamics AX 2012
If you are not the fly-by-the-seat-of-your-pants type that waits for orders to come in before having to figure out how to...
Best Practices for Moving to a Cloud ERP Solution
For organizations thinking about moving to a cloud ERP solution such as NetSuite, here are some best practices to consider when...

Embedding PowerView Dashboards into Role Centers
PowerView is great for creating quick ad-hoc reports, but up until now I have not been able to use...

Integrating a Microsoft Dynamics CRM dashboard into any entity
Recently, one of our clients wanted to see a dashboard added into the Microsoft Dynamics CRM form. For example, they...

Using Enterprise Search to Unite Your Data
The Enterprise Search feature within Dynamics AX 2012 is a great way to find things quickly and...

Master Planning Price Alerts & Quantity Breaks
In an economy where the control of spending is critical to cash flow, having visibility to procurement incentives can...

Free webinar: Social CRM and what you need to consider
The web has drastically changed the landscape of today’s marketing programs and how customers buy from us. Most consumers are...

What is PowerPivot? | PowerPivot 101
Building an SSAS cube isn’t for everyone. PowerPivot is! With PowerPivot, you are able to examine data over time...

Dynamics AX 2012 General Ledger Dimensions Part 3 – Profitability Statements: GL vs. Alternate Systems
So in the last piece we looked at various analyses you could do through dimensions. In this section we’re...

Eventing for Microsoft Dynamics AX 2012
Events are a new concept within the Microsoft Dynamics AX 2012 development environment. The premise is easy, you can...

Retail | Product Information Management Systems (part 1 of 2)
One huge challenge that retailers of complex products face on a day to day basis is how to deal...

NetSuite Manages the Lead to Cash Process for Increased Productivity
Properly managing the lead to cash process can help increase sales productivity. The fully integrated CRM (Customer Relationship Management) and...

Importing Data with Netsuite
Data can be imported into NetSuite from a CSV file, a Quicken file or a QuickBooks file. A NetSuite professional...

Microsoft Dynamics CRM 2011 Jscript Walkthrough : Setting Today’s Date in a DateTime Field
When working with Microsoft Dynamics CRM, there are situations that require validation of data on the forms. One of the more...

NetSuite Enhanced Dashboard Reporting Features Offers Flexibility for Users
NetSuite delivers built-in, real-time financial dashboards tailored to the user. In the 2012.2 release of NetSuite users can experience several...

Using Cases to Track Quality Issues and Complaints
Cases within Dynamics AX 2012 are a great way to track quality issues and complaints throughout the organization. Case management...

Using Multiple Forms
Segregation of duties is a major concern for accounting and finance departments of companies, not only to comply with audit...

NetSuite Saved Searches — Part 1: Data extraction
Have you wondered how you can improve the balance between amount of time spent on preparing and the amount of...

Why Start-ups Choose NetSuite as their Business Systems
One of the most exciting parts of McGladrey’s business is working with startup companies. When a new company asks for...

Five Crucial Tips for Effective Prospect Research
Phone calls are the main interaction platform between customers and businesses. Over 92% of the average customers report that they...
What is your Organization’s Social CRM Strategy?
Wikipedia’s compares Social CRM as “a synonym for Social Media Monitoring, where organisations watch services like Facebook, Twitter and LinkedIn for...

Dynamics AX AOT Search Too Slow for You? Take Advantage of the Cross-Reference Table
Simple, fast, and flexible functionality utilizing Dynamics AX 2012 cross-reference tables. If you have ever had to use the built-in...

Data Migration Framework (DMF) in Microsoft Dynamics
Microsoft Dynamics® AX 2012 has undergone some significant design changes to the application and the table structures. Even though moving...

Microsoft Dynamics CRM Next Major Service Update in December 2012
If you are using Microsoft Dynamics CRM online, then the upcoming month of December will make your CRM investment much...

Sales Order Template Generation
Easy to setup, administer, and control the specific templates that allow for improved order entry The Sales Order Template Generation...

Outlook Categories and their Integration with Microsoft Dynamics CRM
Microsoft Outlooktasks and Microsoft Dynamics CRM activities both have Categories so if you set this in Dynamics CRM and sync...

Implementing Dynamics AX 2012 General Ledger Dimensions- Part 2 Implementation Considerations
Part 2 – Implementation Considerations In the first segment of this series we looked at traditional segmented general ledgers vs....

Implementing Dynamics AX 2012 General Ledger Dimensions
One of the strongest new features in Dynamics AX 2012 is the Dimensions in the General Ledger (GL) module. This four-part...

Upgrade Strategies | Financial Data Reporting
Often times a company’s incentive to upgrade their Dynamics AX installation comes with a need to reorganize their organizational structure....

Should I Fire My ERP Implementation Firm?
Much has been written about the many failures of ERP over the years. We read that the many causes are...

The 5 Benefits for Construction Companies Using CRM
Traditionally, construction firms have used disparate data bases like Microsoft Outlook or Excel that collect data on projects or customers. CRM...

Microsoft Dynamics CRM 2011 Jscript Walkthrough: Setting Up Look-Up Fields, Part I
I think one of the more common questions I receive when working with Jscript in Microsoft Dynamics CRM is, how...

Part III Financial Dimensions: Segmented Entry Control
Next up is the segmented entry control. In earlier releases, the financial dimensions were displayed as separate fields and were...

Creating Automatic Email Confirmations From Dynamics AX
Automating email communication and email confirmations is a great way to streamline your business process. An example of achieving this is to send...

System vs. Custom Dimensions- Part II Financial Dimensions
5 – System vs. Custom Dimensions As stated in the first part of my blog, a system-defined dimension allows you to...

Top Three Reasons ERP Projects Fail
For some of you out there, reoccurring childhood nightmares were replaced at some point in your life by a horror that...

Getting Started with Javascript Form Scripting for Microsoft Dynamics CRM 2011
With the flexibility of Microsoft Dynamics CRM 2011, there are many options for enhancing the product such as data validation,...

5 Cool New Ways to Use Financial Dimensions in Microsoft Dynamics AX 2012
Financial Dimensions With the complete redesign of the financial dimensions and chart of account structure in Microsoft Dynamics® AX...

Installing the Outlook client for Microsoft Dynamics CRM – Office 365 Subscriptions
I am posting this article as a response to the video tutorial, Installing and Configuring the Outlook client for Microsoft Dynamics...

Migrating Outlook Data Files to Microsoft Dynamics CRM
I have recently been involved in an enterprise implementation of Microsoft Dynamics CRM for one of our manufacturing and wholesale...

Working with Microsoft Dynamics CRM Users in Office 365
With the release of Office 365, there is a new process for adding users to your Microsoft Dynamic CRM Online....

Overlooked Microsoft Dynamics CRM Performance Tweaks – Part 2: Design Improvements
In my last blog I went over how some basic settings in Windows can affect the performance of Microsoft Dynamics...

Introducing the Security Development Tool in Microsoft Dynamics® AX 2012
Security Development Tool The Security Development Tool for Microsoft Dynamics AX2012 is a fast-track method for maintaining roles, duties, privileges,...

Setting Field Security Profile in Microsoft Dynamics CRM 2011 Without Coding
Field Security Profile is a new functionality in Microsoft Dynamics CRM 2011 that helps organization control access to a specific...

Using Requests for Quotation to Automate Vendor Management and Bidding
The Vendor Portal is a great tool that allows you to streamline purchasing processes, and also get the vendor to...

Inventory License Plating – New System Dimension Streamlines Warehouse Operations for Food Industry
Inventory License Plating Powerful, agile, and flexible functionality utilizing a new system dimension to streamline Microsoft Dynamics AX and Wireless...

Training Your Super Users: 5 Important Things to Keep in Mind
So you’ve just selected an ERP system and your company is gearing up for a full-scale implementation. Amidst the flurry...

Microsoft Dynamics CRM 2011 Online with Office 365 – Plug-In Registration and Scribe Adapter – an unsecured or incorrectly secured fault was received – Solved
Microsoft is now moving the 30 day trial versions of Microsoft Dynamics CRM 2011 Online to its Office 365 platform. ...

What’s Up With The Microsoft Office Add-Ins?
Microsoft Office Add-Ins In the past few months, I have been asked countless questions about the new Microsoft Office Add-Ins...

Creating Statements in Dynamics AX 2012 Retail
This post will focus on a functional portion of Dynamics AX 2012 Retail. This week I was working on some customization...

Using Application Triggers in AX 2012 POS Development
This is one in a series of posts related to the Microsoft Dynamics AX 2012 POS application. There is a lot...

Microsoft Dynamic CRM – Assigning Forms to Security Roles
Microsoft Dynamic CRM has an excellent solution for organizations wanting specialized forms to be viewed by teams or business units...

Microsoft Dynamics CRM 2011 Performance Tuning – Part 2
In part 1 of my performance tuning series, I talked about the purpose of the series and covered a couple...

Working with the AX 2012 EDT Relation Migration Tool
This week I was faced with a couple of problems related to the relationships between tables made under an Extended...

Introduction to Programming for Performance in Microsoft Dynamics AX
Microsoft Dynamics AX Programming Tips The performance of an enterprise application is a key factor in how users perceive that...

Microsoft Dynamics CRM 2011: 5 Steps to Reports in Dashboards
Dashboards in Microsoft Dynamics CRM 2011 are a very powerful tool. One which allows users a plethora of information in...

Introducing the New Inventory Value Report in Microsoft Dynamics® AX 2012
Goodbye PIBIG report and Hello Inventory Value report! I am sure many of you have struggled at least once or...

From the CTO: Microsoft Dynamics AX |Synergize Your Desktop
Often when I’m out visiting customers or prospects, we’ll get bogged down on a singular feature or function, and lose...

Bringing the Power of Data Mining to the Mid-Market
Data mining has been around for years, but has yet to really take hold in the mid-market. Instead it has...

AX 2012 for Retail – An Introduction to Application Settings
This post is about using the AX 2012 for Retail Application Settings. This is a dll that exists within the AX...

Improving Productivity with Enterprise Search
Claire, the Accounts Payable Clerk, is entering invoices when her phone rings. She thinks to herself, “I cannot get anything...

Microsoft Dynamics CRM 2011 Dashboard Tip
Microsoft Dynamics CRM 2011 offers up wonderful functionality to build dashboards providing a wealth of information at a glance. Dashboards...

Overlooked Microsoft Dynamics CRM Performance Tweaks
For all of us that use Microsoft Dynamics CRM on a daily basis, we have at some point or another...

Importing Zip Codes into Dynamics AX
Today I would like to discuss importing Zip Codes into Dynamics AX 2012 from a Text file and also point...

Increasing Organizational Productivity with Dynamics CRM
Today’s business climate is extremely lean given the economy of the last few years. Organizations have cut back on people...
The Effects of Poor Customer Service and How a CRM Solution Can Help
“It doesn’t take a lot of poor customer service for a customer to start looking for a replacement.” That message...

Microsoft Dynamics CRM for Outlook Configuration Troubleshooting Wizard
One of our leading Microsoft Dynamics CRM consultant Sarah Champs posted a great article about installing and Configuring the Outlook...

Dynamics CRM 2011 Performance Tuning – Part 1
Like many of you, I’ve spent quite a bit of time going through the performance tuning documents which Microsoft and...

Free Trial of Microsoft Dynamics CRM
Is your organization looking for a more mature Customer Relationship Management (CRM) system? Whether your needs are basic, out of...

Microsoft Dynamics CRM 2011 Update Rollup 10 has been released
Want to keep current with the most recent hot fixes and functionality in Microsoft Dynamics CRM 2011? Update rollup 10...

Marketing Automation Really Extends your Microsoft Dynamics CRM Investment
I am surprised how many Microsoft Dynamics CRM customers don’t use any marketing automation software. When our clients see how...

Microsoft Dynamics CRM Accelerator Spotlight: SharePoint Authentication Accelerator for Microsoft Dynamics CRM
McGladrey’s status as a Microsoft Partner with a Gold Customer Relationship Management (CRM) Competency means that we have demonstrated our ability...

Case Study: Non-Profit Organization Selects Microsoft Dynamics CRM as Tool for Grant Management
The Arc of Dauphin and Lebanon Counties (The Arc) is a non-profit, membership organization serving approximately 800 members using a...

“Nothing Happens Until Someone Sells Something”
I like this quote (author unknown) because it is an action statement and a challenge. All successful businesses depend on sales…...

Microsoft Dynamics CRM 2011 Custom Code Validation Tool Released
In preparation for Microsoft Dynamics CRM Q4 2012 Service Update to support various web browsers. Microsoft has released a tool...

Extend Microsoft Dynamics CRM: Changing a Form to Read-Only
There are various methods of modifying the rights to forms in Microsoft Dynamics CRM. In a two part series, we outline first how...

Microsoft Has Updated the CRM 2011 Client Performance Optimization Document
I was browsing around the Dynamics CRM 2011 Support Page and noticed the Optimizing Client Performance document had been updated...

Installing and Configuring the Outlook client for Microsoft Dynamics CRM for Optimal Performance
Need help installing the Microsoft Dynamics CRM Outlook Client? If you have already installed the client, are you experiencing performance issues within...

It’s 8 AM… do you know where your customers are?
Many years ago, I recall seeing a TV commercial directed at parents. The commercial stated “It’s 8 PM… do you...

Microsoft Dynamics CRM 2011 Report Displayed Error
Recently, I have ran into a Reporting issue in Microsoft Dynamics CRM for one of my client. He was not...

Complimentary Dynamics CRM webcast: Social Intelligence
Join RSM on Tuesday, July 10, 2012, 12 p.m. EST/11 a.m. CST for a complimentary webcast with ISV guest, InsideView. ...
CRM 2011 UR9 Q2 Service Update Release date guess
The latest release date that I’ve seen for Microsoft Dynamics CRM Q2 is July 19th. I’m sure we’ll all find out...

Installing, Configuring, Optimizing and troubleshooting Dynamics CRM for Outlook – Video
I know the title of this blog article is a mouthful and how could I possibly provide all these things....

Service Scheduling in Microsoft Dynamics CRM 2011
Out of the box Microsoft Dynamics CRM doesn’t provide much around service scheduling, therefore if your organization plans to use...

Dashboarding in Microsoft Dynamics CRM 2011
Not only do many charts come out of the box with Microsoft Dynamics CRM, but users can also create their...

12 Great reasons why companies use Microsoft Dynamics CRM, plus a little rant…
I saw this great graphic (below) on the Microsoft blog site today and wanted to share. This graphic reminded me...

Extend your Microsoft Dynamics CRM solution with RSM Accelerators
Accelerators are packaged configurations built for a particular function or an industry. They are designed to get organizations up and...

Case Study: Not-for-profit automates sales and marketing departments with implementation of Microsoft Dynamics CRM
Pennsylvania based ECRI Institute chose Microsoft Dynamics CRM to centralize their data and automate their business process. Equally important to the...

MSCRMAsyncService Errors in the Event Log of Microsoft Dynamics CRM
In continuing with my earlier post, I’m going to keep working on adding various performance tips and tricks as they...

MSCRMPlatform Warning in Event Viewer in Microsoft Dynamics CRM – Event ID 17972
This is one of those warnings you or your clients may notice in their event viewer from time to time...

Migration of data from SalesForce
I have done quite a few migrations to Dynamics CRM and some of the most difficult ones have to deal...

Dynamics CRM 2011 Audit User Logon
I had a client asked me today if they could audit the user logon. I found this on the Microsoft...

Scribe Console Connection Troubleshooting
Many companies looking to integrate with Microsoft Dynamics CRM turn to Scribe Software, data migration and integration solutions for Microsoft Dynamics. As a Scribe...

Dynamics CRM 2011 Javascript ZipCode/Postal Code Lookup
Recently, I needed to write some javascript to do a zip code/postal code lookup for validation purposes and it also...

Update existing CRM data using Export to Excel and Import Wizard
A lot of my clients want to pull data into CRM from other sources without having to buy a third...

Dynamics CRM 2011 Advanced Find Video
I’m sure you can find other ones out there, but I think the one we’ve done here is one of...

2012 Emerging Technology Conference
Please join us for our annual Technology Conference. I will be attending our event in Denver on March 6th, so...

Dynamics CRM 2011 Customer Portal – Contact Us and Event Registration not saving – Resolution
I’ve been demoing and implementing the Customer Portal for Dynamics CRM 2011 A LOT lately. The latest “free” version that...

CRM User Adoption
A few years ago, I performed a CRM assessment for a company that was using Dynamics CRM 4.0 (implemented by...

Why Choose Microsoft Dynamics CRM over Salesforce.com
Below is a recent article on win for Microsoft Dynamics CRM over Salesforce and Oracle. In my world, this is...

Microsoft Dynamics CRM 2011 R8 – Unbelievable (and finally)
I just saw the Partner Briefing on Microsoft Dynamics CRM 2011 R8 release scheduled for Q2 release and all I...

Integrating “National Accounts” in Microsoft Dynamics GP and Microsoft Dynamics CRM using Scribe
While integrating Microsoft Dynamics CRM and Microsoft Dynamics GP, I ran into a situation where I needed to: Be able...

Microsoft Dynamics CRM 2011 Developer Toolkit
Microsoft Recently released the Developer Toolkit for Microsoft Dynamics CRM 2011. The toolkit integrates with Visual Studio 2010 and installs...

Practical considerations to integrating the Dynamics CRM Outlook Client and SharePoint Document Management Integration
The native SharePoint integration into Microsoft Dynamics CRM has caused a lot of excitement over the last few months. The...

Microsoft Dynamics CRM 2011 – Activity Sub-grids only display regarded records
As promised, we will continue to post articles of known issues with Microsoft Dynamics CRM 2011 and this is a...

Microsoft Dynamics CRM 2011 – Javascript to display associated views
This post is a companion post of Microsoft Dynamics CRM 2011 – Activity Sub-grids only display regarded records, which details...

Microsoft Dynamics CRM 2011 – Improved Data Import Wizard
Anyone who has experienced the import capabilities of Microsoft Dynamics CRM prior to the latest release (2011) will undoubtedly agree...

Script Errors in Microsoft Dynamics CRM 2011 – CRM Presence – Known Issues
RSM recently had an issue with all users on a particular environment receiving Internet Explorer script errors in the Microsoft...

Queues in Microsoft Dynamics CRM 2011 – Queues: Team Ownership
In Microsoft Dynamics CRM 2011, you now have the ability to create Queues and Queue Items for almost any entity....

Advanced Find, Dashboards and Reports Webinar
RSM recently held a Webinar on Dynamics CRM Advanced Find, Dashboards and Reports. You can find the recording and presentation...

Microsoft Dynamics CRM 2011 – Add picture to contact/lead forms using SRS report
Recently, I needed to display existing pictures (and provide the ability in Microsoft Dynamics CRM to add additional ones) for contacts...

Microsoft Dynamics CRM 2011 Mobile Express
With the ability to publish custom entities to the mobile express in Microsoft Dynamics CRM 2011, we have done a little...

CRM 2011 Javascript hide/show sections based on picklist
The following is a script for Microsoft Dynamics CRM will show and hide sections based on picklist value: function HideShowHardwareRoles() {...

 RSMUS.com
RSMUS.com